
The Cloud Security Alliance (CSA) has long been at the forefront of identifying and analyzing emerging security challenges in cloud computing. Their latest State of SaaS Security Survey Report, released this month, delivers a comprehensive view of how organizations are managing security in their rapidly expanding SaaS environments. Drawing insights from 420 IT and security professionals across diverse industries and organization sizes, the report paints a clear picture of both progress and persistent challenges in securing our modern application landscape, spanning regulatory zones, industries, and identity types.
What makes this report particularly valuable is its timing. As organizations continue their digital transformation journeys and grapple with emerging technologies like GenAI, understanding the state of SaaS security couldn’t be more critical. The report highlights that while 86% of organizations now rank SaaS security as a high priority and 76% are increasing their security budgets, significant gaps remain in how we approach this challenge.
When I read through the Cloud Security Alliance’s latest State of SaaS Security Report, one thing became crystal clear: we’re still fighting yesterday’s security battles with yesterday’s tools. And nowhere is this more evident than in how we manage identity and access.
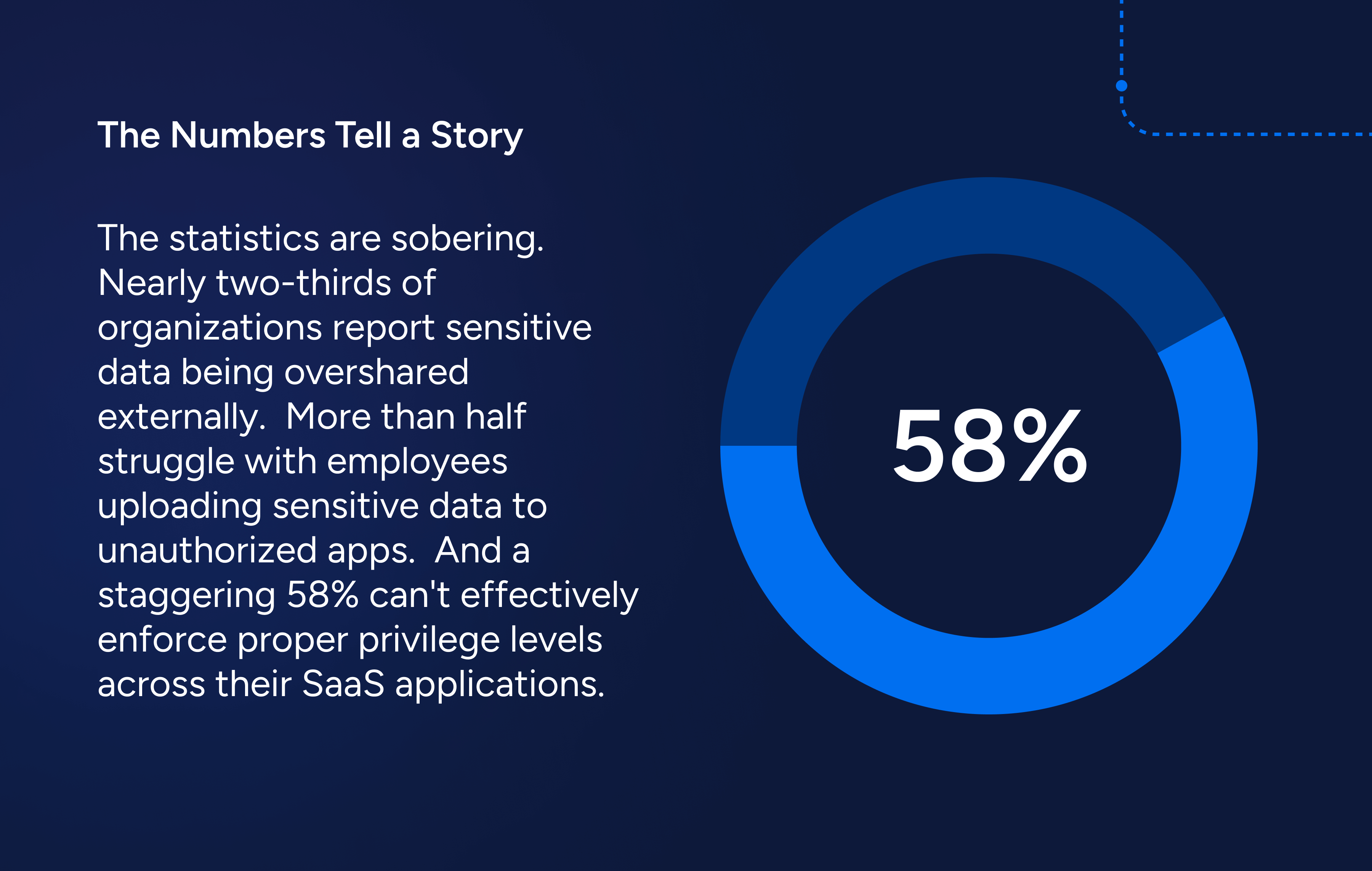
Even more concerning, the report reveals that HR platforms and marketing automation tools – which often contain highly sensitive employee and customer data – are primarily managed outside of IT in 51% of organizations. Developer environments aren’t immune either, with source code management tools like GitHub and GitLab increasingly becoming targets for oversharing and misconfigured access.
But here’s what really caught my attention: while organizations are investing heavily in SaaS security (76% increased their budgets this year), they’re still missing the forest for the trees.
Living in a Multi-Everything World
Here’s the reality we need to face: We don’t just live in a multi-cloud world anymore. We live in a multi-everything world. Sensitive data isn’t just in SaaS applications – it’s in cloud infrastructure, data lakes, and yes, still in on-premises systems. Employees aren’t just using one or two apps – they’re using dozens, often without IT’s knowledge. Supply chains require growing numbers of diverse partners to access systems and exchange data. And it’s not just human users anymore – non-human identities like service accounts, API connections, and AI tools are proliferating faster than we can track them.
The Old Playbooks Don’t Work Anymore
Traditional approaches to identity and access management were built for a simpler time. They were designed when we could draw clear lines between inside and outside, when we could count our applications on two hands, and when “identity” meant “human user.” When the most important measure of success for I&AM was service levels in granting access or quickly changing passwords. That world is gone.
Today’s reality? According to the CSA report, 46% of organizations can’t effectively monitor non-human identities. Over half lack automation for basic identity lifecycle management. And with the explosive growth of GenAI tools and eventual growth of Agentic AI, these challenges are only accelerating.
A New Approach for a New Era
What’s needed isn’t just better tools – it’s a fundamentally different approach to identity security. One that:
- Spans all platforms and environments, not just SaaS
- Treats human and non-human identities with equal rigor
- Provides real-time visibility into who (or what) has access to what
- Enables automated enforcement of least privilege
- Understands the context of access relationships
The Path Forward
The most successful organizations I work with have realized that identity isn’t just another security tool – it’s the foundation of their entire security strategy. They’ve moved beyond siloed solutions and point products to embrace a unified, identity-centric approach to security.
This isn’t just about better compliance or reduced risk (though those are important benefits). It’s about enabling your organization to move faster, adopt new technologies confidently, and say “yes” to innovation while still protecting what matters most.
The Wake-Up Call
The CSA report should serve as a wake-up call. The risks are real, they’re growing, and our traditional approaches aren’t keeping up. But there’s good news too: by putting identity at the center of our security strategy and adopting modern approaches to identity security, we can help organizations regain control and confidence in their security posture.
The question isn’t whether to modernize your approach to identity security – it’s how proactively you can get started.
Appendix – Key Findings Summary
- Key Finding 1:SaaS Security Is a Growing Priority as Organizations Ramp Up Investment
- Key Finding 2: Sensitive Data in SaaS Is at Risk Due to Poor Visibility and Weak Access Controls
- Key Finding 3: The Rise (and Risks) of Decentralized SaaS Adoption and Management
- Key Finding 4: Human Identity Management in SaaS Remains a Persistent and Expanding Security Challenge
- Key Finding 5: Non-Human Identities & SaaS-to-SaaS Integrations Are an Expanding Security Blind Spot
- Key Finding 6: Overconfidence in Current SaaS Security Strategy Masks Gaps






