Executive summary
Security Operations live and die by time. Alerts are cheap, containment is hard. Veza turns identity security from a static spreadsheet into an operational system of record. The Access Graph gives ground truth of who can do what to which data, Access AI and the Veza Query Language (VQL) make it interrogable in seconds, and Actions drives safe changes through the tools your team already uses. Start with the Access Graph overview to see how intelligent access is modeled end to end: Access Graph.
Why this matters now
Identity is the control plane. Breaches are decided by effective permissions, not just by login events. The latest industry breach analysis shows credentials and misuse still dominate outcomes. See the data in the Verizon DBIR 2025.
Non-human identities changed the math. Service accounts, tokens, bots, and workloads now dwarf human users in many estates. That swell increases blast radius if left over-privileged. Independent research summarizes the growth and risk profile in the CyberArk machine identity analysis.
Zero Trust means least privilege with receipts. CISA’s guidance highlights granular authorization and continuous verification as the path forward. Review the high-level expectations in the Zero Trust Maturity Model.
Where ISPM and IVIP fit. Identity Security Posture Management focuses on continuously finding and fixing toxic access while proving control to auditors. Read the overview at ISPM. Identity Visibility and Intelligence Platform provides the unified visibility and analytics layer that SOCs need to reason over effective permissions and take action. See the resource at IVIP. Veza’s SecOps motion is the execution layer for those principles: observe with a graph, decide with queries, and act through your ITSM, SOAR, and IdP.
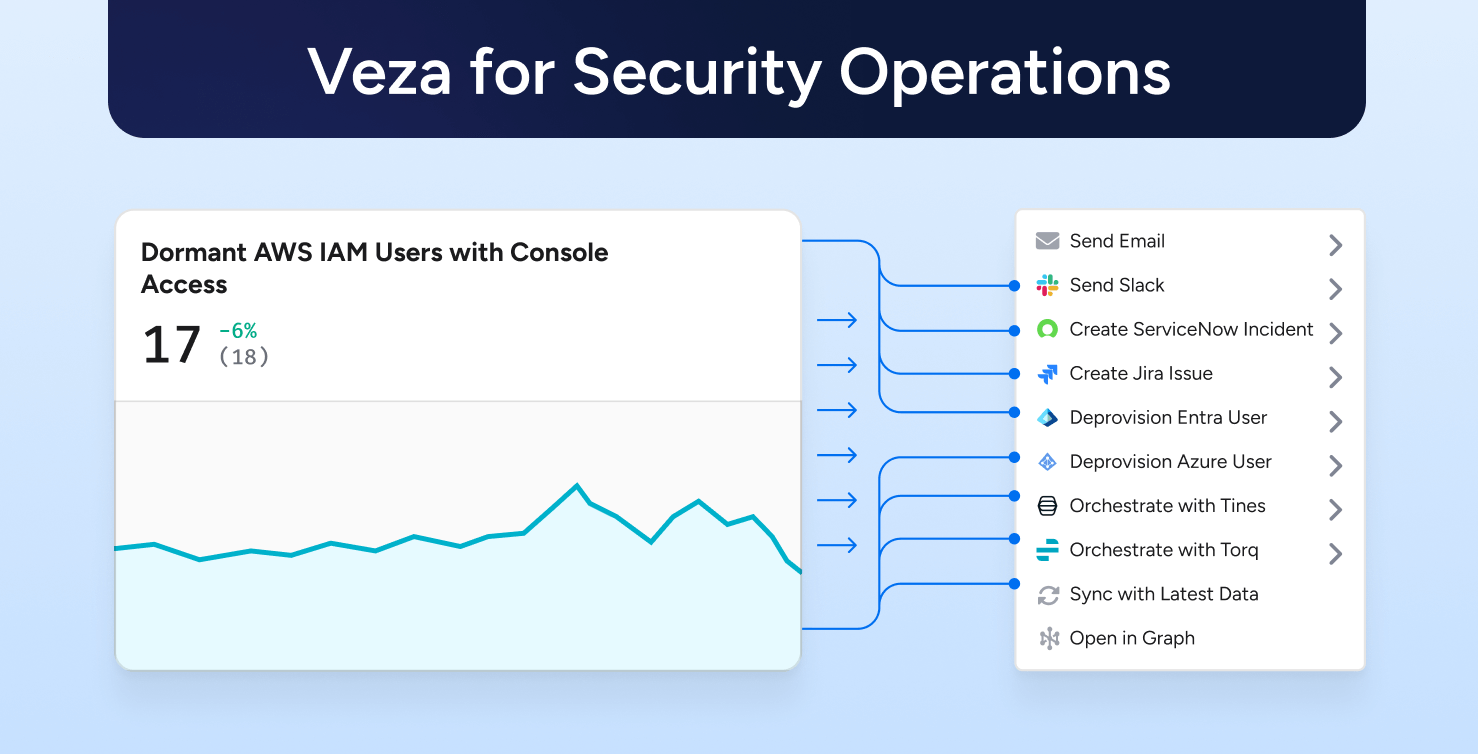
What “Veza for Security Operations” means
Veza makes identity security operational for the SOC by pairing a universal permissions model with safe automation. Access AI accelerates investigations with natural language, while the Veza Query Language (VQL) provides surgical precision for hunts and forensics. Explore the analyst experience with Access AI and the query power of VQL.
How the tooling works
1) Access Graph is your ground truth
Veza ingests identities, groups, roles, policies, ACLs, and resource metadata, then resolves them to effective permissions expressed in CRUD terms. That single source of truth becomes the substrate for triage, containment, and post-incident hardening.
2) Interrogate with Access AI and VQL
Start with natural language, then pivot to VQL when you need path-aware queries across identities, roles, policies, and resources. Typical questions include who has delete on a Snowflake finance schema, including inherited rights, and which service accounts have programmatic access to production S3 buckets with recent use.
3) Take action through your stack
Security Operations is a team sport, and Veza integrates with the tools you live in, so containment is precise and auditable. Pair EDR and ITDR risk with authorization truth using the CrowdStrike integration. Align authentication context with effective permissions via Okta: route approvals and changes through ServiceNow, Jira, and Slack. Enforce least privilege where the data lives on AWS and Snowflake.
SecOps playbooks
Compromised identity containment:
Input: EDR flags a high-risk user or service account.
- Step 1: Map effective permissions and sensitive objects in scope.
- Step 2: Scope or revoke access and create a change with approvals in your ITSM.
- Step 3: Notify the owner in chat-ops and attach evidence to the incident record.
Output: least-privilege state enforced with documented approvals. For background on identity-led threat activity and containment pressure, see the CrowdStrike Global Threat Report 2025 and the ransomware patterns called out in the ThreatDown State of Ransomware 2025.
Privilege blast radius analysis
Query for identities with powerful rights on critical data, return graph paths and accounts, apply least-privilege changes with approvals, and capture the audit trail. If you are formalizing ITDR, a neutral overview of objectives and outcomes is summarized in the BeyondTrust ITDR explainer. For a deeper identity-centric lens on ransomware containment and posture, see Veza’s perspective in Identity, Ransomware, and ISPM.
Non-human identity exposure cleanup
Discover orphaned service accounts and long-lived tokens, correlate to data impact, de-scope, rotate credentials, attest ownership, and track NHI hygiene so drift does not return.
Operator experience
Start in Access AI for quick answers, pivot to VQL for path-level precision. Results include lineage and rationale so you can trust the decision. Actions packages change with approvals, guardrails, and evidence, which empowers junior analysts and keeps seniors in control.
Proof and measurables
Track identity security as an operational program with clear, defensible metrics. Time to Know means minutes from alert to blast radius map, target trend down and to the right. Time to Contain means minutes from decision to enforced least privilege, target trend down and to the right. Entitlement Reduction means high-risk rights removed per month, target trend up and to the right. NHI Hygiene means NHIs with scoped access, recent use, and named owner, target trend up and to the right.
Getting started
- Explore Veza Actions to see how change is operationalized across ITSM, SOAR, and ChatOps.
- Browse the integrations catalog and plan onboarding.
- Understand how Veza’s Open Authorization Architecture scales clean application onboarding.
- When you are ready to see it on your data, request a demo.






