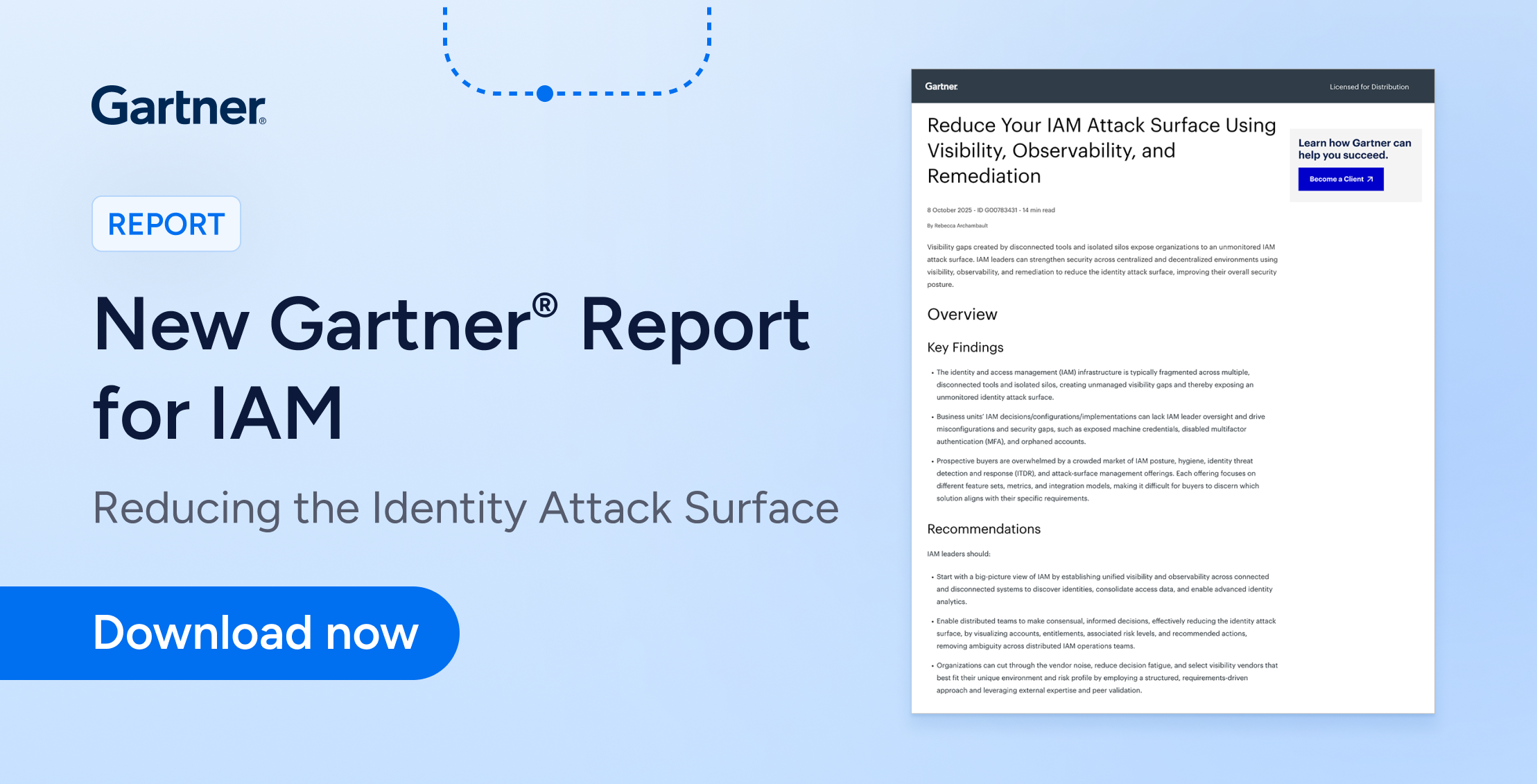
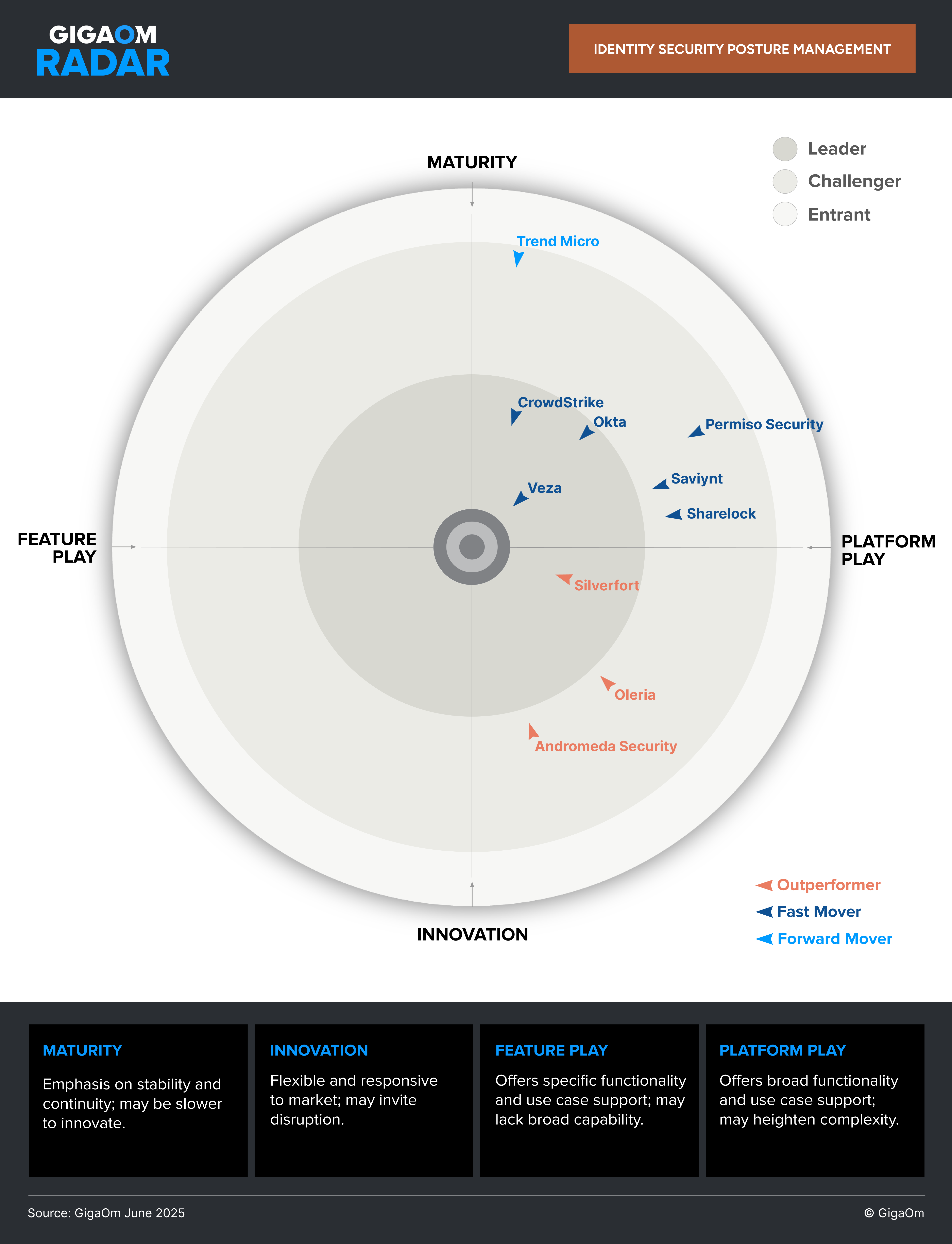
The #1 attack vector in cybersecurity? Identity.
This GigaOm Radar shows how top ISPM platforms help you close identity gaps before attackers exploit them.
Traditional IAM grants access. ISPM goes further—continuously monitoring and reducing identity risk across users, service accounts, cloud roles, and SaaS apps.
What You’ll Learn:
How to spot and fix misconfigurations, toxic permissions, and overprivileged accounts
How do ISPM platforms prioritize identity risk and automate least privilege enforcement
Who leads the ISPM market
Download the report by filling out the form.
Secure every identity. Stop the next breach before it happens.