Non-human identities run the work your customers never see. They pull secrets, assume roles, sign tokens, talk to APIs, and move data at machine speed. When they sprawl, incidents do not look like zero-day issues. They look like normal operations until a service quietly writes to production or a token with admin scope leaks from a build system. You do not need a theatre. You need a program that starts by seeing reality and ends with verified fixes that stick.
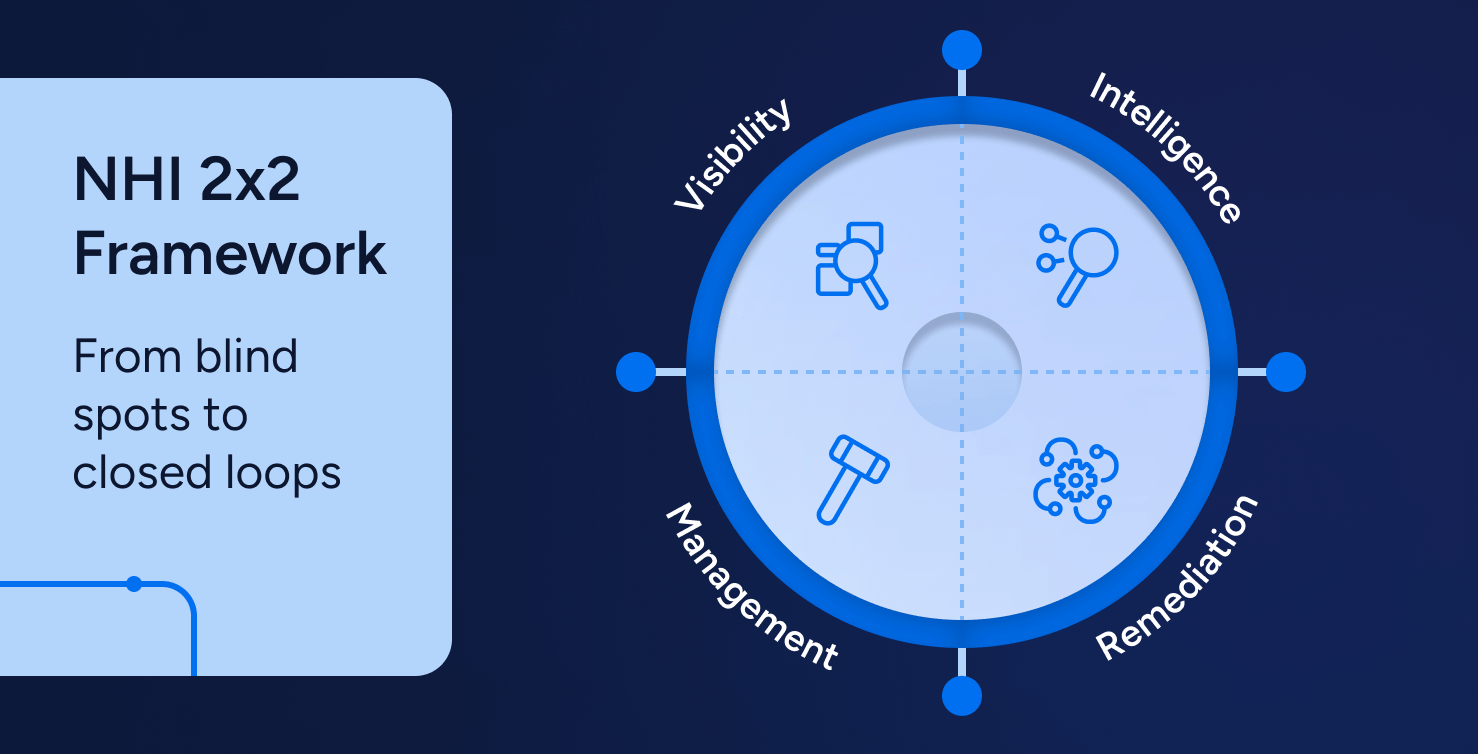
That program is the NHI 2×2. On the horizontal axis sit four motions every mature program cycles through: Visibility, Intelligence, Management, and Remediation. On the vertical axis are the things your teams touch every week: service accounts, service principals, certificates, and API tokens. The point is not a diagram. The point is to run left to right for each vector without breaking builds or trust.
The backbone is simple. Reduce every conversation to who can take what action on what data, and keep that answer current across cloud, SaaS, data, and on-prem. In practice, that shows up in the surfaces engineers actually use, like Access Intelligence for ranking work and Access Search for quick answers without spelunking.
The X axis, in the language of operators
Visibility is a normalized view of non-human identities and their effective permissions. Not a list of role names. A resolved picture of owners, last used, reachable data, and change rights. Intelligence takes that picture and ranks work by blast radius and data sensitivity. This is where teams stop debating and start queuing fixes, because effective access accounts for inheritance, nested groups, OAuth scopes, and indirect data paths that the role listing never shows. When you need a strategic frame for why this layer is rising on roadmaps, the industry’s 2025 take on Identity Visibility and Intelligence Platforms matches what operators already do here.
Management turns intent into defaults. New NHIs should start life as the least privileged possible. Patterns help. Teams standardize creation and scoping with owner assignment and TTLs baked in; when elevation is necessary, they make it visible and governable at the point of change with Privileged Access Assurance.
Remediation closes the loop and proves it. Retire, downgrade, revoke, rotate, and verify with continuous evidence so risk stays down instead of snapping back after audits. That feedback loop is what Activity Monitoring supplies in practice, showing risky paths shrink and stay small.
The Y axis, where pain actually lives
Service accounts are born fast and die slow. You inherit interactive logons that should never happen, legacy group memberships that create write paths into production, and dormant identities with an outsized blast radius. The fix looks like this in real life: resolve the set across identity providers, operating systems, databases, and SaaS; attach owners and environments; calculate effective permissions to sensitive data; standardize creation with owner, purpose, TTL, rotation policy, and environment tags. Let automation retire dormant accounts, prune unused memberships, and break privileged paths. If your team needs field-tested habits for making ownership stick, this guide on NHI ownership and security hygiene covers the patterns that keep drift down without adding friction.
Service principals grow by consent. App registrations collect secrets and certs. Scopes drift from temporary to forgotten. Cross-tenant paths multiply. Start with a catalog of registrations, bindings, secrets, certs, and every consent, including who can grant as well as who has already granted those permissions. Use intelligence to flag wildcard scopes, unmanaged cross-tenant access, and principals that can modify your identity provider or production resource groups. Enforce approvals for high-risk scopes, require an expiration on secrets and certs, and remediate with scope reduction, consent revocation, scheduled rotation, and confirmation that downstream access actually changed. If you need a broader playbook that ties this to non-human identity breadth, the deep dive on governing 90-plus NHIs aligns with these moves.
Certificates look tidy until you map algorithms, SAN reuse, and which identities can impersonate critical services. Visibility means issuers, key length, SANs, and expirations across meshes, gateways, app registrations, and data platforms. Intelligence isolates weak crypto and high-risk impersonation paths. Management enforces auto-renewal and issuance approvals, binding certs to least privileged identities. Remediation rotates before breach, revokes on compromise, and validates traffic cutover and mutual TLS instead of assuming it. To keep leaders aligned with why this matters now, the perspective in Gartner’s Hype Cycle for Digital Identity calls out the rise of visibility plus control as a single motion.
API tokens are the quiet crown jewels. They sit in CI/CD Pipelines, chatbots, data tools, vendor portals, and automation frameworks. Their last used status is unclear. Scopes are overbroad by design. A single token writes to PII tables from a shared workspace no one directly owns. Visibility is a real catalog with owners and the last used. Intelligence highlights admin scopes, cross-environment use, and reachable sensitive data. Management enforces TTLs, naming and tagging conventions, and least privilege scope bundles. Remediation supplies kill switches for leaks or overbroad tokens, rotates keys on schedule, and backs it with conditional access so one mistake does not become an outage. For a broader lens on posture that includes tokens as first-class citizens, the explainer on Identity Security Posture Management connects continuous governance with day-to-day engineering work.
Why does this belong in one operating loop?
Every row can run left to right the same way. Connect systems once. Ask questions once. Enforce outcomes everywhere. Measure reduction and keep moving. That is how you ship fixes without fire drills and give auditors evidence without archaeology.
Veza is built to run this loop on real and often messy estates. The graph supplies the shared truth across systems, the signal is prioritized where work actually happens, and guardrails make elevation and approvals predictable. Closure comes from remediation and access reviews executed by Veza Actions, translating effective permissions and ownership into concrete changes in the systems of record, scope downgrades, consent revocations, retiring dormant service accounts, and rotation triggers, with outcomes verified before the next sprint.
NHI 2×2 at a glance
Here is how the loop plays out for each vector, left to right. Use it as a bridge from story to action.
| NHI vector | Visibility | Intelligence | Management | Remediation |
|---|---|---|---|---|
| Service accounts | Inventory across IdPs, operating systems, databases, and SaaS; owners and environments attached; effective permissions resolved. | Rank by blast radius to production; flag interactive logons and dormant high privilege identities. | Standardize creation with owner, purpose, TTL, rotation policy, and environment tags; enforce least privilege templates. | Auto retire dormant accounts; prune unused memberships; break write paths to sensitive data; verify outcomes. |
| Service principals | Catalog app registrations, secrets, certificates, role bindings, and consents; track who can grant and who did. | Approvals for high-risk scopes; mandatory expirations for secrets and certificates; default to least privileged app roles. | Detect weak cryptography, SAN reuse, and certificates that enable the impersonation of critical services. | Downgrade scopes; revoke stale consents; rotate on schedule; confirm downstream access changes. |
| Certificates | Inventory issuers, algorithms, key length, SANs, and expirations across meshes, gateways, app registrations, and data platforms. | Auto-renew policies; issuance approvals; bind certificates to least privileged identities; enforce mutual TLS where required. | Highlight admin scopes, cross-environment use, reachable PII, and change rights. | Rotate before policy breach; revoke on compromise; validate traffic cutover and mutual TLS. |
| API tokens | Kill switches for leaks or overbroad tokens; rotate keys; backstop with conditional access; measure reduction of long-lived tokens. | Catalog across CI, secrets managers, SaaS portals, data tools, and automations; owner and last used are tracked. | Enforce TTLs, naming and tagging conventions, and least privilege scope bundles; require purpose and owner. | Kill switches for leaks or overbroad tokens; rotate keys; backstop with conditional access; measure reduction of long lived tokens. |
Getting started without breaking builds
Week one connects sources and tags owners. Week two turns inventory into a signal with effective permissions and data sensitivity. Week three sets guardrails so new non-human identities start life least privileged. Week four automates the top three high-value fixes in your environment and proves the impact with trend metrics. Then you loop.
Keep the momentum with the right assets
Teams that standardize this loop across service accounts, principals, certs, and tokens usually keep one reference close. The Non-Human Identity datasheet maps lifecycle stages to specific controls and measurable outcomes you can baseline against. When you want to see your own graph and walk a painful workflow end-to-end, a working session with the product team is the shortest path. Start by requesting a demo.






