Celebrating Our Customers—I’m excited to share the story of our shared customer journey with Blackstone to revolutionize IGA with The Veza Way: putting automation and intelligence in IGA!
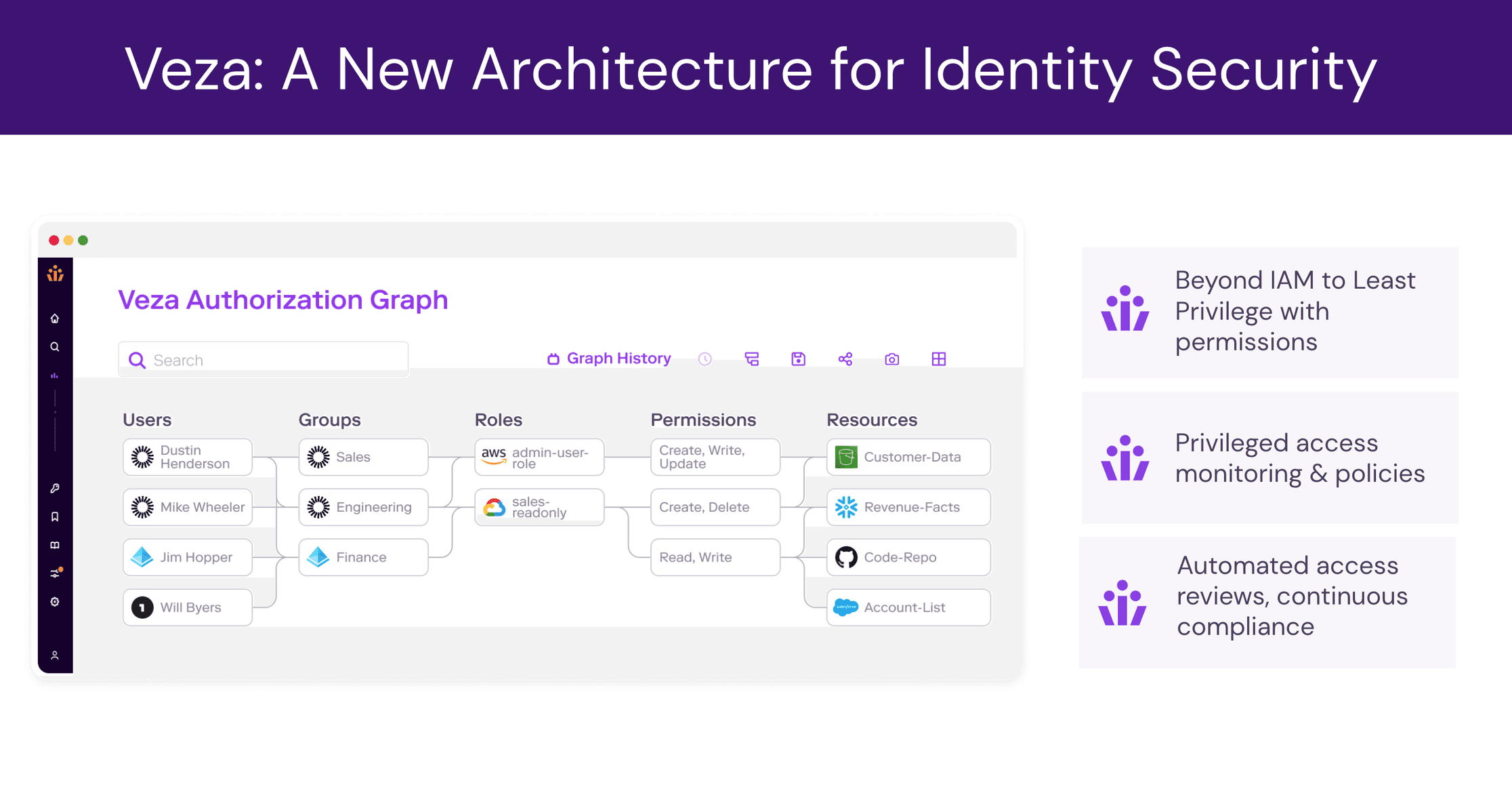
Every organization is juggling a multitude of urgent security initiatives including: data protection, data security, cloud security, ransomware protection, and insider threats. With Veza, our founding belief is that identity security is at the root of all these security initiatives. More specifically, organizations must answer these three questions:
- Who has access to what?
- What can they do with the access?
- Should they even have the access in the first place?
While there have been a lot of identity innovations over the past 2 decades, such as Active Directory, SSO, and MFA, none of these have cracked the code of helping organizations understand who has access to what, and what can be done with that access.
In simpler words, organizations have a goal of applying Zero Trust to achieve the Principle of Least Privilege, but, in reality, organizations are living with over-permissioned access, and a growing burden of access debt. And, this problem only gets worse with every passing week as organizations scale and modify their infrastructure across identities (humans, machine identities, service IDs), SaaS apps, data systems, cloud services, and custom applications.
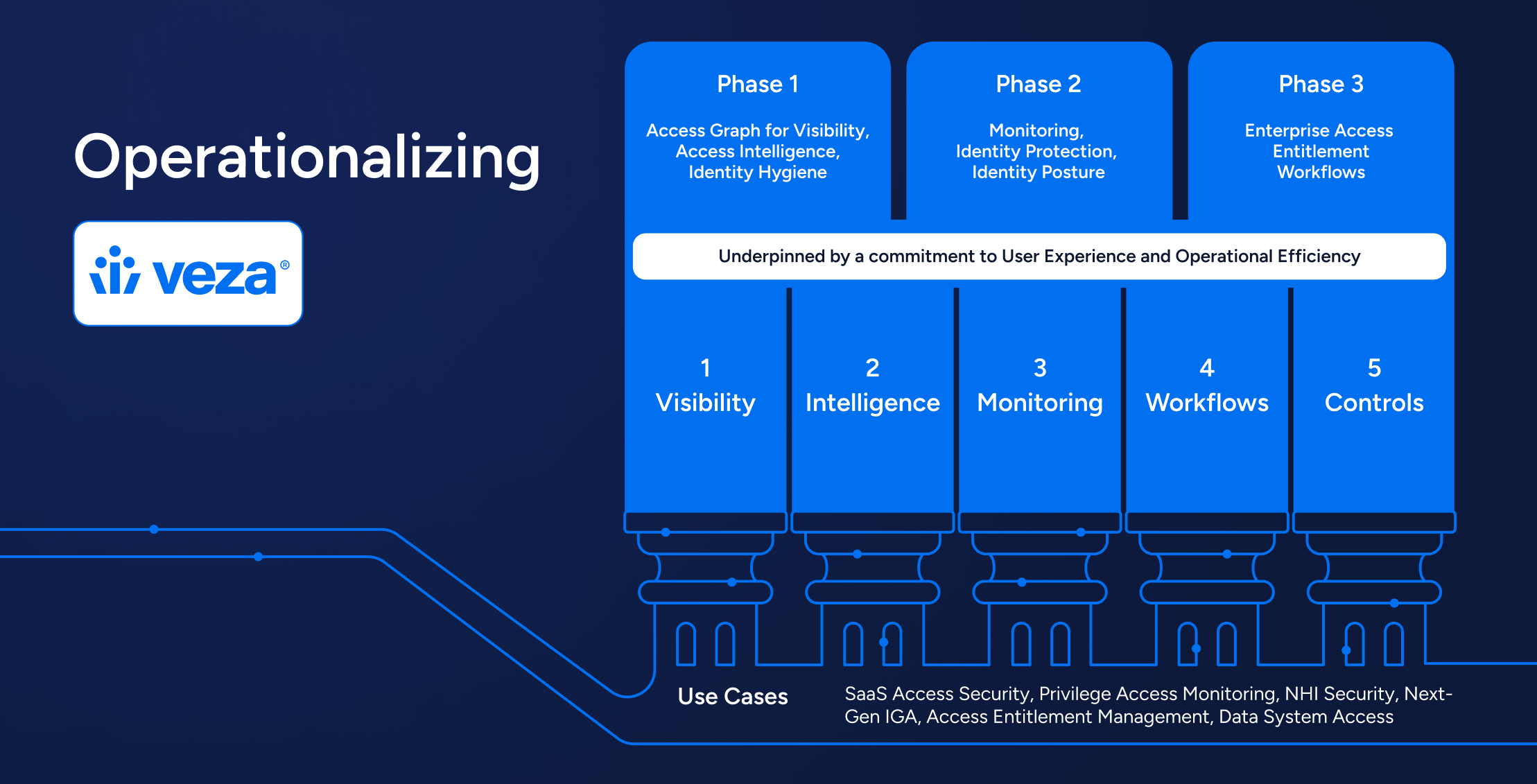
Identity is the weak link in security. The time is now for a second act to modernize identity for the decades ahead. Access permissions are the missing piece. This next act of identity combines previously siloed access permission data, and extracts intelligence from the relationships to solve for critical security and governance initiatives, such as:
- IGA – with automating access reviews and certifications, and AI/ML methods for IGA Intelligence
- PAM with privileged access monitoring
- Securing data lakes and cloud platforms,
- Security for SaaS, on-prem, and custom applications
- Securing access to both structured and unstructured data sets
The era of going beyond IAM is here. Veza understands system specific access permissions and transforms them to solve business problems – access visibility, access creep, privilege creep, credential security, access monitoring, access review workflows, access provisioning, and access authorization — all at enterprise scale and for enterprise systems of custom apps, SaaS apps, data systems, infra, and cloud services.
Organizations undergoing their own modernization of identity—whether driven by a need to modernize their IGA and PAM or to stay a step ahead of cyber threats—stand to benefit from peers who have already embarked on these projects. As a co-founder and CEO, nothing makes me prouder than seeing our customers succeed and thrive. I’m excited to shine a spotlight on Adam Fletcher, Sr. Managing Director and CISO, Blackstone, and the great work they’re doing to secure data across their enterprise resources of SaaS apps, custom applications, data lakes, and data systems.

As CISO of Blackstone, Adam and his teams were a pivotal early customer for Veza. I still remember when we shared our vision and our early products with Adam and his teams, we found ourselves completing each other’s sentences! We had both realized that identity has to go beyond traditional IAM tooling to truly understand identity access from birthright permissions (joiner-mover-leaver), to ad-hoc requests, to the actual use of access permissions. Adam’s product guidance and feedback (as our Board Observer) has been invaluable as we work together to build a secure identity future.
Any organization storing and using sensitive information in the cloud is dealing with an exponential increase in complexity of systems, resources and identities to manage. The traditional crop of IGA and PAM tools are built for the on-prem era, rely on outdated, unscalable architecture, and can’t keep up with the scale of today’s challenges. The Beyond IAM era is here. Meet Veza, The Identity Security Company. Thank you to the Team Veza for their commitment and dedication to revolutionize the identity industry for decades to come.