SaaS Access Security & Governance
Veza is the fastest way to secure access to data in SaaS applications, reducing the risk of breaches and ensuring accurate audits for compliance.
Reduce the risk of breaches in SaaS apps
For all your identity security teams
Identity & Access Management (IAM)
- Configure, setup, and automate user access reviews
- Run recertification campaigns with manager and supervisor reviews
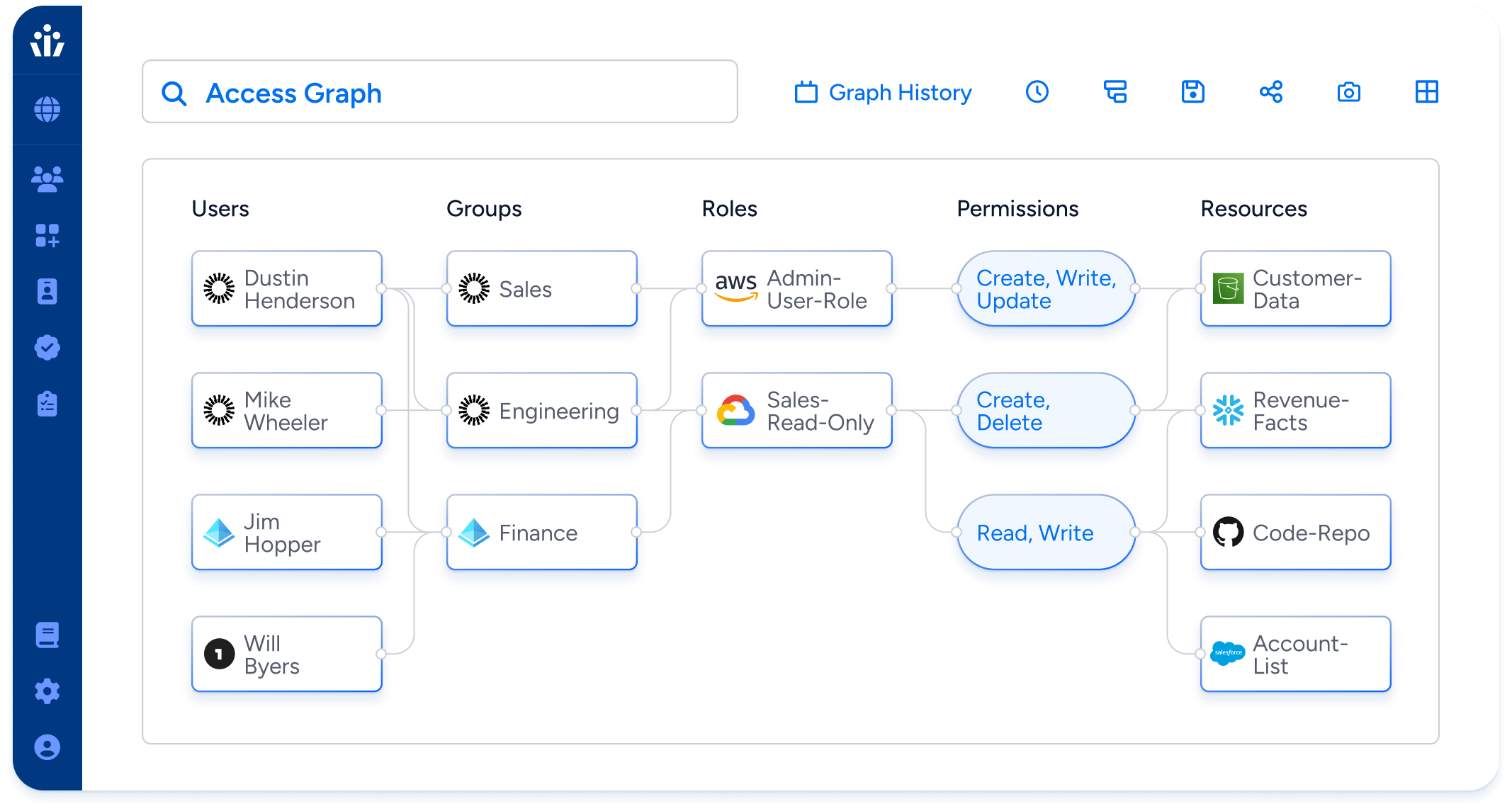
Governance, Risk & Compliance (GRC)
- Automatically compile review and certification campaigns covering your cloud environments, on-premise systems, and SaaS apps.
- Delegate decision making to employee managers or data owners.
- Integrate with SOAR and ITSM systems like ServiceNow and Jira to implement access review decisions consistently and fast.
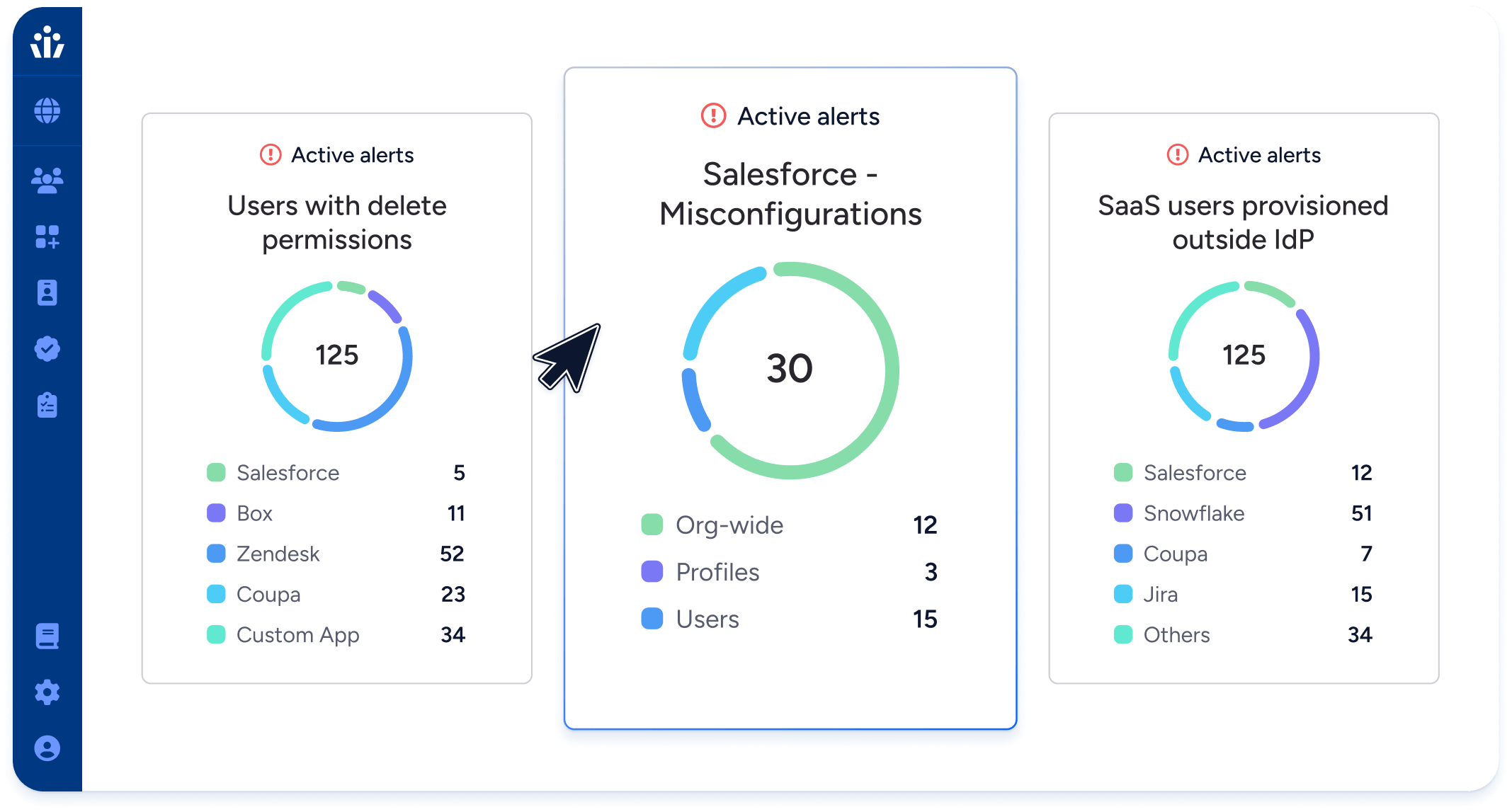
Security Engineering & Security Operations
- Assess risks with out-of-box dashboards, insights, and analytics for apps like Salesforce, GitHub, and Atlassian.
- Find and fix accounts with by creating and enforcing policies on risky posture such as no MFA enrollment.
- Discover local users who are not in your SSO or IGA systems.
- Get notifications in ITSM systems like ServiceNow or PagerDuty when privilege violations are detected.
- Pinpoint and revoke unused or dormant permissions.
- Analyze historical access and blast radius for any compromised account.
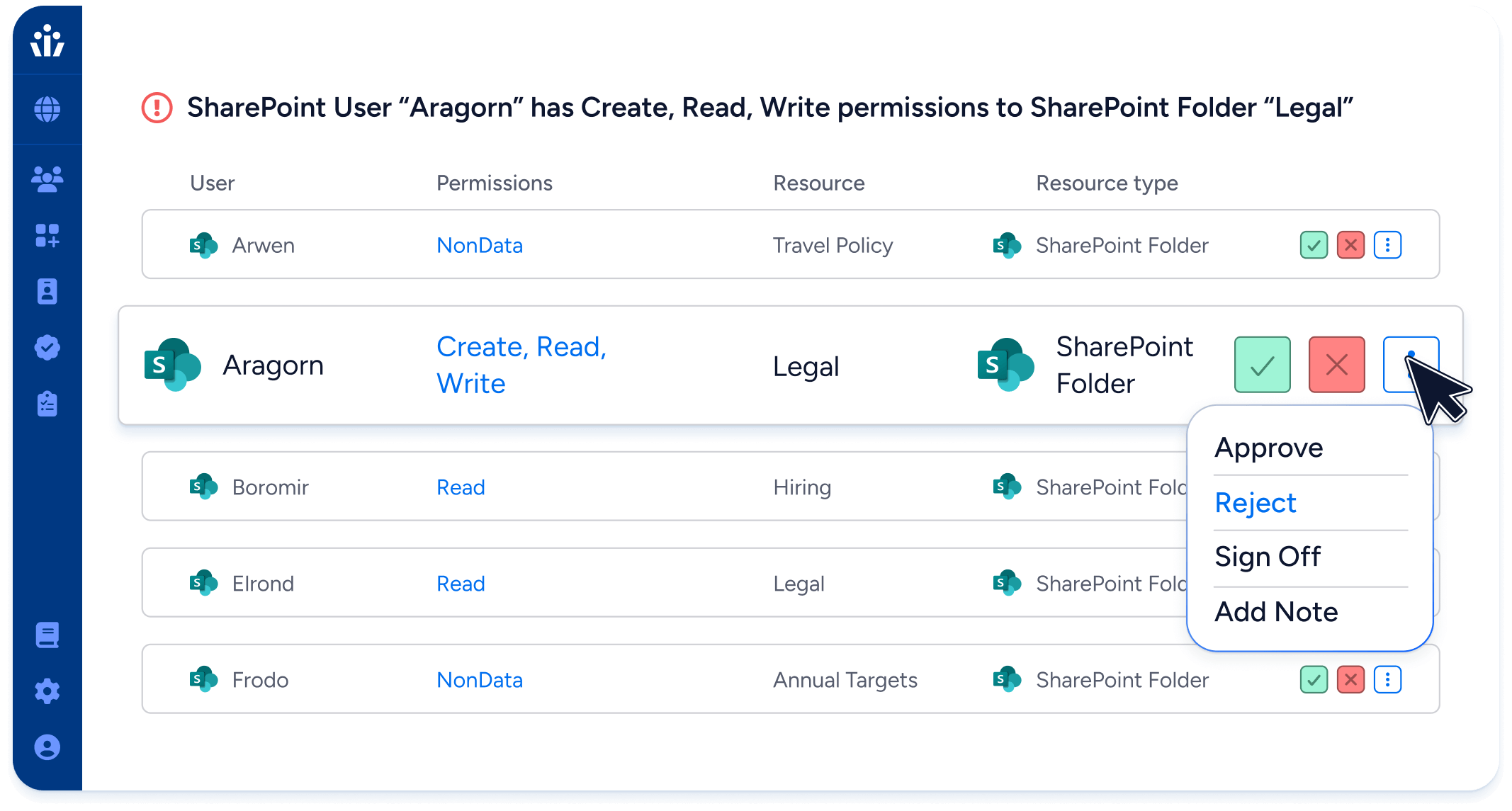
Leading enterprises trust Veza to manage SaaS Access Security








“As TGen continues to adopt multi-cloud architectures and deploy various SaaS apps like Slack, Veza gives us instant visibility into access permissions, enabling us to define privileged access standards throughout the organization. Veza has provided a level of platform agnostic, multi-cloud privilege visibility I hadn’t seen before, and is playing a key role in our ongoing onboarding of SaaS.”
John Forrister, Vice President Information Security | TGen
Learn More
-

Simplifying CMMC 2.0 Compliance: Modern Access Control Strategies for Government Contractors
Learn more -
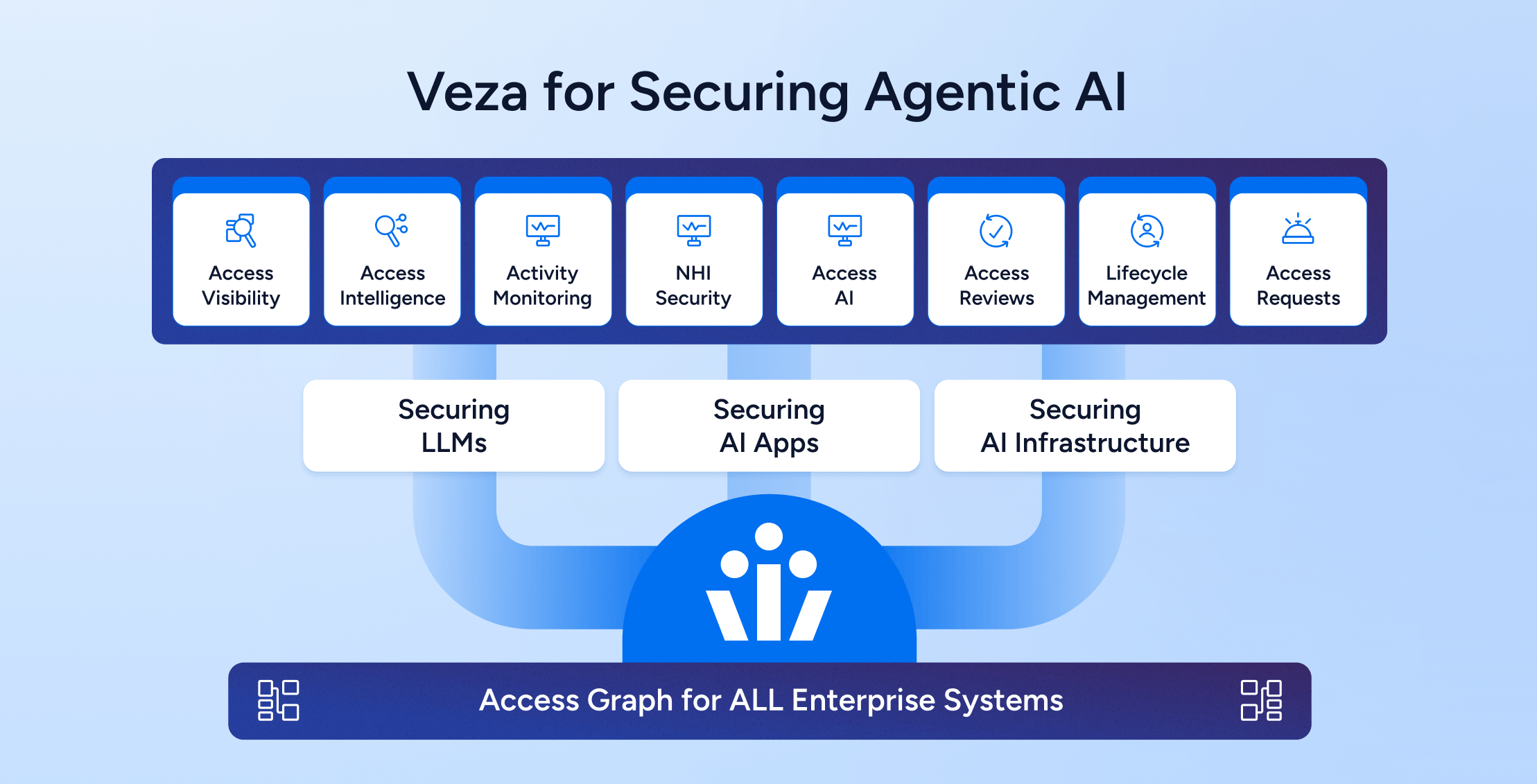
Trust as the Foundation for Agentic AI Architecture: Securing Access to all the AI layers – Models, Infra, AI Applications
Learn more -
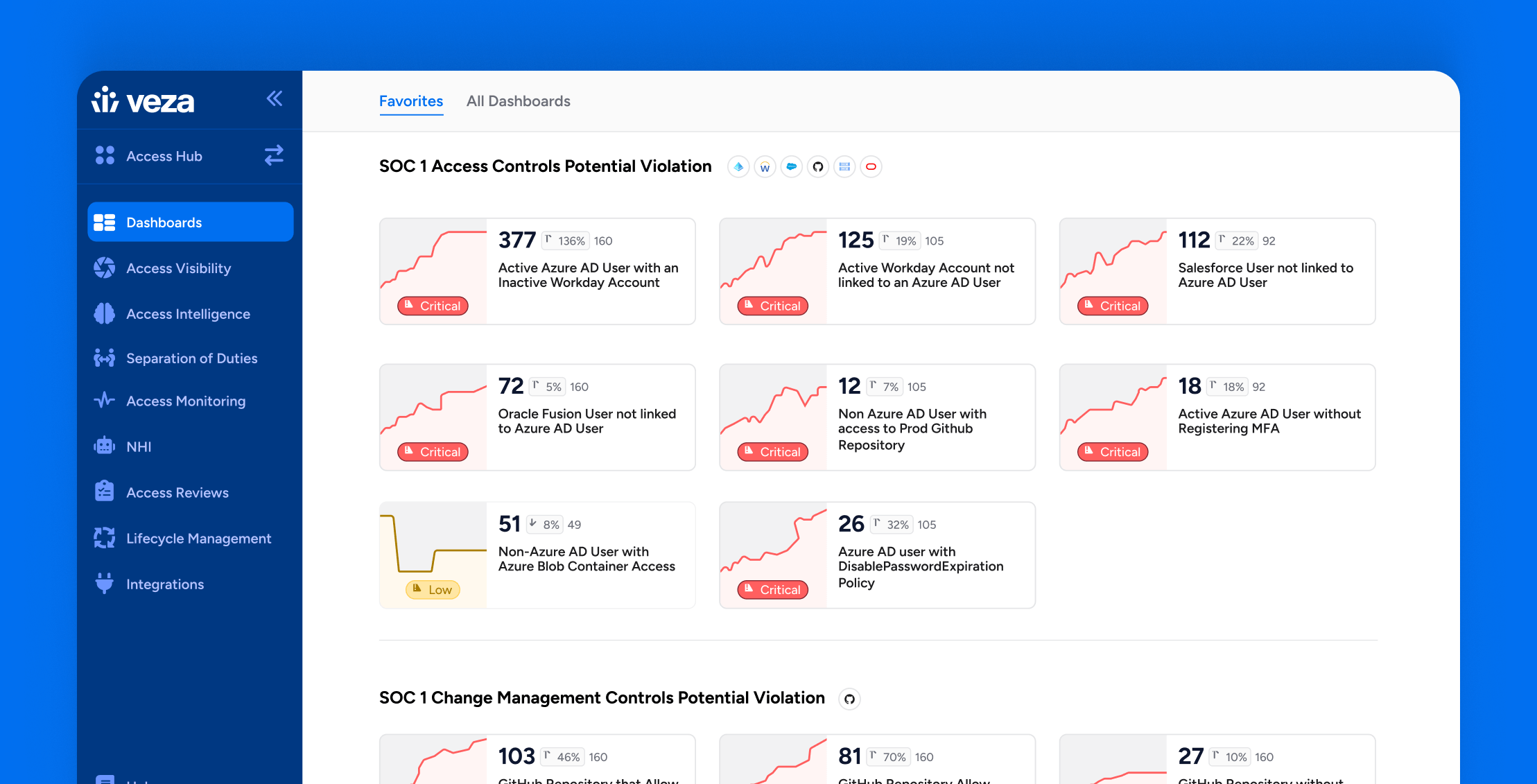
How Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more




