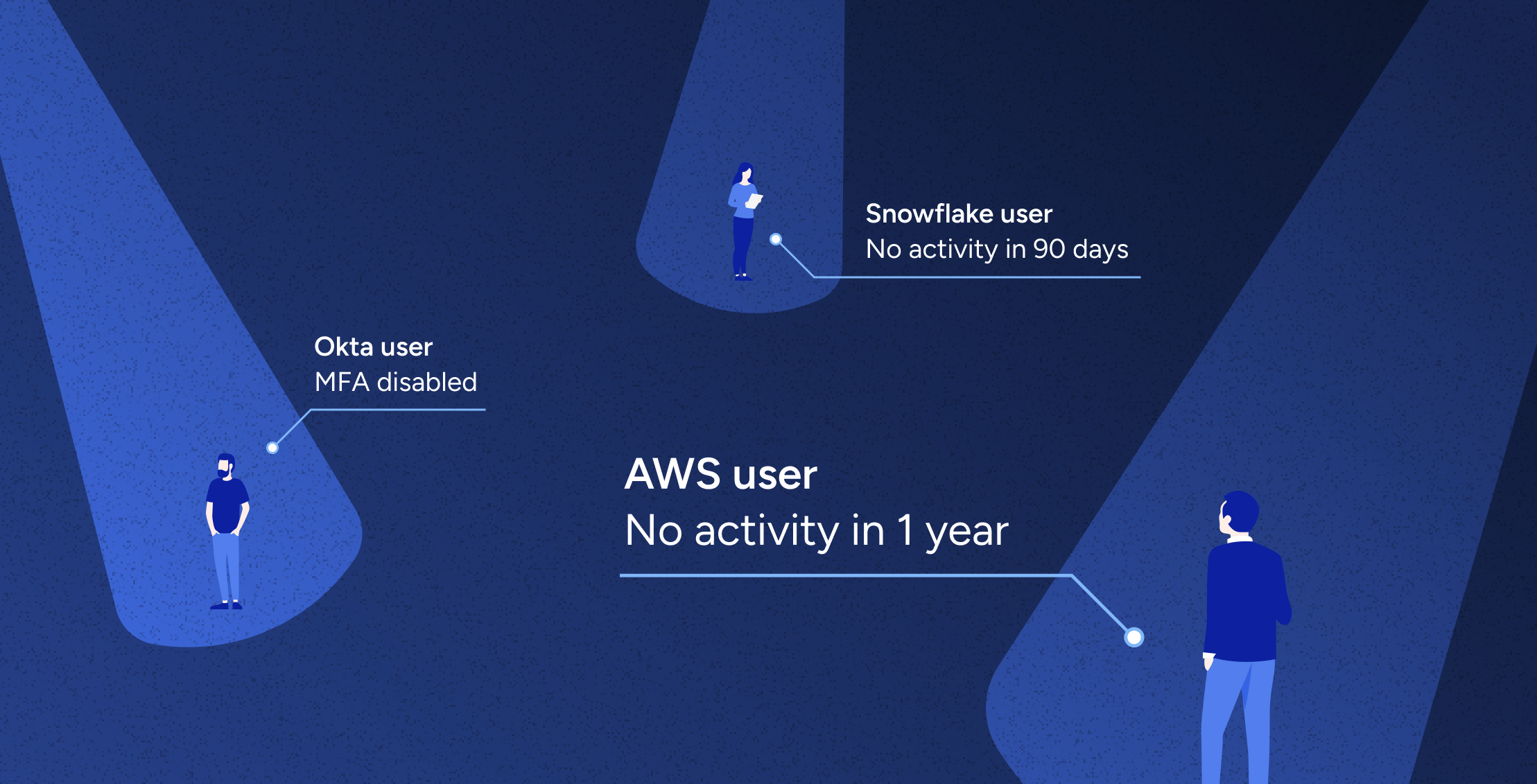
With the average enterprise using 371 SaaS applications to conduct day-to-day operations, access is becoming more disparate and difficult to manage. Access is codified via system specific permissions and entitlements, and the lack of understanding of what these permissions mean, results in increasing the risk for organizations. In order to maintain least privilege, enterprises must ensure that their users are given the appropriate birthright access as well as continuously detect and remove unused or inappropriate access. Furthermore, organizations have been focusing on finding unused access to applications as a means of reducing expenditure associated with growing SaaS license costs.
The Veza Access Platform allows security and identity teams to gain the understanding of identities and associated access across platforms, SaaS applications, and resources in order to determine if accounts are over-permissioned or if entitlements have been unused. Using Veza Lifecycle Management, users can be provisioned and deprovisioned automatically to ensure that users have access to the appropriate set of entitlements across applications based on their role, location, and function in the organization. Furthermore, all Veza products, such as Access Intelligence, integrate with the System for Cross-Domain Identity Management (SCIM) protocol to further automate the deprovisioning process by making it more intelligent and standardized, especially when Veza is detecting security incidents, usage activity (or lack thereof), or other noteworthy events (i.e. lateral movement, privilege elevation, privilege drift, etc.) that need to result in user deprovisioning to reduce and limit access.
Common Access Revocation Scenarios
Automate Termination of Identities
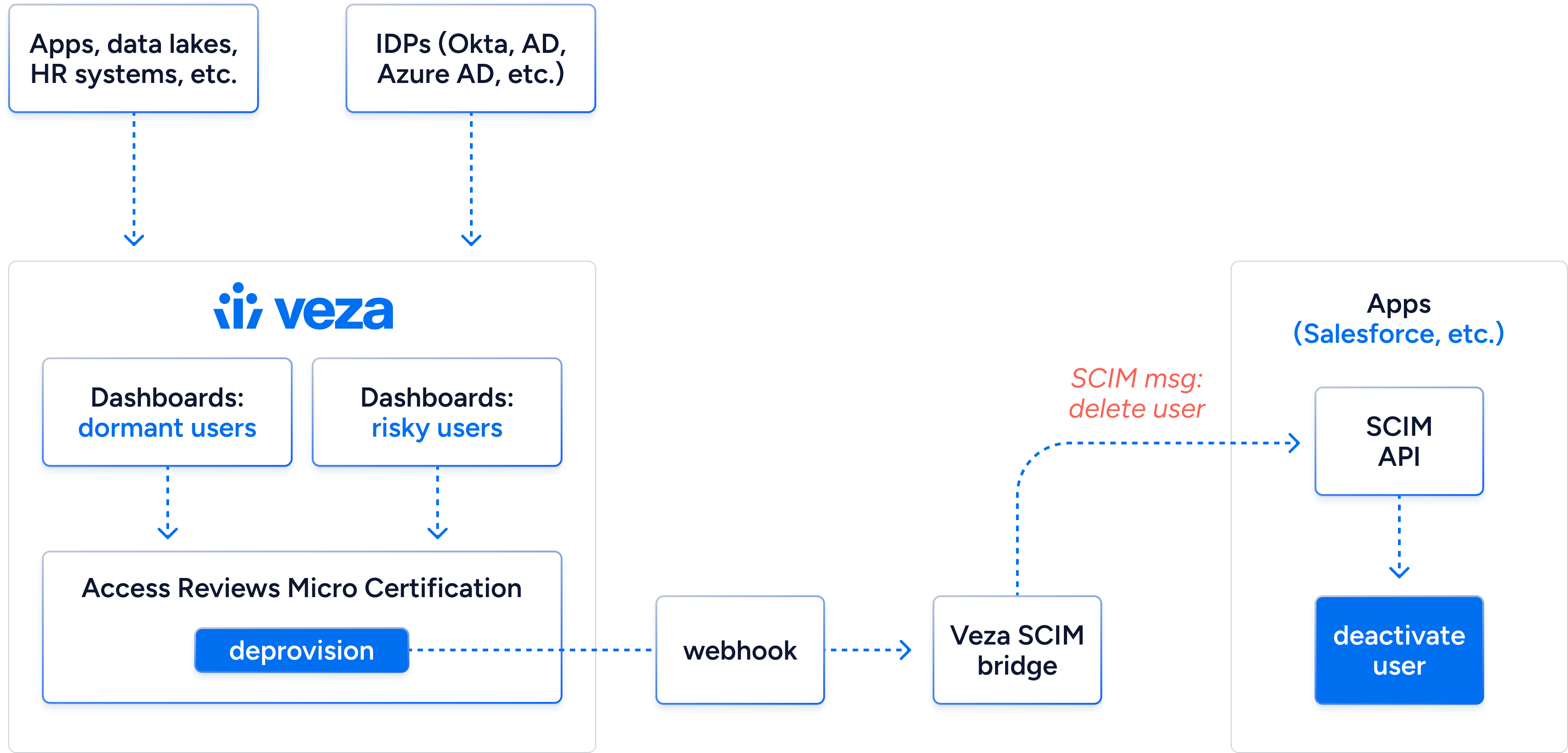
By utilizing Veza’s reporting and alerting capabilities in conjunction with webhook-based triggers and the Veza SCIM Bridge, organizations are able to automate the removal of access to applications, alleviating the pains of the error-prone, manual processes. Through the use of the Veza SCIM Bridge, organizations can automatically remove access based on a predetermined event, such as a security incident or other indicators of risk detected by Veza. For urgent, time-sensitive departures, teams can even manually trigger a deprovisioning workflow – ensuring that all access to the system is immediately revoked.
Remove Over-Provisioned Access
To help organizations improve their identity security posture management (ISPM), they must identify efficient methods for detecting and removing over-provisioned access without disrupting business processes. A user who has access beyond what is necessary to an application is increasing the blast radius of any potential attack against (or compromise of) that user’s account.
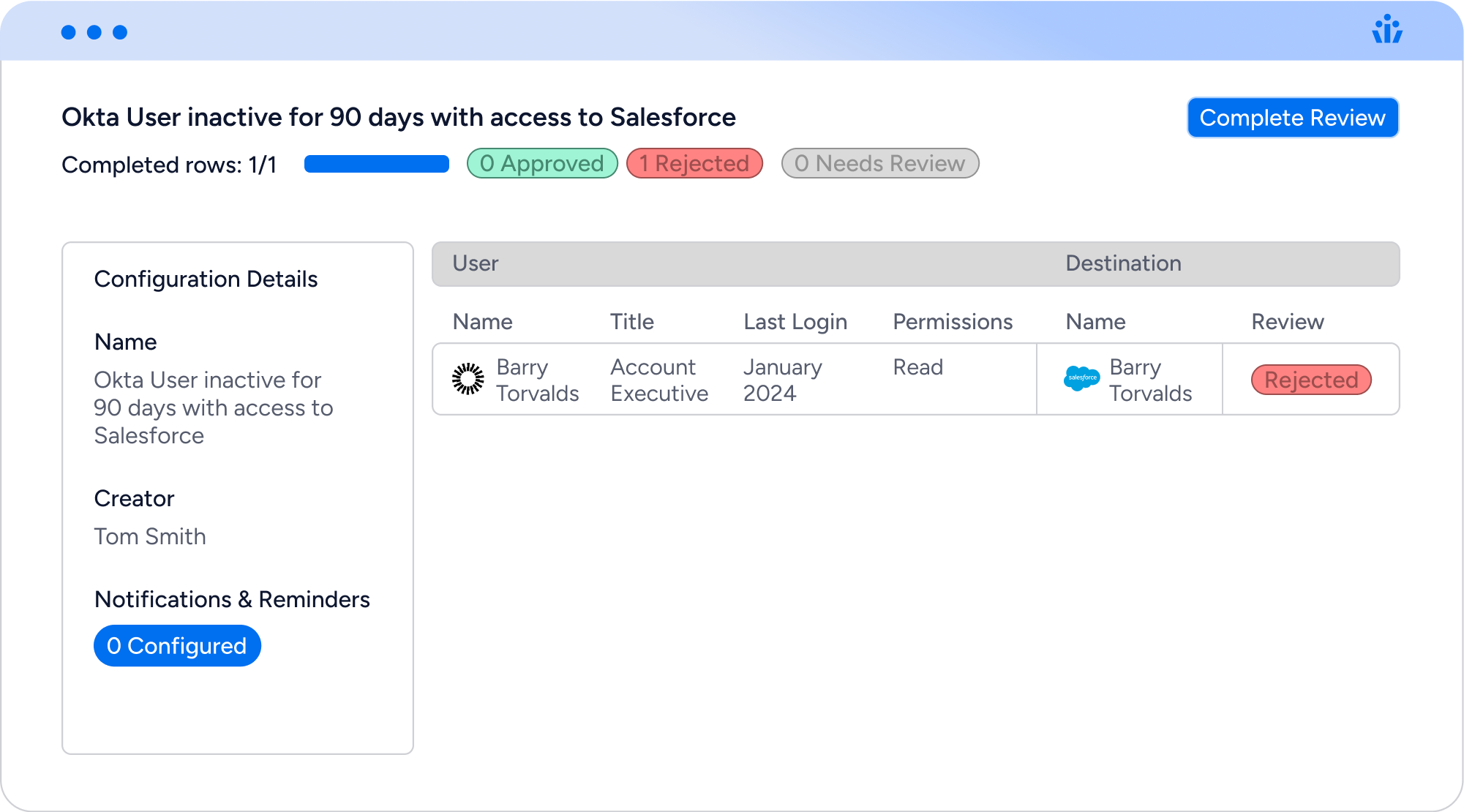
Veza Access Intelligence allows you to set up continuous monitoring controls to identify unused or over-provisioned access. For example, if a user does not log into Okta for 120 days, Veza can automatically initiate action. Importantly, these actions can vary – they may include launching an on-demand access review that presents the decision to maintain access to the user’s manager for approval or removal. If necessary, deprovisioning could be undertaken immediately. Using the Veza SCIM Bridge, Veza Access Intelligence can trigger a deprovisioning workflow that will remove the user from the target application immediately after detection.
Save on SaaS Licensing Costs
Today’s macroeconomic environment requires organizations to be efficient with their resources. Besides reducing risk by removing unused access, organizations can benefit from reallocating expensive software licenses to employees who truly need access and will fully utilize the license.
By combining Veza Access Intelligence and Veza SCIM Bridge, organizations can monitor for unused license entitlements and initiate deprovisioning of those license seats. Once recovered, the organization can decide to stop paying for the relinquished license or reallocate its usage for more productive purposes.
Ensure Consistent, Correct, and Least Privilege Access
Through Veza Lifecycle Management, organizations can automate the provisioning and deprovisioning processes across typical joiner, mover, and leaver (JML) scenarios. With our policy-based framework and capability to monitor user state changes from authoritative sources of identity, Veza Lifecycle Management can automatically deprovision user access in situations involving high volumes of movers and leavers. There are a number of scenarios that may require a thorough and consistent deprovisioning of user accounts, such as terminations, resignations, reductions in force, job changes, reporting structure changes, and department transfers. Veza Lifecycle Management offers both native and Veza’s Open Authorization API-based integrations as well as support for SCIM thus enabling deprovisioning across a wide range of applications and platforms.
Why SCIM?
SCIM, or System for Cross-Domain Identity Management, is an open, HTTP-based standard protocol designed to automate the exchange of user identity information between Identity Providers (IdP) and cloud-based Service Providers (SP).
With SCIM, organizations can benefit from:
- Standardization: A common language and format for exchanging user data, making it easier for different systems to communicate and interoperate.
- Automation: Automated provisioning, deprovisioning, and management of user accounts across multiple applications, reducing manual effort and errors.
- Security: Ensures that user data is exchanged securely using HTTPS and other security protocols.
- Flexibility: Supports various use cases, including employee onboarding, offboarding, and changes in roles or permissions.
Importantly, Veza has integrated with SCIM because it works seamlessly across vendors and platforms. For instance, with SCIM, Microsoft Entra ID could be used as the identity provider and would thus contain a directory of user identities. But, a company standardized on Entra ID may still use non-Microsoft SaaS apps like Salesforce for their employees. Importantly, using SCIM can enable the company to automatically create and remove users from applications across a mixed identity vendor stack. Even capabilities like updating user attributes between applications is supported with SCIM. So, instead of manually updating identities across all applications, IT and IAM teams as well as developers can use SCIM to automate and simplify the process.
Conclusion
Automated and efficient workflows to remove unneeded, unused or inappropriate access are the cornerstones of helping security and identity management programs (IGA, IAM, PAM, ITDR, ISPM, etc.) achieve the promise of least privilege. With the Veza Access Platform, unused and over-provisioned access as well as changes in user lifecycle state are automatically surfaced, enabling companies to strengthen their security posture, ensure users are granted correct access based on the tenant of least privilege, and reduce their SaaS licensing costs.




