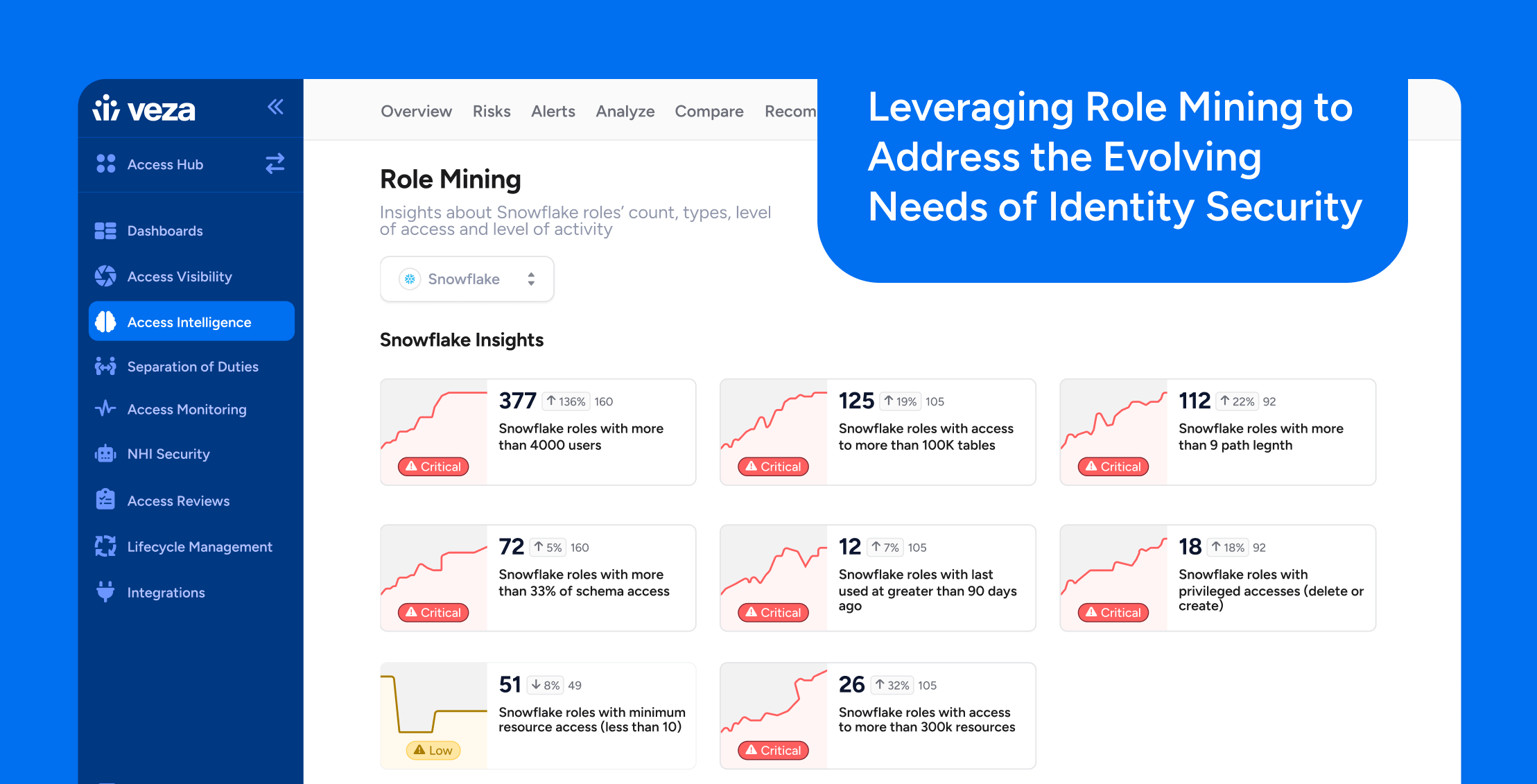
Setting the Stage
Managing user access has always been a challenge, but in today’s hybrid, multi-cloud environments, it’s becoming a full-blown security risk. As organizations adopt more applications and store increasingly sensitive data across complex infrastructures, ensuring the right people have the right permissions at the right time is harder—and more important—than ever.
That’s where role mining comes in. By analyzing how access is used across systems, role mining helps security teams detect patterns, eliminate unnecessary permissions, and enforce the principle of least privilege at scale. It’s not just a tactical fix—it’s becoming a strategic enabler for modern identity governance.
I was recently reading an article on role mining, and it struck me how much this technique aligns with the work we’re doing at Veza. We see role mining as a foundational part of access management automation—one that helps SecOps teams regain control, reduce risk, and stay ahead of evolving compliance demands.
Role Mining: Identity Security’s Hidden Workhorse
Role mining is more than just analyzing permission logs. Done right, it reveals how people use access across systems and helps define roles that match real-world job functions. This insight enables organizations to define roles that reflect real-world job functions—streamlining access management, reducing risk, and supporting the principle of least privilege.
Take a finance team, for example. Role mining might show that 80% of users rely on the same five tools and reports. Instead of managing each permission individually, you can define a role that bundles exactly what they need—nothing more, nothing less. That keeps your access footprint clean and audit-friendly.
Platforms like Veza take this a step further. We don’t just identify roles—we evolve them. Our platform ingests real-time access data, aligns it with organizational context, and adapts roles dynamically. The result: less manual work for IT, better compliance posture for security teams, and access policies that move at the pace of your business.
How Veza Empowers Role Mining with AI and Machine Learning
The future of role mining is being shaped by the rapid adoption of artificial intelligence (AI) and machine learning (ML) across the identity security landscape. These technologies are helping organizations automate the detection of over-permissioned users and recommend role adjustments based on evolving business needs and real-time data.
AI-driven tools can identify redundant permissions, eliminate unnecessary access, and ensure that the principle of least privilege is always maintained. This proactive, data-driven approach minimizes security risks, reduces exposure to sensitive information, and ensures users only access the resources they need.
Solutions like Veza take these AI and ML capabilities further by continuously monitoring access patterns, adapting to shifts in business roles and security requirements. By leveraging real-time data and automation, Veza ensures that role mining remains dynamic, helping organizations optimize their access governance while maintaining compliance and security.
Business Benefits of Modern Role Mining
Role mining offers organizations measurable improvements in their identity security posture. When embedded within platforms like Veza, these benefits become scalable and actionable, providing organizations with the tools needed to manage access at scale while ensuring compliance and security.
Here’s how the core advantages of role mining translate into tangible improvements:
- Enhanced Security: Role mining identifies and eliminates over-permissioned users, ensuring that permissions are tightly aligned with job roles. This reduces the risk of unauthorized access or data breaches.
- Improved Efficiency: Traditional permission management can be manual and time-consuming. Role mining automates the process, enabling SecOps teams to focus on more strategic tasks while reducing human error.
- Regulatory Compliance: Role mining ensures that access controls are in line with key industry regulations like SOX, HIPAA, and GDPR. Platforms like Veza enhance this by automating auditing and reporting, helping organizations stay compliant with minimal effort.
- Cost Savings: Automating the management of access permissions eliminates unnecessary access, reducing operational overhead and optimizing resources, resulting in significant cost savings.
- Continuous Visibility: Role mining provides deep insights into access patterns and potential vulnerabilities. With near real-time monitoring, SecOps teams maintain visibility, allowing them to quickly identify and address security gaps.
A Higher Vision of Identity Security: The Evolving Landscape
The future of identity security is moving toward more adaptive and intelligent governance models that evolve in real time. Traditional identity management tools, while foundational, often struggle to keep up with the dynamic nature of modern IT environments. As organizations scale and face increasingly complex threats, static policy enforcement and role-based access controls can fall short in addressing the full scope of security challenges.
Emerging trends are pointing toward solutions that go beyond static policy enforcement, incorporating behavioural context, near real-time access verification, and AI-driven insights. These next-generation platforms provide continuous monitoring and can automatically adjust to changes in user behaviour and access patterns, helping organizations mitigate risk without manual intervention.
The focus is shifting toward creating systems that are more adaptive, scalable, and resilient. Organizations are now looking for identity security frameworks that can respond in real-time to emerging threats and evolving business needs. The integration of zero-trust principles and contextual access management is central to this transformation, offering more granular control over who can access what, when, and why.
In this evolving landscape, identity security will increasingly rely on automated policy enforcement and intelligent insights. As businesses continue to face new risks, the tools and frameworks they adopt will need to be flexible and forward-thinking, helping them stay ahead of emerging threats.
Advancing Identity Security with Adaptive Governance
As IT environments become more complex, managing user access is an ever-growing challenge. Role mining is a key component of effective access management, but it’s only one part of the solution. Through AI-powered automation and continuous role refinement, organizations can transform role mining from a reactive task into a proactive, adaptive strategy for managing access in near real-time.
From Policy to Practice: What Comes Next
Modern identity governance demands more than rules—it needs intelligence, automation, and agility. Role mining, powered by real-time data and AI, is one of the most powerful tools in the SecOps toolkit. But it works best when paired with a platform that evolves alongside your business.
By shifting from static roles to dynamic, adaptive governance, organizations can reduce risk, speed up audits, and free up security teams to focus on what matters most: staying ahead of threats.
Want to dig deeper? Here are a few resources to explore:
- What is Identity Security? – An introductory guide to understanding the complexities and importance of identity security in today’s digital landscape.
- Access Intelligence – Learn how Veza’s Access Intelligence uses AI to detect privileged users, dormant permissions, policy violations, and misconfigurations across enterprise systems.
Platform Overview Data Sheet – Dive deeper into Veza’s platform capabilities, including monitoring privilege, investigating identity threats, automating access reviews, and bringing access governance to enterprise resources.
About the Authors
This article was co-authored by Matthew Romero, Technical Product Marketing Manager at Veza, and Rob Rachwald, VP of Marketing at Veza. Together, they bring deep expertise in identity security, cybersecurity marketing, and go-to-market strategy.
Matthew’s background includes a wealth of experience in identity-centric security, hybrid cloud environments, and SecOps. He focuses on translating complex identity access challenges into clear, actionable insights for security leaders. Matthew’s expertise lies in bridging technical depth with strategic communication, helping organizations defend against modern threats.
Rob has over two decades of experience in cybersecurity marketing, having led go-to-market efforts at companies like Palo Alto Networks, FireEye, and Fortinet. His work spans across nearly every facet of the security landscape, including identity security, endpoint protection, and threat intelligence. Rob is passionate about simplifying complex security concepts into impactful, strategic narratives that resonate with CISOs and security teams.
Together, Matthew and Rob bring a unique blend of technical and strategic perspectives, helping security leaders build proactive defenses against evolving identity-driven threats.





