-
 Data Security
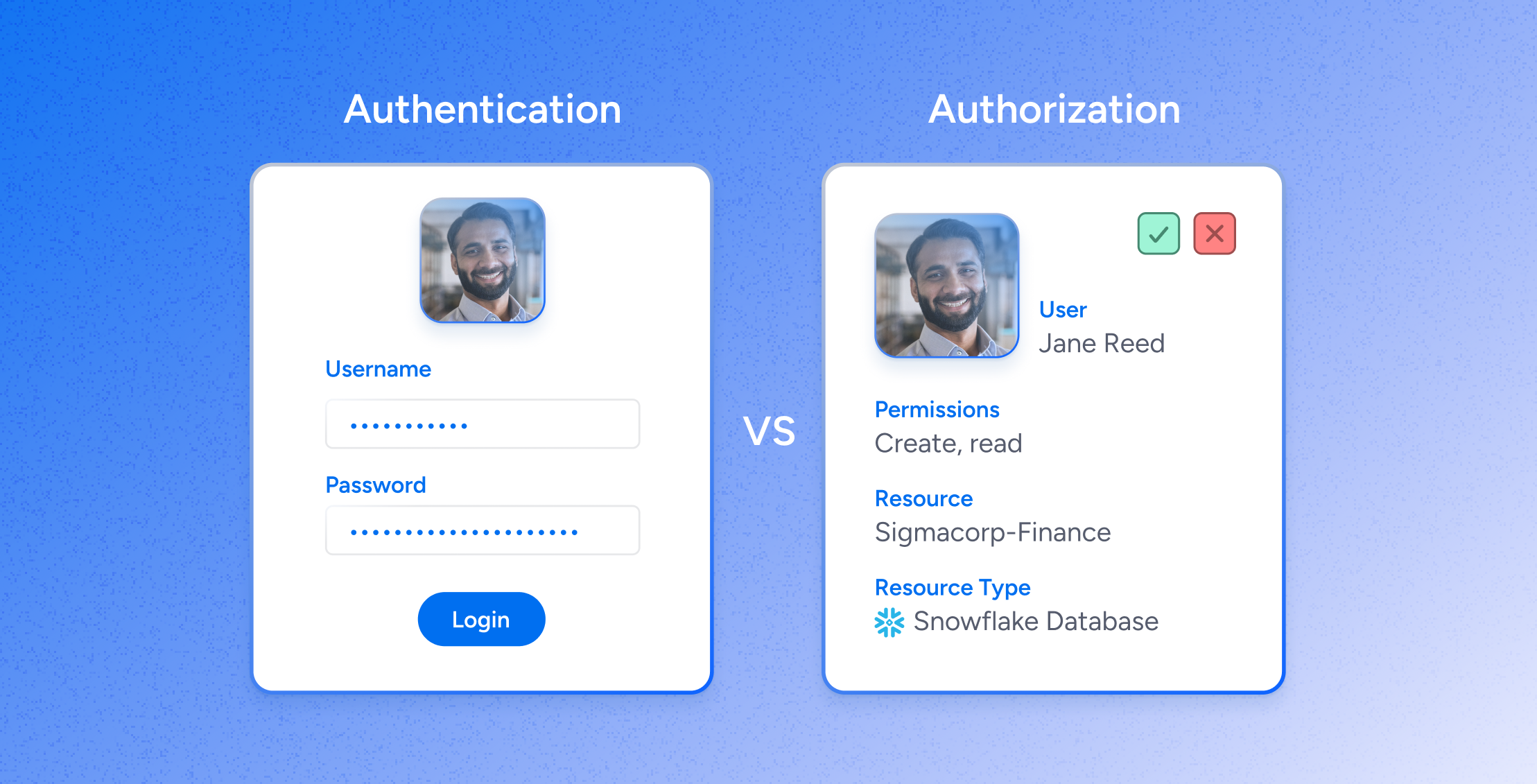
Data SecuritySimplifying Security: The Power of Effective Access Control in Cybersecurity
Learn more -
 Data Security
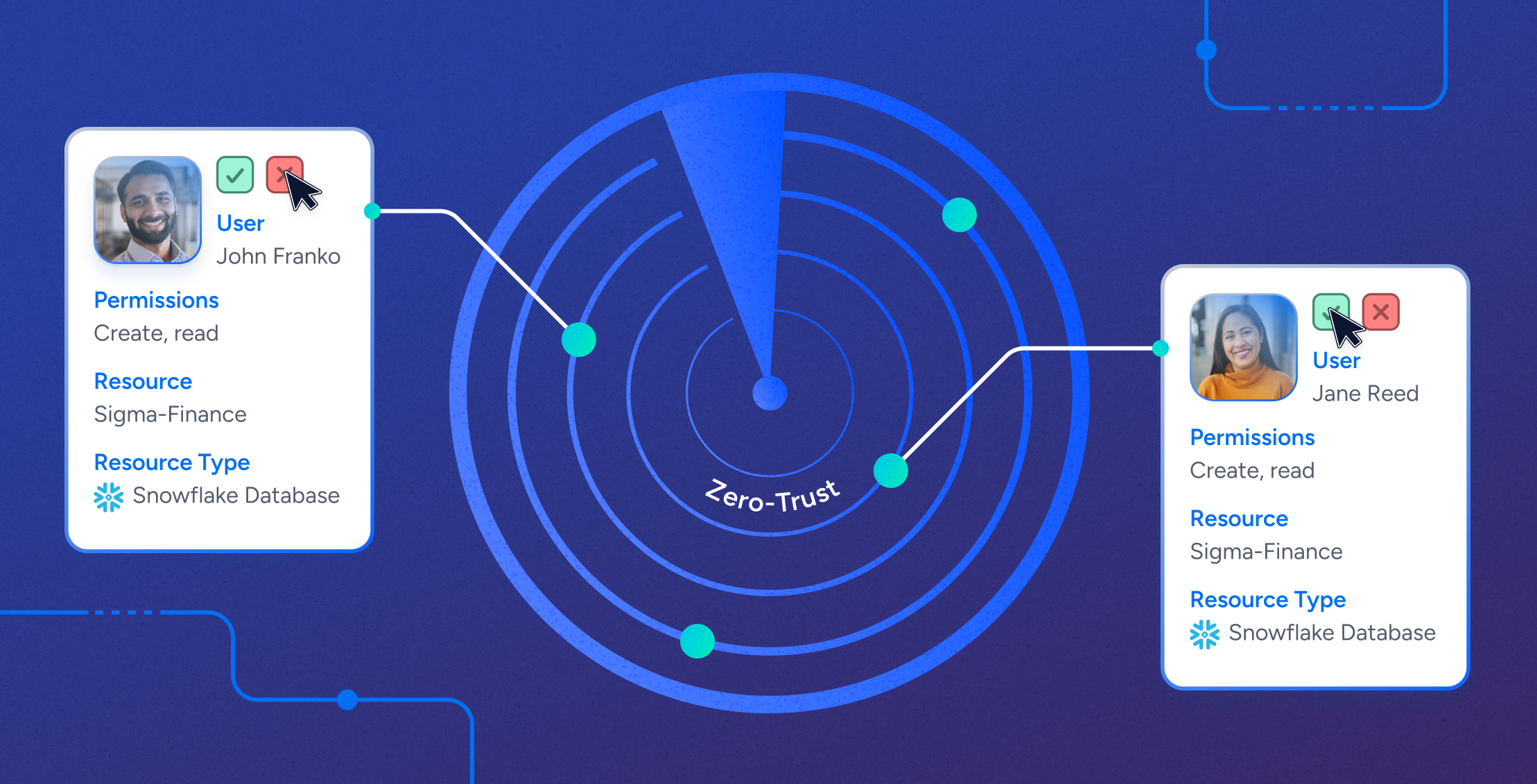
Data SecurityAutomated Access Revocation & Remediation at Scale
Learn more -
 Data Security
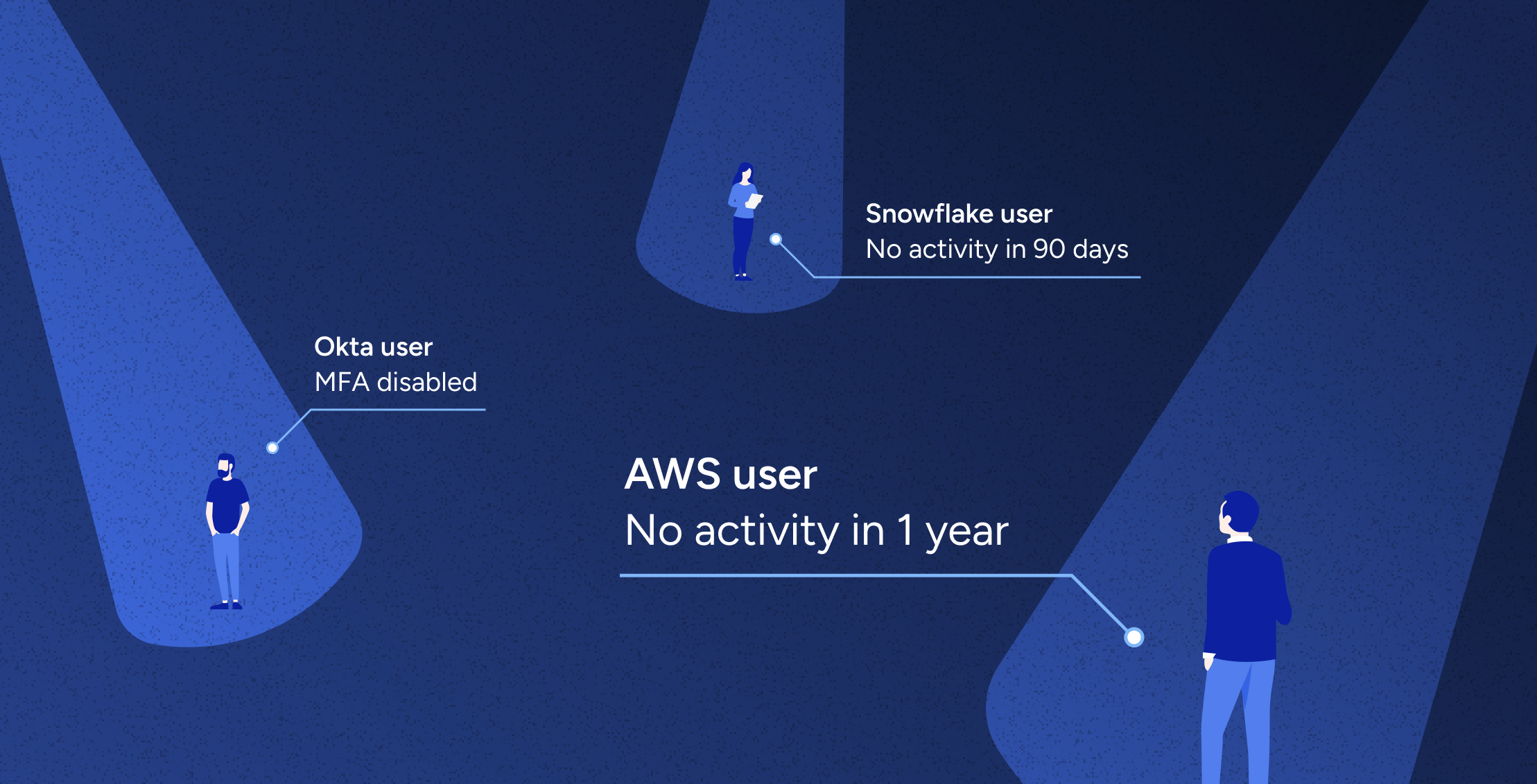
Data SecuritySecuring Snowflake: A CISO’s Guide to Effective Access Control
Learn more -
 Data Security
Data SecurityAccess AI: Introducing the Future of Identity Security
Learn more -
 Data Security
Data SecurityWhat is SaaS Sprawl?
Learn more -
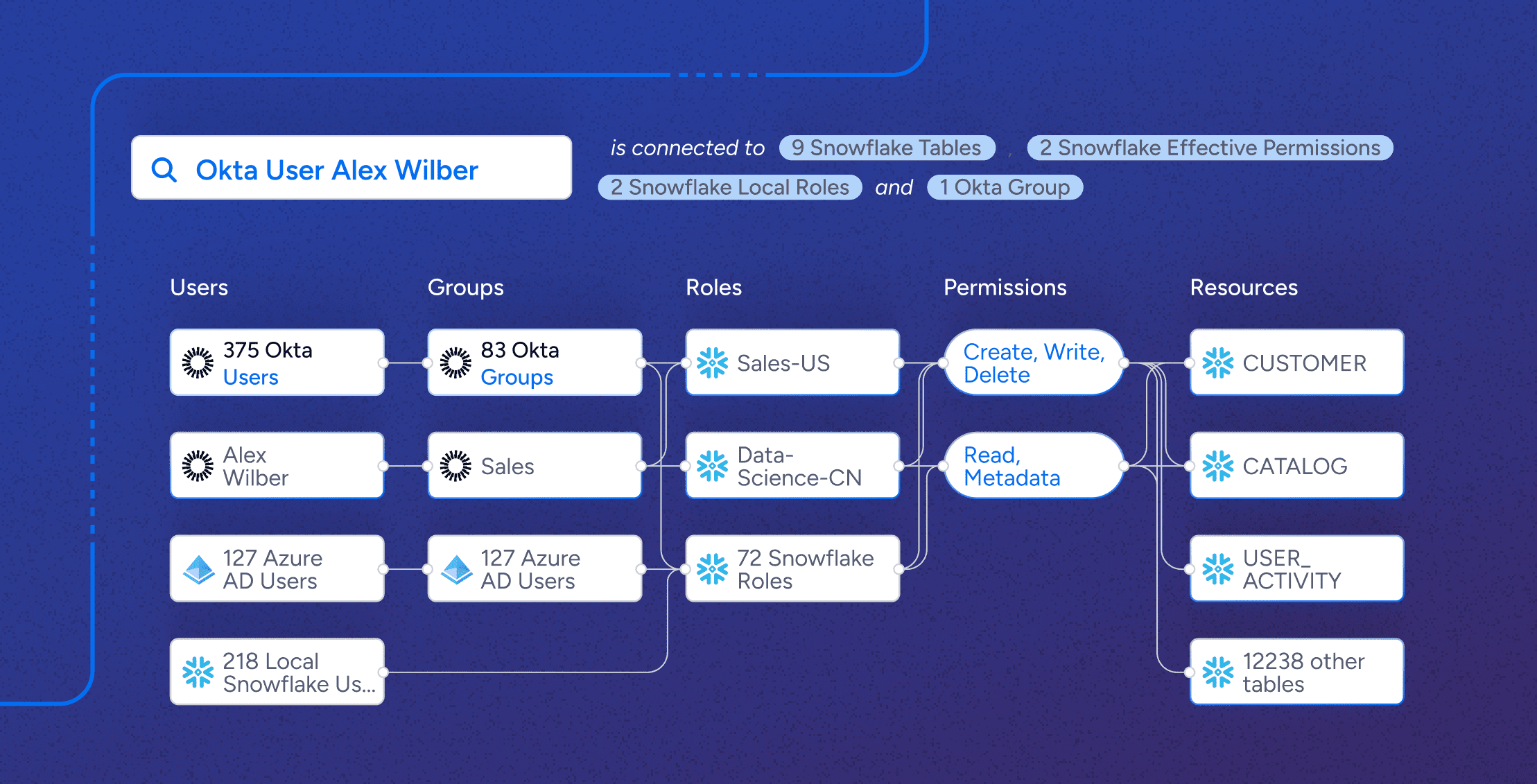 Data Security
Data SecuritySnowflake View Permissions: Who Has Access to What?
Learn more -
 Data Security
Data SecurityWhat is Machine Identity Management? [2024 Guide]
Learn more -
 Data Security
Data SecurityThe Imperative for Identity Security: A Call to Action for the Industry
Learn more