Cloud Access Management
Migration to the cloud made access management exponentially harder, with many more identities and resources to manage. Veza helps you untangle the complex web of cloud IAM to know exactly who can do what across Amazon, Google, Azure, and Oracle cloud environments.
Access managment at enterprise scale
For all your identity security teams
Identity & Access Management (IAM)
Understand the effective permissions of cloud identities without the need to master multiple complex IAM systems.
Seamlessly onboard and offboard users from your cloud environments, assigning appropriate access according to team and duties.
Respond to requests for resource access with automated least privilege group and role recommendations.
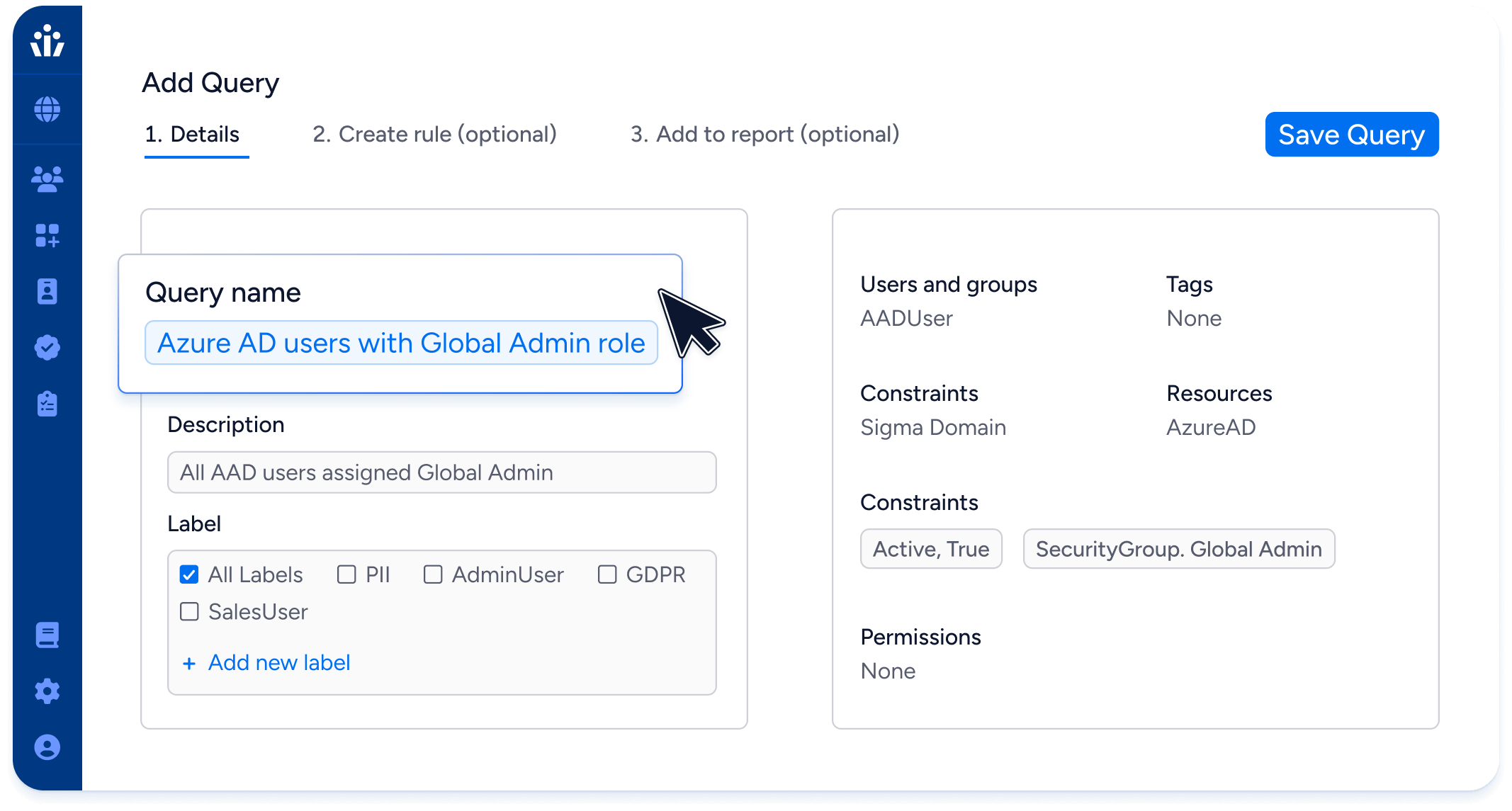
Governance, Risk & Compliance (GRC)
Instantly compile comprehensive access reviews for your cloud environments assigned to user managers or resource owners.
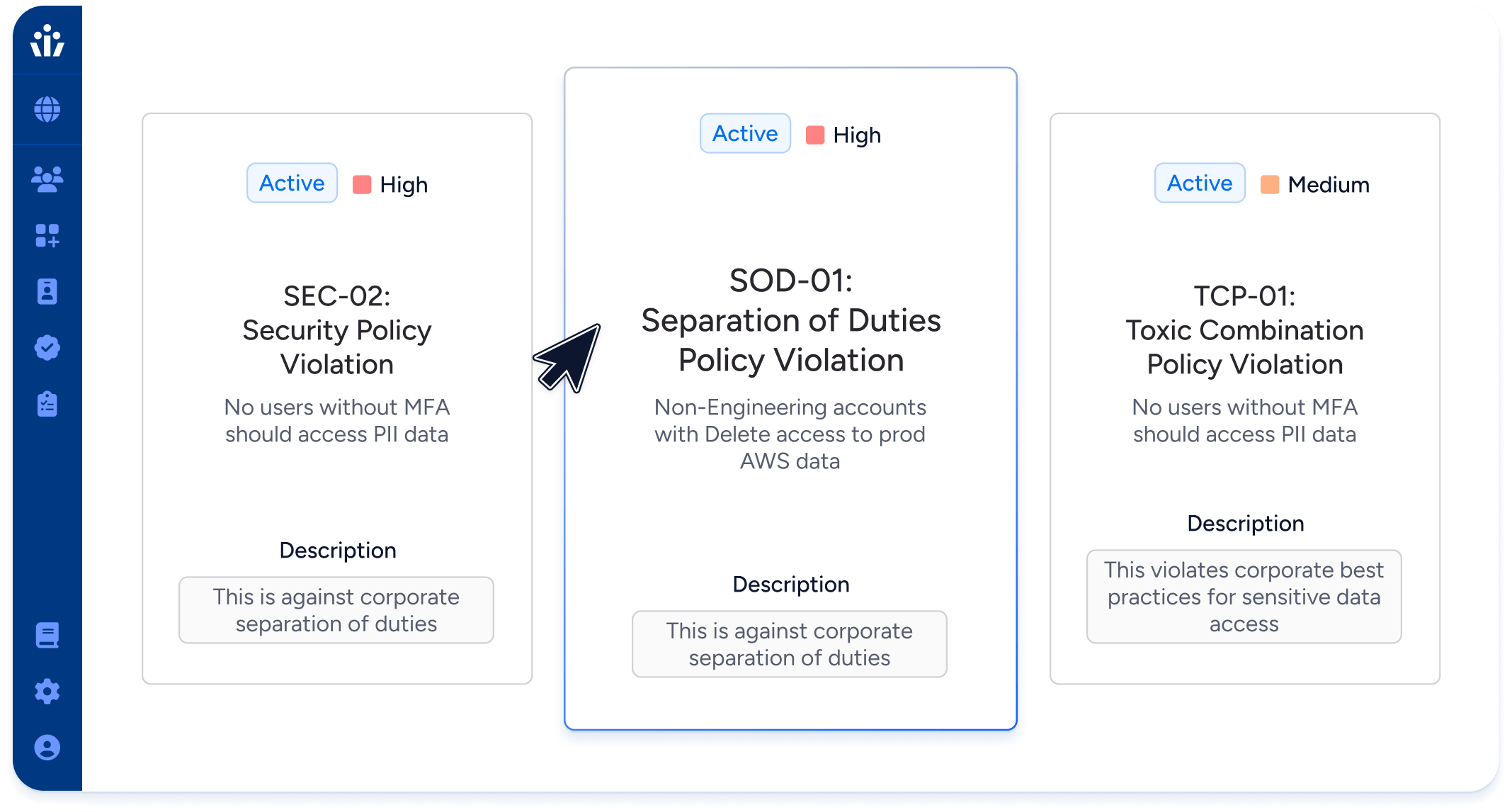
Enforce policies for toxic combinations or separation of duties (SoD).
Track all users with admin permissions in your cloud environments.
Security Engineering & Security Operations
Analyze historical access and blast radius in your cloud environments to detect and respond to any compromised account.
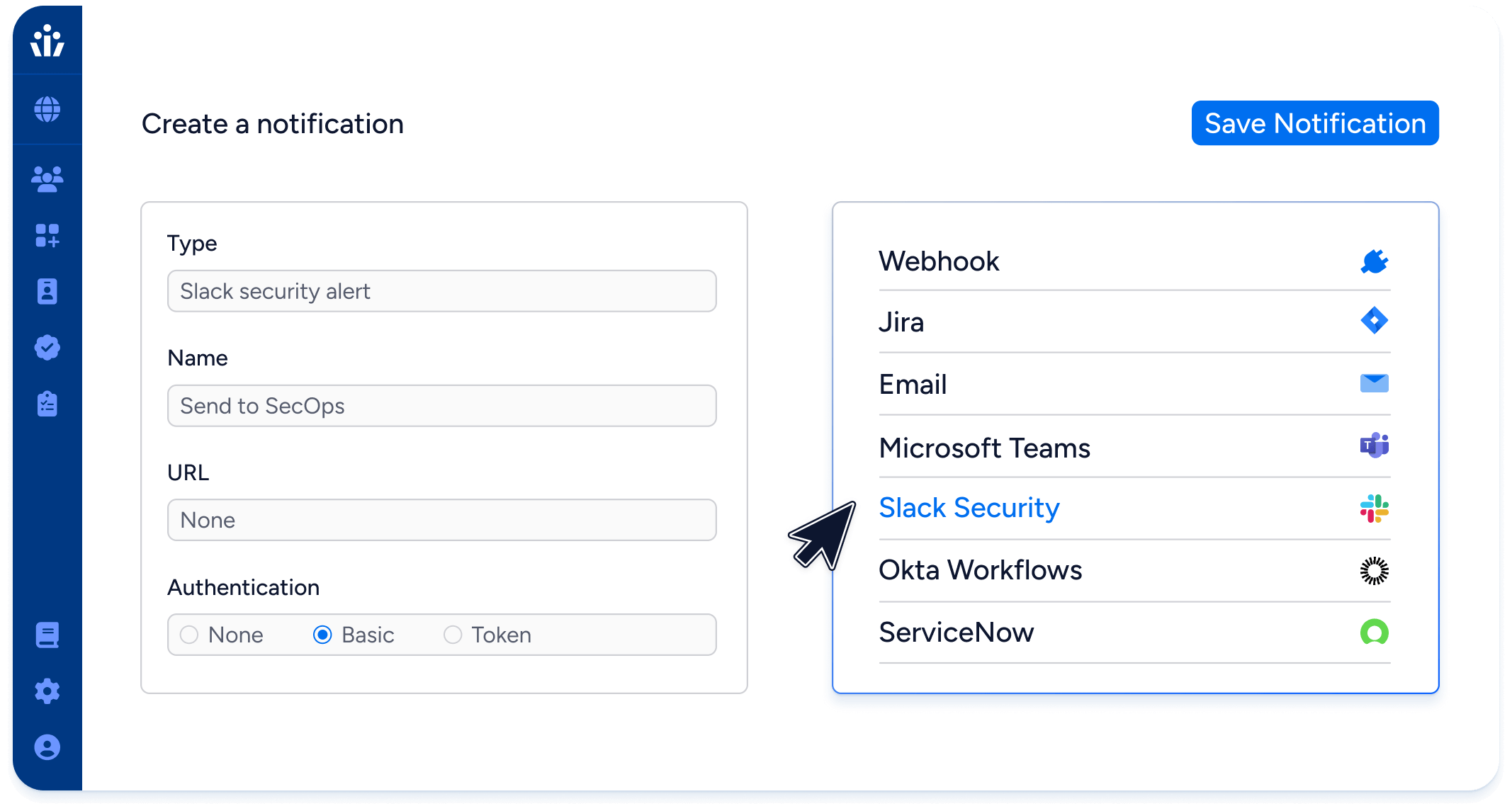
Remediate risks and violations in real-time with alerts or ITSM tickets in ServiceNow, Slack, or JIRA.
Pinpoint unused permissions to remove privileged accounts without impacting user experience.


“If you’re using a cloud of any size, there’s probably plenty of things that you’ve done in the past that didn’t have the right governance around them. And being able to go back, see that, fix it, and then put governance on top of it to ensure that it doesn’t sprawl again, that that’s one of the things that we just love about Veza.“
Jason Simpson | Vice President of Engineering
Learn More
-

Veza – The Enterprise Agent Identity Control Plane
Learn moreVeza’s 2026 State of Identity and Access Report found that in a typical enterprise, an average worker holds 96,000 entitlements, 38% of IdP accounts are dormant and only 55% of permissions are safe and compliant. The volume and complexity of identity-based attacks is exacerbated by the explosion of AI agents and non-human identities (NHIs). In […] -

Taming the M&A Chaos: How Veza Addresses Identity Security Risks During Mergers, Acquisitions, and Divestitures
Learn more








