Executive Summary
Service accounts, workload identities, tokens, client secrets, bots, and agentic AI now outnumber humans and carry powerful permissions. Veza’s NHI Security discovers these identities, maps ownership, calculates effective permissions, hardens credentials, and automates least privilege without breaking production. When an identity is abused, your SOC gets authorization truth to detect, scope, and contain fast.
What Counts as a Non-Human Identity
Non-human identities include OS-level service accounts, cloud roles and workload identities, application registrations and service principals, API keys and tokens, CI/CD bots, robotic process automations, and headless SaaS users. For a concise primer your team can pass around, the explainer What are Non-Human Identities? covers definitions and failure modes.
Why NHI Security Matters Now
Keys and tokens propagate through pipelines and containers. Orphaned machine accounts retain standing privilege. Traditional IAM and MFA center on people, not machine access paths. For practical pitfalls and day-one remediations, see the field guide Non-Human Identity Security: A Practical Guide to Mitigating Risk.
The Veza Approach
Veza treats machine access as a graph problem. The platform normalizes identities, roles, groups, policies, ACLs, and data objects across directories, clouds, SaaS, and databases to compute effective permissions that engineers can read and auditors can defend. If stakeholders want a one-minute mental model, the video Who can take what action on what data frames the approach succinctly.
End-to-End NHI Lifecycle With Veza
Frameworks That Guide NHI Security
IVIP, Identity Visibility and Intelligence Platform
IVIP centers on unified discovery, normalized authorization data, and analytics across identities and entitlements. For NHI security, that means putting effective permissions at the core. Leadership can align quickly using the analyst perspective in IAM is blind, IVIP can see.ISPM, Identity Security Posture Management
ISPM operationalizes identity risk reduction for humans and machines. It catches drift, wildcard roles, long-lived credentials, and toxic combinations before they become incidents. External validation of the space is summarized in the GigaOm Radar for ISPM.ITDR, Identity Threat Detection and Response
ITDR focuses on detecting identity abuse, scoping blast radius, and containing quickly. Veza detects with rules and activity signals, triages with effective-permission context, and contains risk by revoking standing privileges through governance workflows. If your SOC pairs identity and endpoint telemetry, the integration overview Veza + CrowdStrike shows how the pieces fit.
Capability Map
| Capability | NHI Need | Framework Alignment | How Veza Delivers (NHI-specific) |
|---|---|---|---|
| Discovery & normalization | Enumerate NHIs across directories, cloud, SaaS, CI/CD, data; classify types; assign owners | IVIP (primary), ISPM | Connectors + Access Graph normalize machine identities; classification (service accounts, workload roles, app registrations, tokens); ownership inference from creators/approvers/usage. |
| Authorization intelligence | See effective permissions (who/what can do which action on which resource) | IVIP (primary) | Graph-based resolution of roles, groups, policies, ACLs → human-readable actions on concrete resources; path analysis to sensitive data and change functions. |
| Credential hygiene & secrets posture | Identify long-lived keys, unused tokens, hard-coded credentials; enforce rotation | ISPM (primary), IVIP | Inventory tokens/keys with age & usage; unused scope detection; policy checks to shift to short-lived, scoped credentials and vault patterns. |
| Ownership & accountability | Make one accountable owner per NHI (plus backup) to close the “no one owns it” gap | ISPM, IVIP | Owner suggestions from metadata and activity; owner assignment workflows; accountability surfaced in reviews and dashboards. |
| Least-privilege design (Access Profiles) | Define minimum viable permissions per NHI/job without breaking production | ISPM (primary) | Access Profiles derived from usage & intent; impact simulation before change; templated profiles for repeatability. |
| Governance & certifications | Approve, attest, or revoke NHI access with evidence | ISPM (primary) | Owner-centric Access Reviews; micro-certifications for high-risk NHIs; change tickets and approvals captured for audit. |
| Continuous assurance & drift detection | Detect privilege creep, policy changes, SoD violations | ISPM (primary), ITDR (secondary) | Activity-aware drift alerts; SoD policy checks for NHIs (e.g., deploy + approve release); scorecards to track posture over time. |
| Blast-radius & access-path analysis | Quantify what a compromised NHI can touch right now | IVIP (primary), ITDR | Real-time effective-permission and resource reachability views; “crown-jewel” proximity and toxic combo analytics. |
| Signals, anomalies & escalation | Spot suspicious spikes, new privileged scopes, or orphaned NHIs becoming active | ITDR (primary), ISPM | Rules & activity signals on escalation, new admin grants, inactive-but-credentialed identities; prioritized alerting by impact. |
| Containment & response | Remove only the risky entitlements fast; preserve uptime and evidence | ITDR (primary) | Targeted revocation using Access Reviews/Actions; rollback paths; audit trail; optional enrichment with EDR/endpoint telemetry. |
| Program analytics & KPIs | Prove reduction in standing privilege and mean-time-to-remediate | ISPM (primary) | Trends on NHIs with owners, wildcard/admin reduction, key age mix, unused entitlements removed, MTTR for identity risks. |
NHI Use Cases You Can Run Now
Service account right-sizing removes wildcards while preserving function, with approvals routed in Access Reviews.
Secrets hygiene and rotation identifies long-lived keys and unused scopes, then enforces vault-issued, time-bound credentials while signals flow into Activity Monitoring.
Agentic AI guardrails catalog agents, limit actions to defined datasets, and hunt for drift using Access Intelligence.
Reference Architecture
Ingest and normalize identities, roles, groups, policies, ACLs, and data objects. Analyze and prioritize with action-level visibility, then automate and enforce least privilege with approvals and evidence. For rollout patterns and JIT principles that keep least privilege usable, see Intelligent Access: Modernizing Identity with Just-in-Time Access.
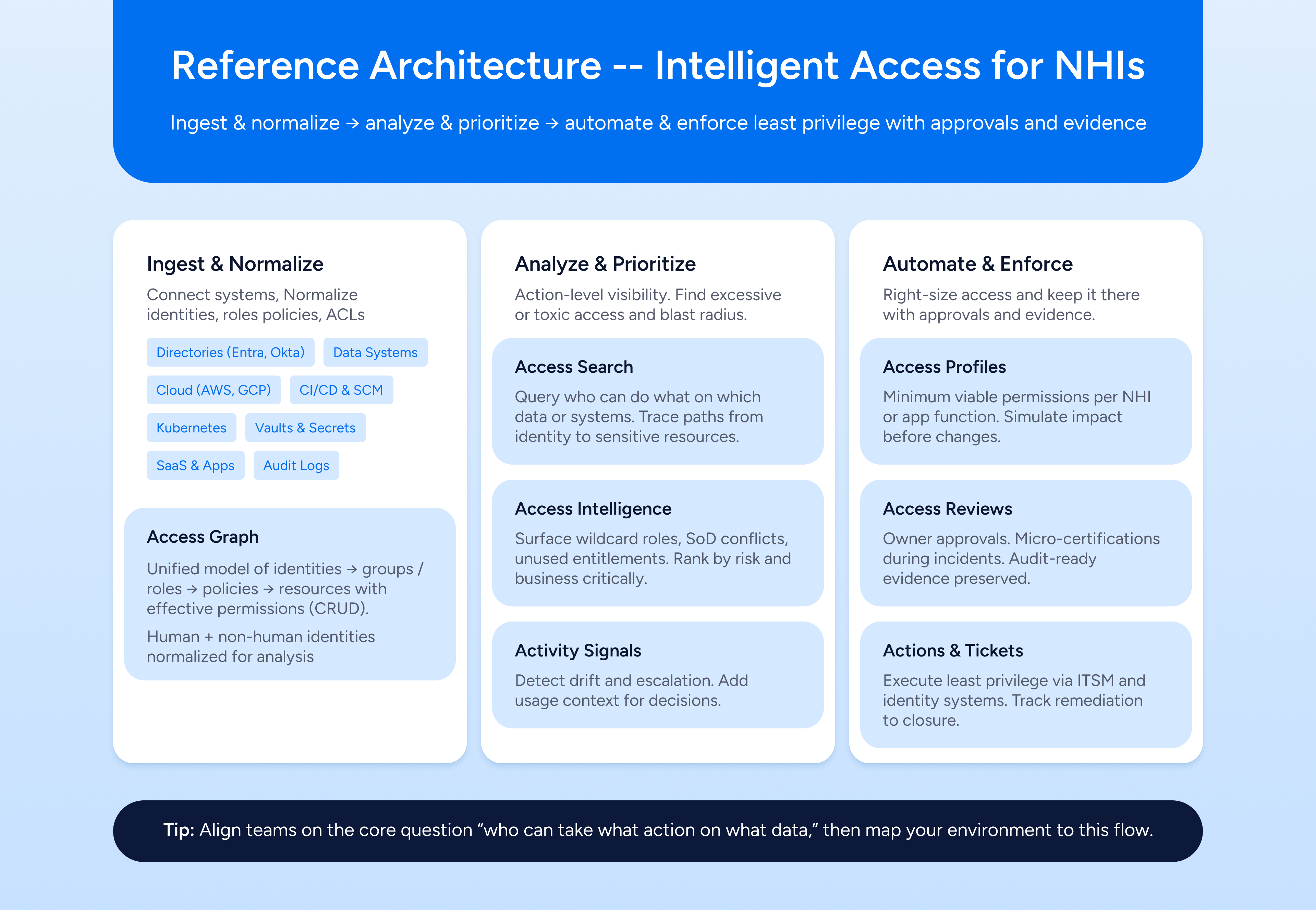
Typical Phased Rollout
First 30 days. Connect core identity, cloud, SaaS, and data systems. Baseline NHI inventory and ownership. Ship a fix list for orphans, wildcards, and long-lived keys.
60 days. Build Access Profiles for top apps and workloads. Run owner-centric certifications in Access Reviews. Remove unused permissions and collapse duplicate roles.
90 days and ongoing. Enforce rotation and short-lived credentials. Expand SoD detection and guardrails for NHIs. Monitor drift and maintain least privilege as code and teams change.
Conclusion
Machine access sits on your critical path now. NHI security isn’t counting identities; it’s knowing exactly what each one can do, who owns it, and how to right-size access without breaking production. Veza turns that into an operating rhythm—discover, understand, fix, and prove—so least privilege becomes muscle memory. Anchor visibility with IVIP, keep posture tight with ISPM, and use ITDR to contain abuse fast. When this clicks, you’ll see fewer wildcards, faster remediation, cleaner audits—and steadier releases.


