Privileged Access Assurance for Today’s Enterprise
Protect your most sensitive data with continuous visibility and control over who has privileged access, without slowing down the business. Veza delivers authorization assurance that includes Privileged Access Management (PAM) capabilities but goes far beyond, governing access across all identities, not just privileged users.

Eliminate Blind Spots in Privileged Access Assurance
Traditional PAM tools focus on access to systems — Veza focuses on access within them. That means not just knowing who can log in, but understanding who can take what action on what data, and continuously enforcing the right level of access at all times.
Why Enterprises Choose Veza for Privileged Access Assurance
Beyond PAM: A More Complete Approach to Access Governance
While Privileged Access Assurance is a critical need, Veza’s platform offers a more comprehensive scope than traditional PAM solutions. By focusing on authorization across all identities and data systems, we help organizations:
Govern
Govern access for all users — human and non-human
Visualize
Visualize what actions identities can take, not just where they log in
Automate
Automate access reviews, attestations, and removals
Real-time Assurance
Provide near real-time assurance across apps, data, infrastructure, and cloud environments
Built for Compliance and Security Leaders Alike
Whether you’re preparing for a SOX audit or tightening controls flagged by risk teams, Veza helps you:
- Continuously enforce access controls over sensitive data
- Provide full visibility into who has access to what, and why
- Eliminate manual processes with automated certifications and workflows
- Accelerate compliance and reduce audit prep time
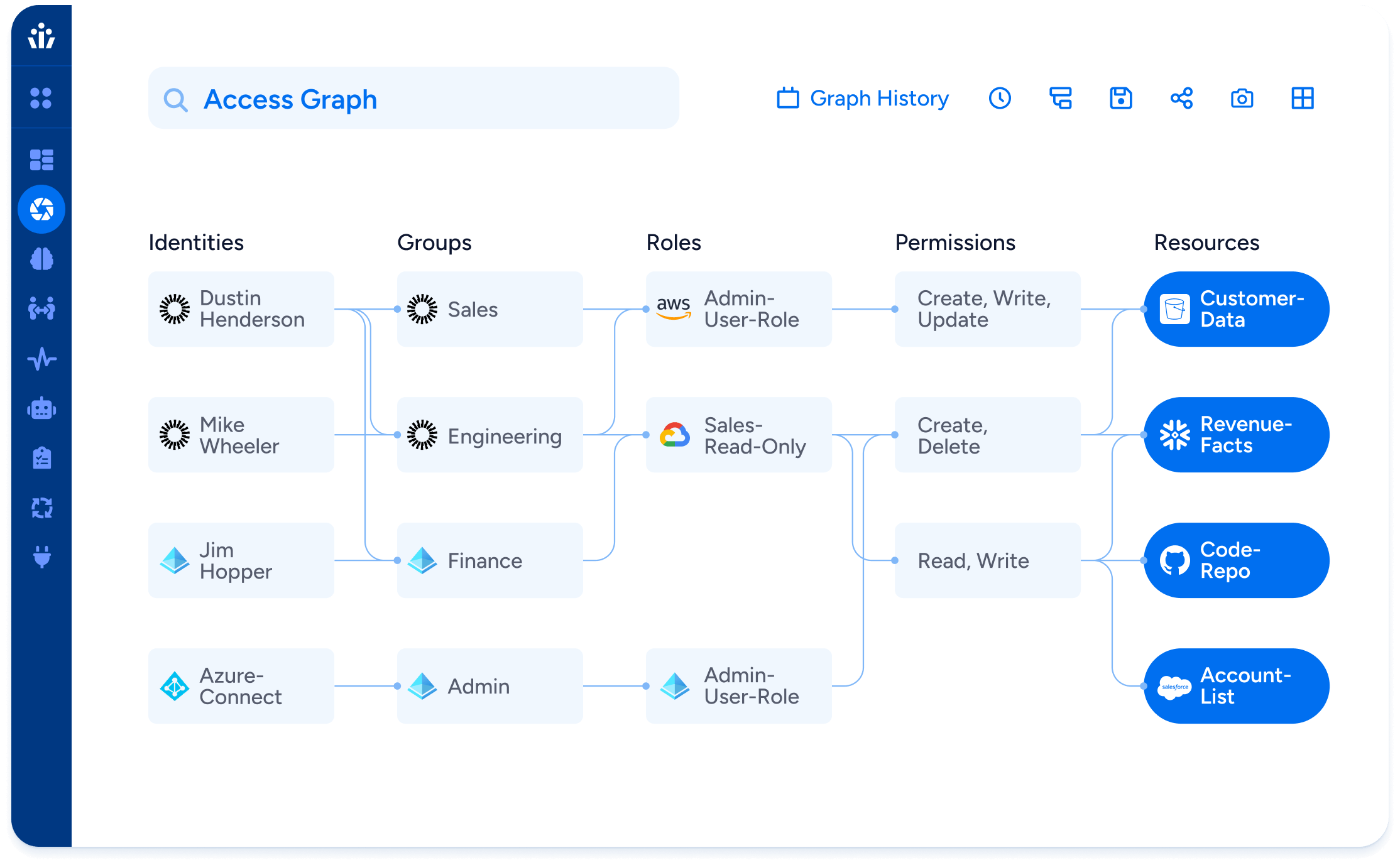
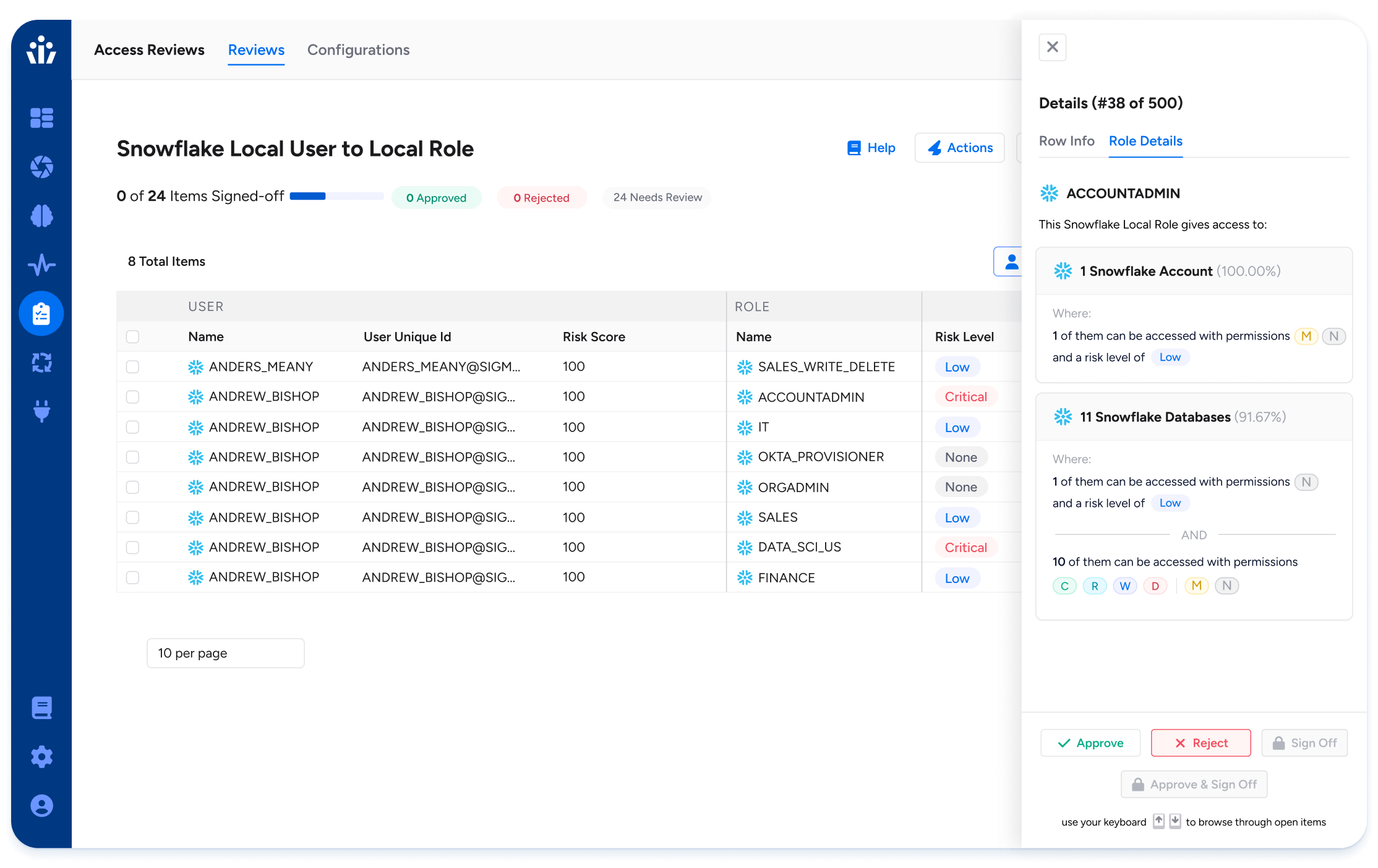
See it in Action
Request a Custom Demo to Discover:
- How to instantly visualize who has access to your most sensitive systems and data
- How to connect Veza to your identity, cloud, and security stack for continuous enforcement
- How to deliver audit-ready reports that prove access is governed in real time