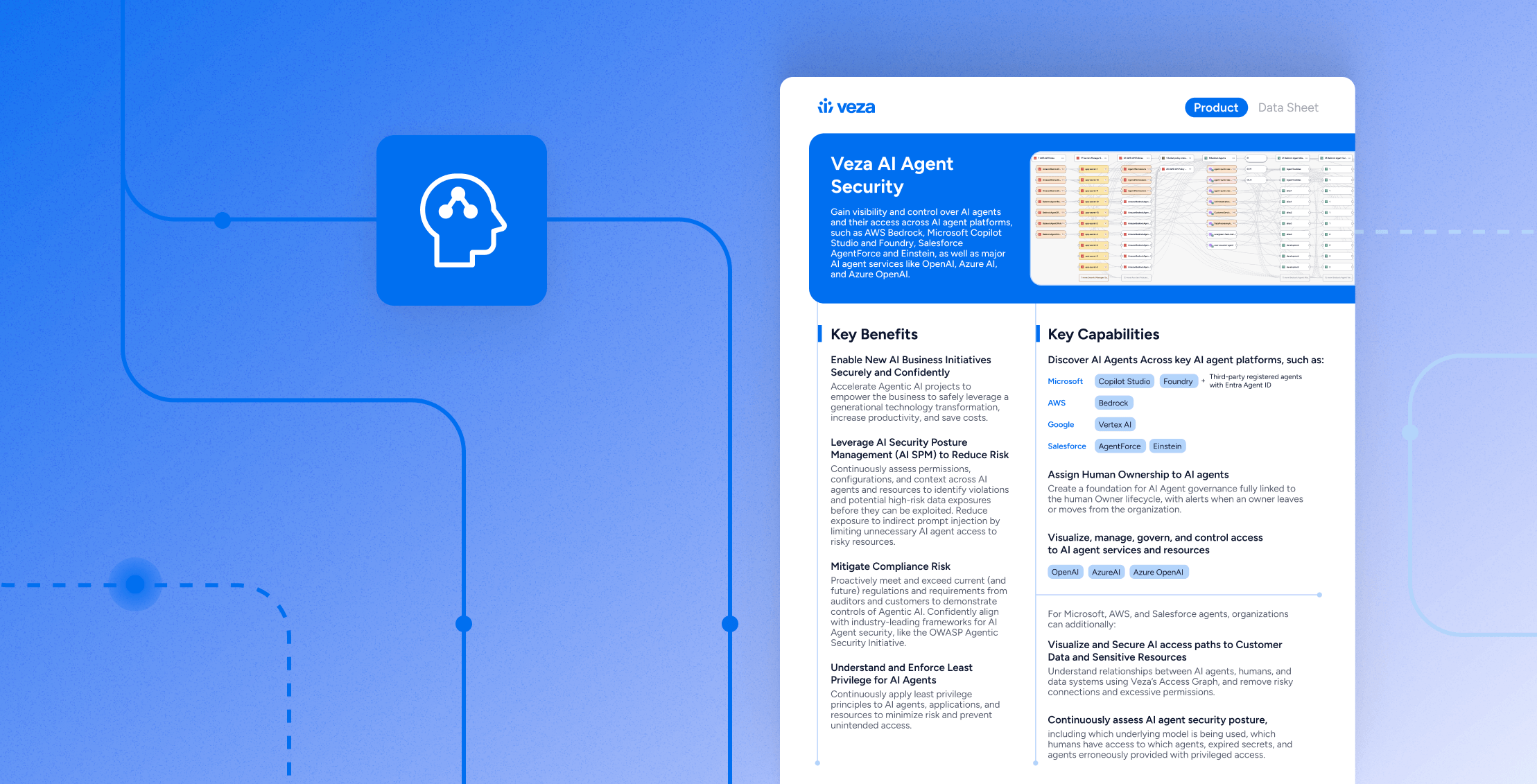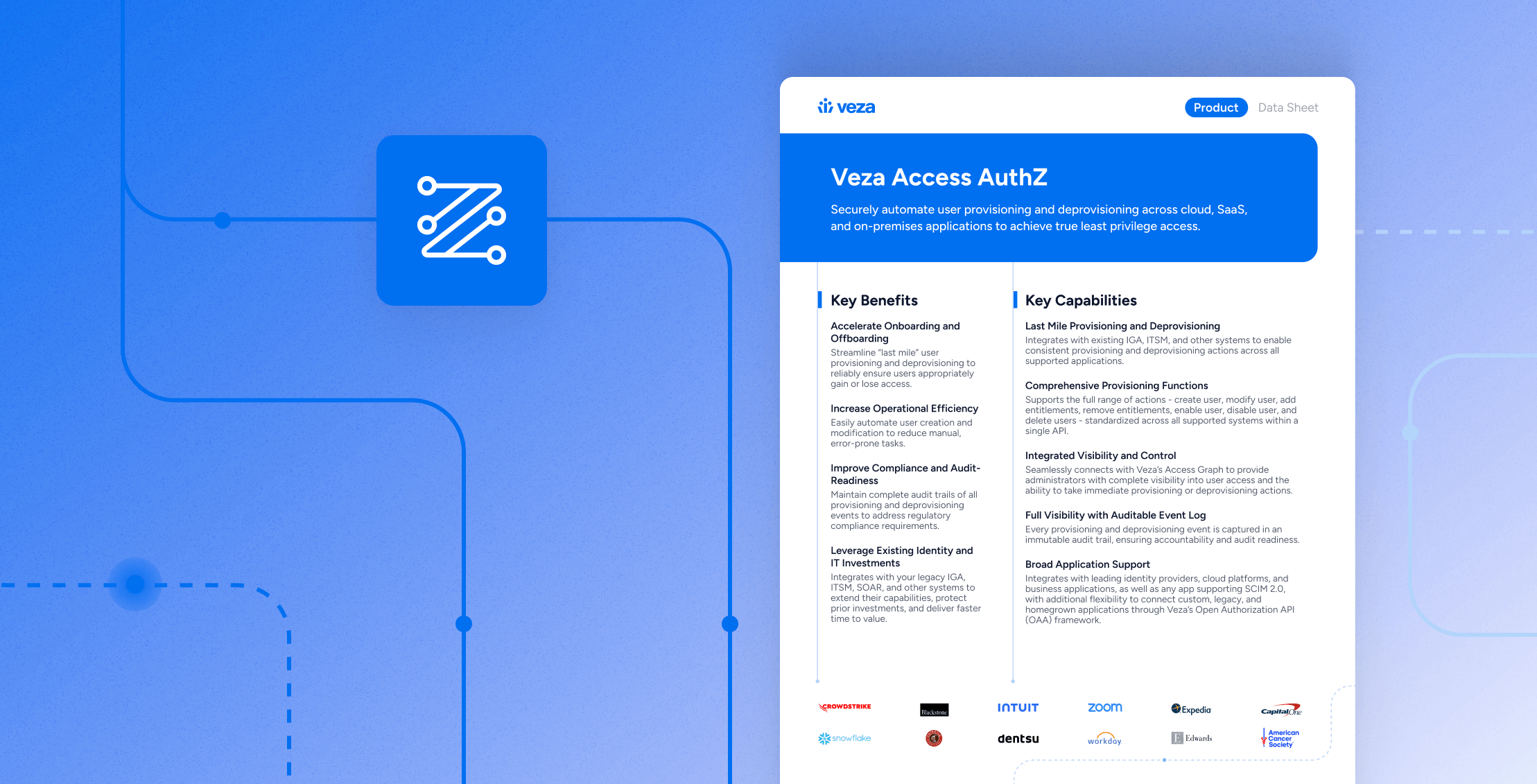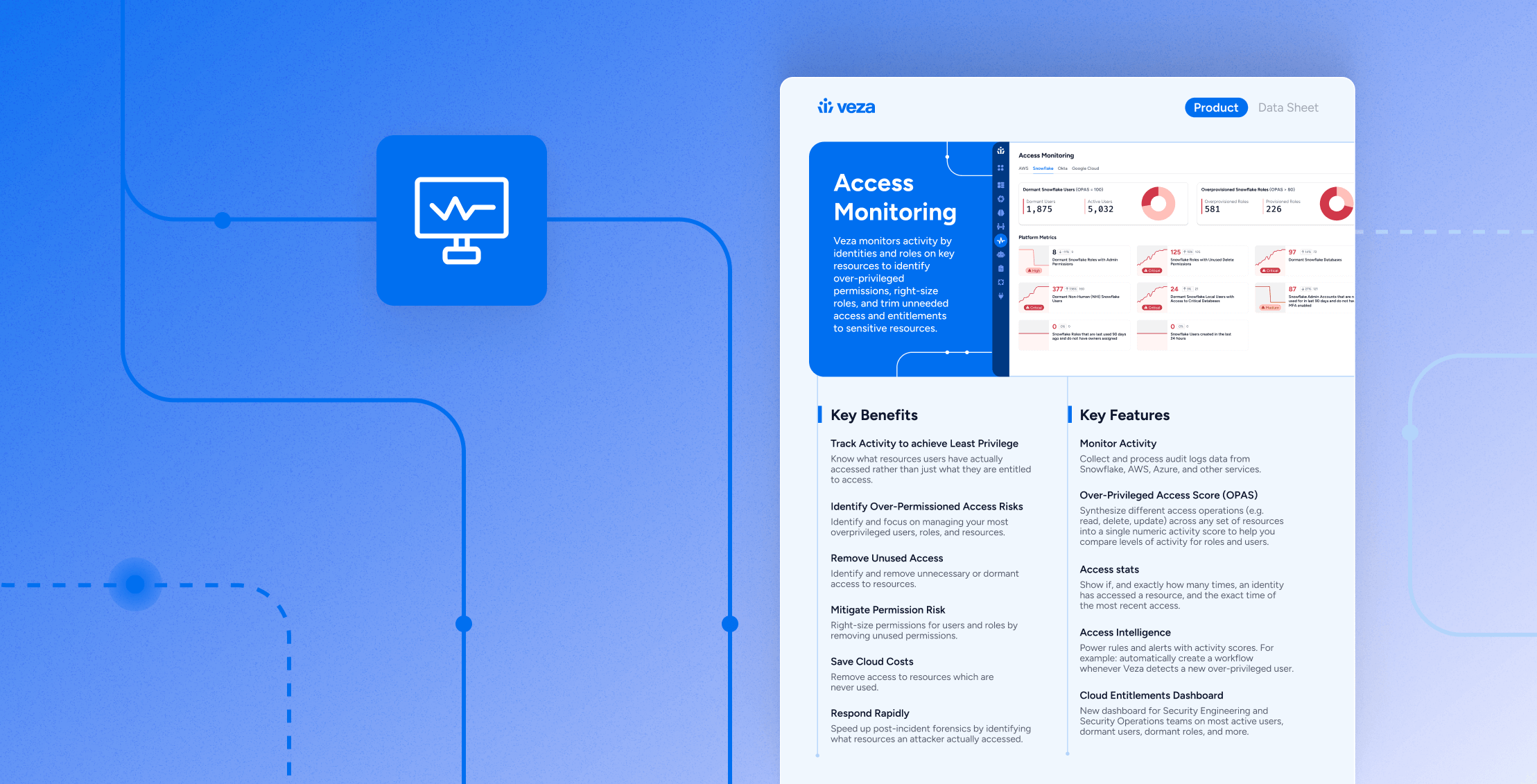
Veza Access Monitoring
Access you can defend. Least privilege you can prove.
Why this matters
Adversaries log in. Auditors ask for proof. Veza turns real activity into decisions you can act on so excess access gets found and fixed.
What you get
- Evidence of who actually used access
- Clear targets to remove dormant and risky permissions
- Faster investigations with precise activity context
- Confidence for audits and renewals
Who it’s for
SecOps, Security Engineering, IAM, and Cloud teams that want results, not spreadsheets.
Trusted by leaders
Seeing unused access lets us make better risk decisions.”
— Adam Fletcher, Chief Security Officer, Blackstone