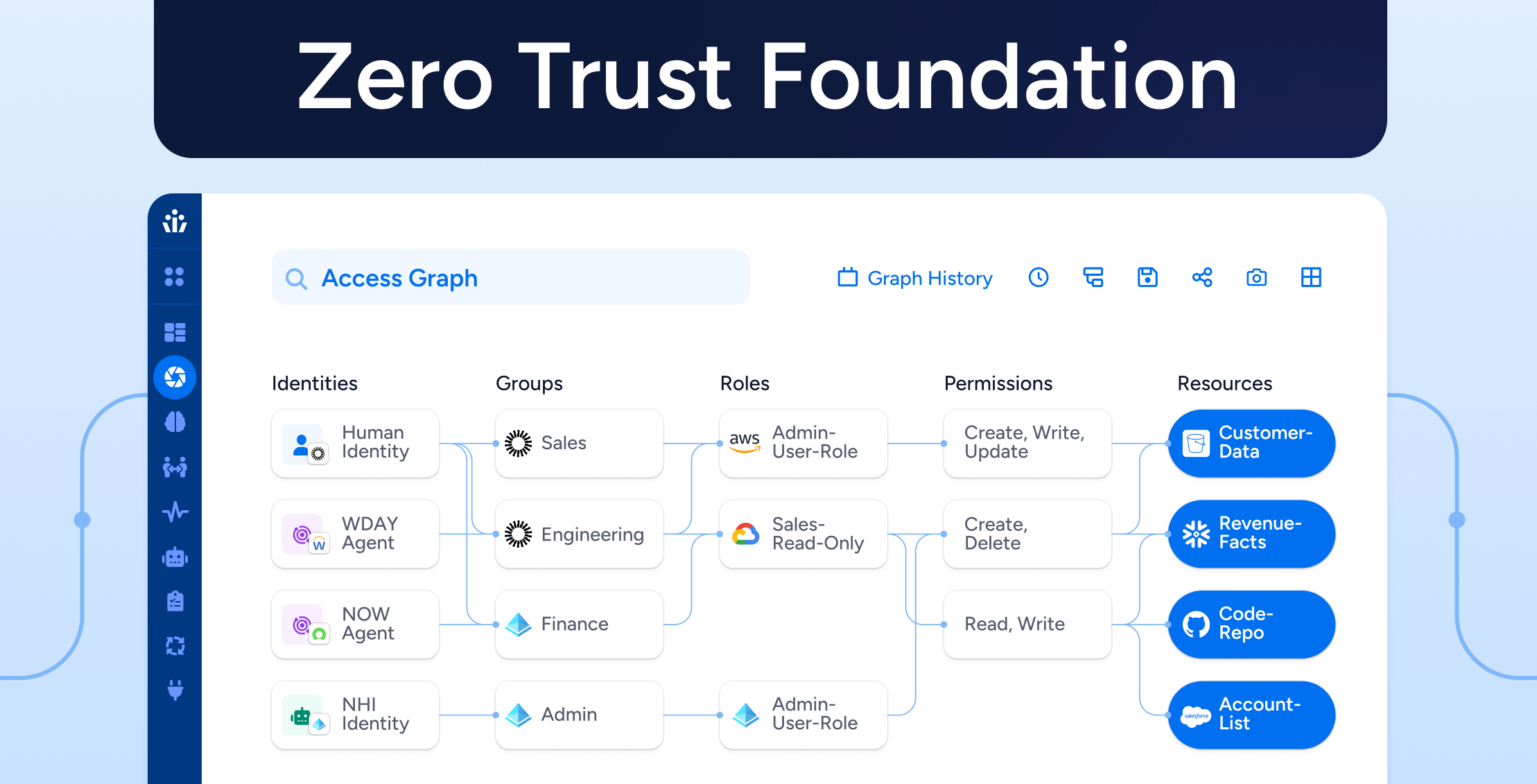
Zero Trust begins with a single question: Who has access to what?
A Brief History of Zero Trust
Fun fact: Zero Trust started due to identity. How? Organizations often err on the side of granting too much access to avoid business disruption. This “just in case” approach directly contradicts zero-trust principles, creating unnecessary risks. Coupled with insufficient automation and poor access review processes, excess permissions accumulate over time, expanding the potential impact of security breaches. Eventually, the identity debt built up, and Zero Trust was the logical way out. Instead of just in case, we moved to just in time.
The Challenge: Zero Trust Isn’t Possible Without Identity Security
Zero Trust is not a product – it’s a strategy rooted in “never trust, always verify.”
Most organizations start with MFA, segmentation, or endpoint controls, but the biggest blind spot remains: access.
Without real-time identity security, Zero Trust falls short:
How Veza Helps
Visualize Identity-to-Data Relationships
Unify access data across SaaS, cloud, and on-prem.
See who has access to what – down to the object level.
Map both human and non-human identities to entitlements with full lineage.
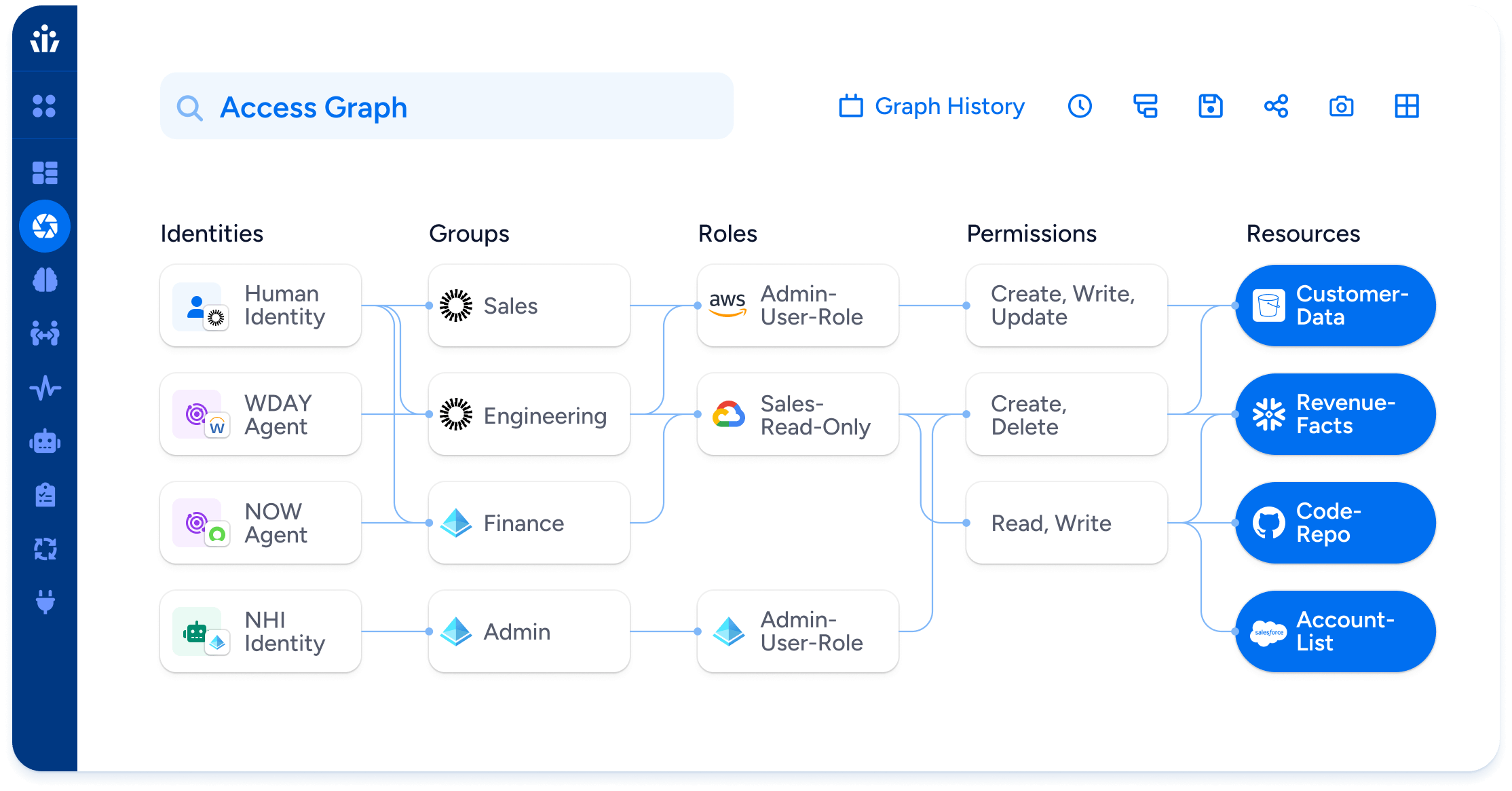
Enforce Least Privilege
Continuously detect and remediate over-permissioned users.
Generate right-sized role recommendations based on usage.
Govern access with business context, not just technical roles.
Enable Just-in-Time Access
Automate time-bound or request-based workflows.
Grant privileged access only when needed – and revoke automatically.
Integrate with ITSM tools like ServiceNow for ticket-based enforcement.
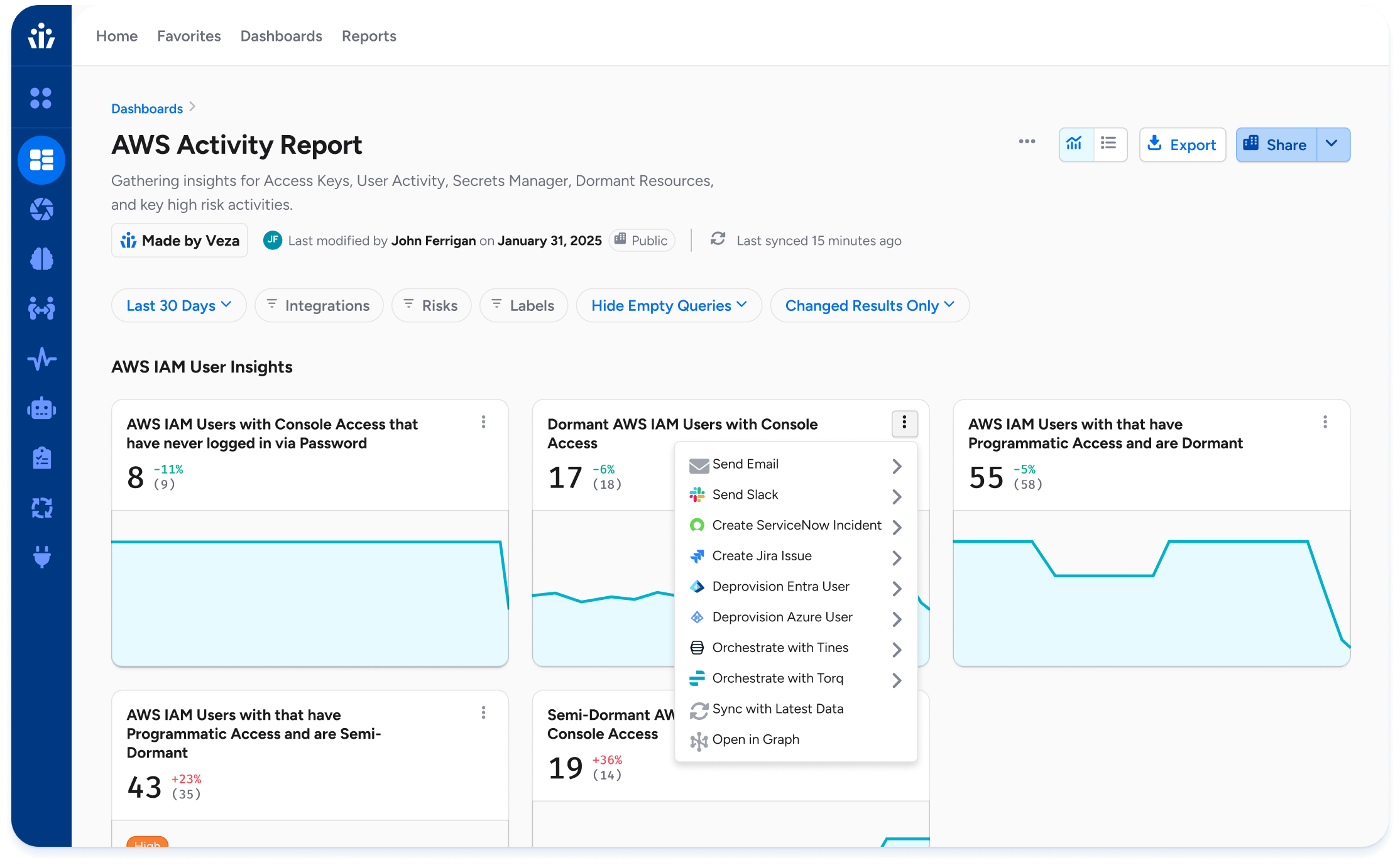
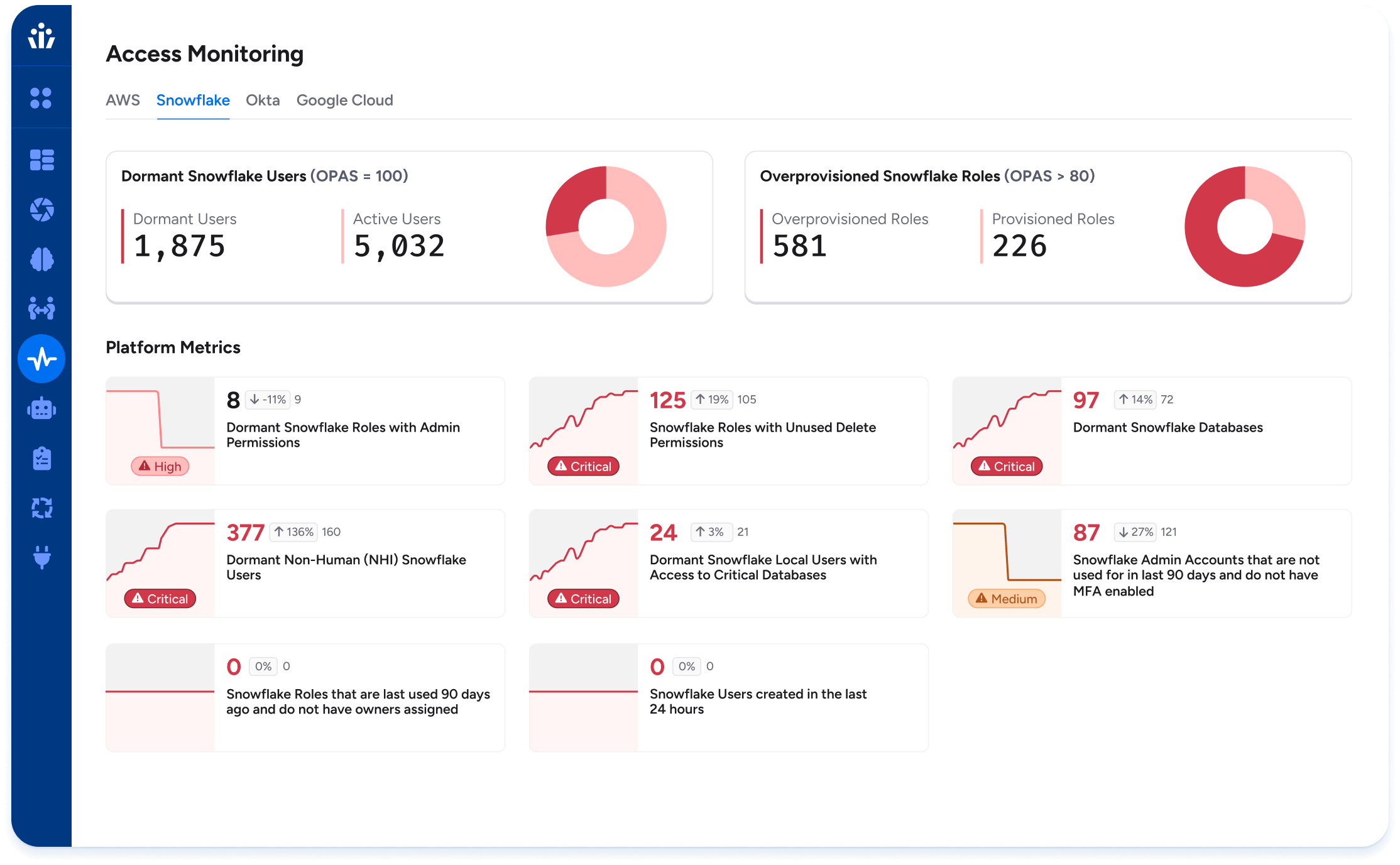
Monitor and Respond to Risk
Detect risky patterns and toxic access combinations.
Surface dormant or orphaned accounts for cleanup.
Trigger alerts and enforcement when least privilege is violated.
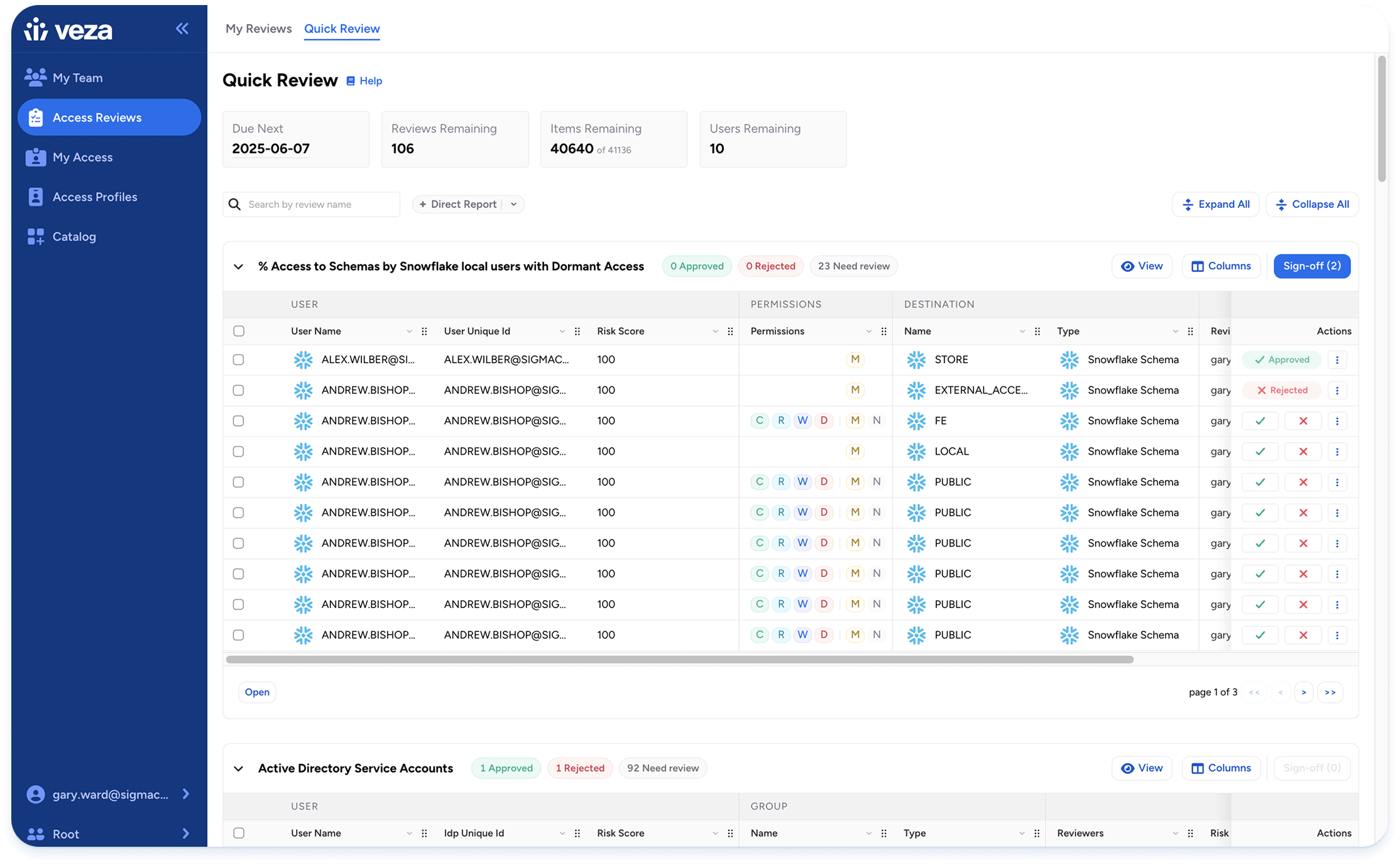
Outcomes with Veza
Additional Resources
Take the next step in your Zero Trust journey with Veza: