Introduction
Just-in-time (JIT) access is a powerful access management concept built around the principle of granting users the access they need only when they need it – in other words, access is granted just in time. There are a number of positive outcomes associated with JIT access – among the most powerful being that JIT reduces standing privilege amongst users, especially for privileged operations or infrequently accessed systems and applications, translating to significant cost, security, and compliance benefits to the organization.
However, existing JIT access is more complicated to deploy and orchestrate than traditional forms of access management initially plus it requires changes in user behavior as well as active involvement from business stakeholders to ensure the process works successfully. That said, the security and compliance benefits realized by the organization when JIT access is successfully implemented – leading to no persistent access – are quite meaningful with the added bonus of significant cost savings as well.
Shortcomings of Traditional Access Models
With traditional access methods, users are granted durable permissions to resources in systems or applications. Durable, in this sense, means that a user’s permissions remain relatively static and unchanging. If permissions do change, then there is a natural tendency for users to amass more access over time, as users have a tendency to acquire more, but not lose, permissions over their lifetime in an organization.
As such, there are several problems with this traditional access model:
- Users end up amassing significant and ever-increasing amounts of standing privilege over time – this frequently results in users having drastically more privilege than they actually need to perform their job on a day-to-day basis.
- Standing privilege per user is reviewed infrequently – user access reviews occur anywhere from quarterly by the most diligent organizations to never by other organizations. Even when an organization regularly reviews access, there is always the possible outcome of managers and application owners “rubber stamping” user access recertifications due to uncertainty, fear of disrupting business processes, or simply wanting to avoid the possibility of preventing somebody from doing their job. Regardless of whether organizations have rigorous access review programs or not, the uncertainty (or unwillingness) of managers and application owners to reject user access at review time is very real and another reason why ever-increasing amounts of standing privilege build up over time.
- Maintaining large amounts of standing privilege is extremely risky – when user accounts with large amounts of standing privilege get compromised, the risk that attackers can move laterally, steal data, or compromise critical systems or infrastructure increases dramatically. The same argument applies to the malicious insider; as he (or she) amasses increasing amounts of privilege across systems and applications, the amount of havoc that this malicious insider can inflict on the organization grows commensurately.
- Maintaining standing privilege is unnecessarily expensive and wasteful – with more and more organizations transitioning to subscription-based application licensing models with per-user meters, it is not just expensive, but wasteful, to have users provisioned and licensed for applications that they’re just not regularly and actively using.
Of course, in the traditional access model, administrators or application owners can always eliminate or modify any given user’s permissions at any time, but in reality, this is a rare occurrence, usually tied to the organization’s user access review process or, in the worst case, never occurring.
Benefits of JIT Access
The core principles of JIT access is that users request access to applications, privileged entitlements, or resources when they need access. Depending on the type of access being requested, the request may be subject to an approval workflow. For example, the user’s manager and an application owner in Sales Ops might be asked to approve a user’s request to access Salesforce. Finally, granted access may be time-limited, meaning that, if approved, access is granted for a limited period of time after which access is automatically revoked.
Compared to traditional access management models, there is more complexity to JIT access, including the need for users to request the access they require, establishing approval workflows, and automation to grant and revoke access. Moreover, users and other stakeholders, such as managers, application owners, and administrators, are required to be much more actively involved in the JIT access management process. But the cost, security, and compliance benefits are significant.
Some of the cost benefits of JIT access include:
- Minimizing the set of applications provisioned to users who don’t fully utilize those applications. This can significantly reduce annual software and SaaS licensing expenditures in many organizations.
- Ensuring that when a user does legitimately need temporary access to a costly application, she or he can efficiently obtain access for enough time to complete their task or project.
- Ensuring that license seats no longer in active use for a costly application are relinquished in a timely manner and made available for the next user requiring access.
All of these benefits combined help organizations keep their software licensing costs under control by maximizing utilization of paid license seats, especially for costly per-seat applications, and ensuring users with legitimate access needs always have access when they need it.
Similarly, JIT access brings numerous security benefits to organizations, including:
- Users only maintain the most common, baseline access privileges on a durable basis. This helps minimize standing privilege amongst users, which reduces the attack surface area since privileged access is ephemeral.
- Related to the previous point, JIT access also decreases the risk and impact of lateral movement when attackers inevitably end up compromising user accounts. For example, it is more challenging, though certainly not impossible, for attackers to move laterally from a lesser privileged account. Similarly, even if lateral movement is possible, maintaining an overall lower level of standing privilege across all users’ accounts thwarts and slows down attackers.
- Since JIT access requires multiple steps, including an access request, approval workflow, access grant, and revocation, the process is highly auditable. In a well-implemented JIT access management system, each step of the process is logged in an immutable audit trail making it easier to trace in a non-repudiable manner:
- Who requested what access
- Why was the request justified
- Who approved the request
- When the access was granted
- When the access was revoked
This level of auditability is not only crucial from a compliance perspective but also incredibly useful for forensics and other investigations.
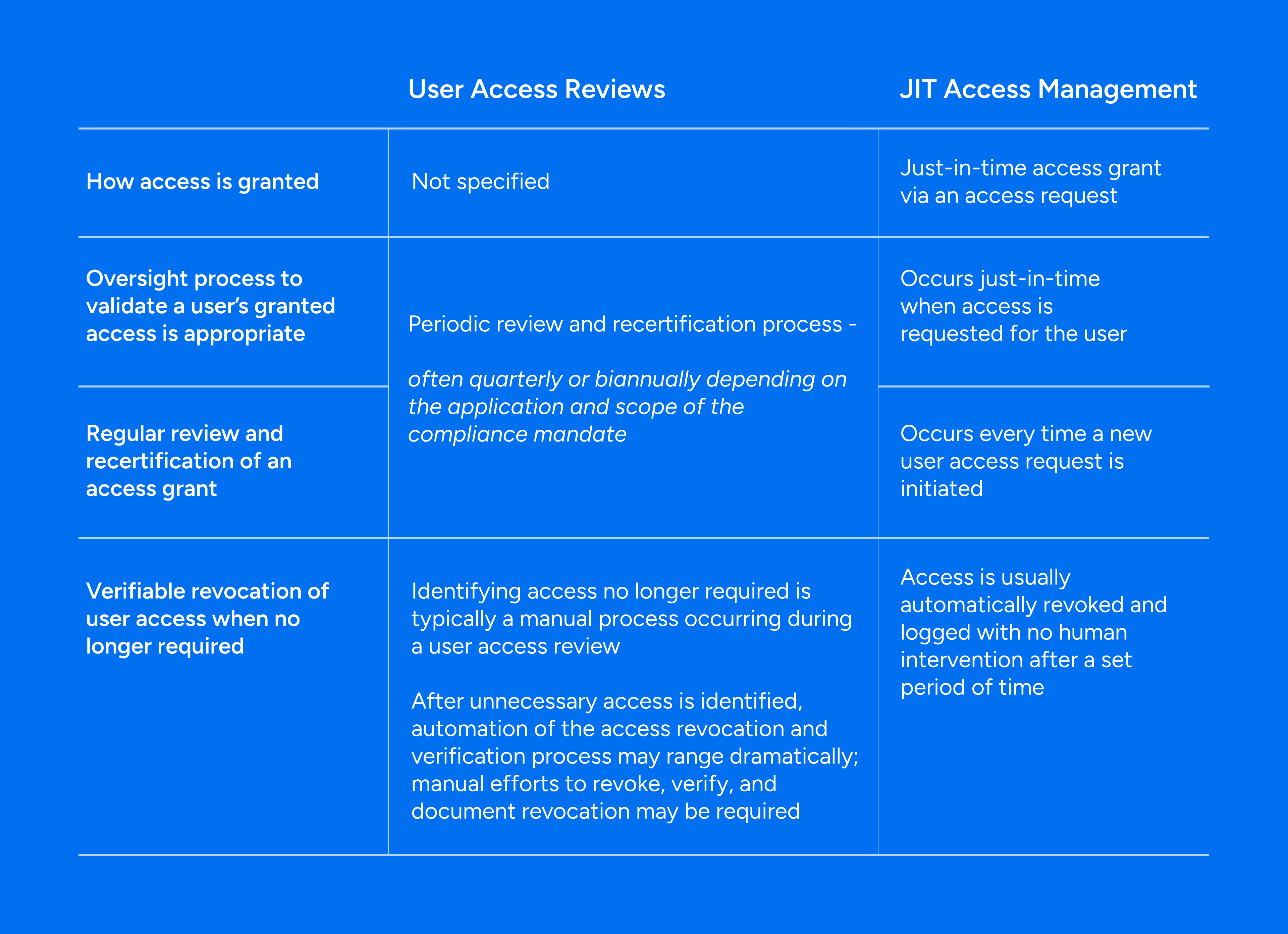
On this last point, organizations, especially heavily regulated ones, can realize significant compliance benefits with JIT access – particularly in the area of access governance. For instance, JIT access, just like regularly scheduled user access reviews, can be rolled out as a critical business process that organizations can employ to help drive the organization closer to the principle of least privilege. Interestingly, however, JIT access can also simplify and minimize the scope of an organization’s existing access review program. For instance, JIT access management, like periodic user access reviews, helps organizations meet regulatory requirements around ensuring granted access is appropriate and necessary by the user to perform his or her job function, the continued need for the user to maintain the access is regularly assessed, and access is verifiably removed when no longer needed by a user. However, the approach for achieving these objectives is quite different for JIT access management vs. user access reviews and can be summarized as below:
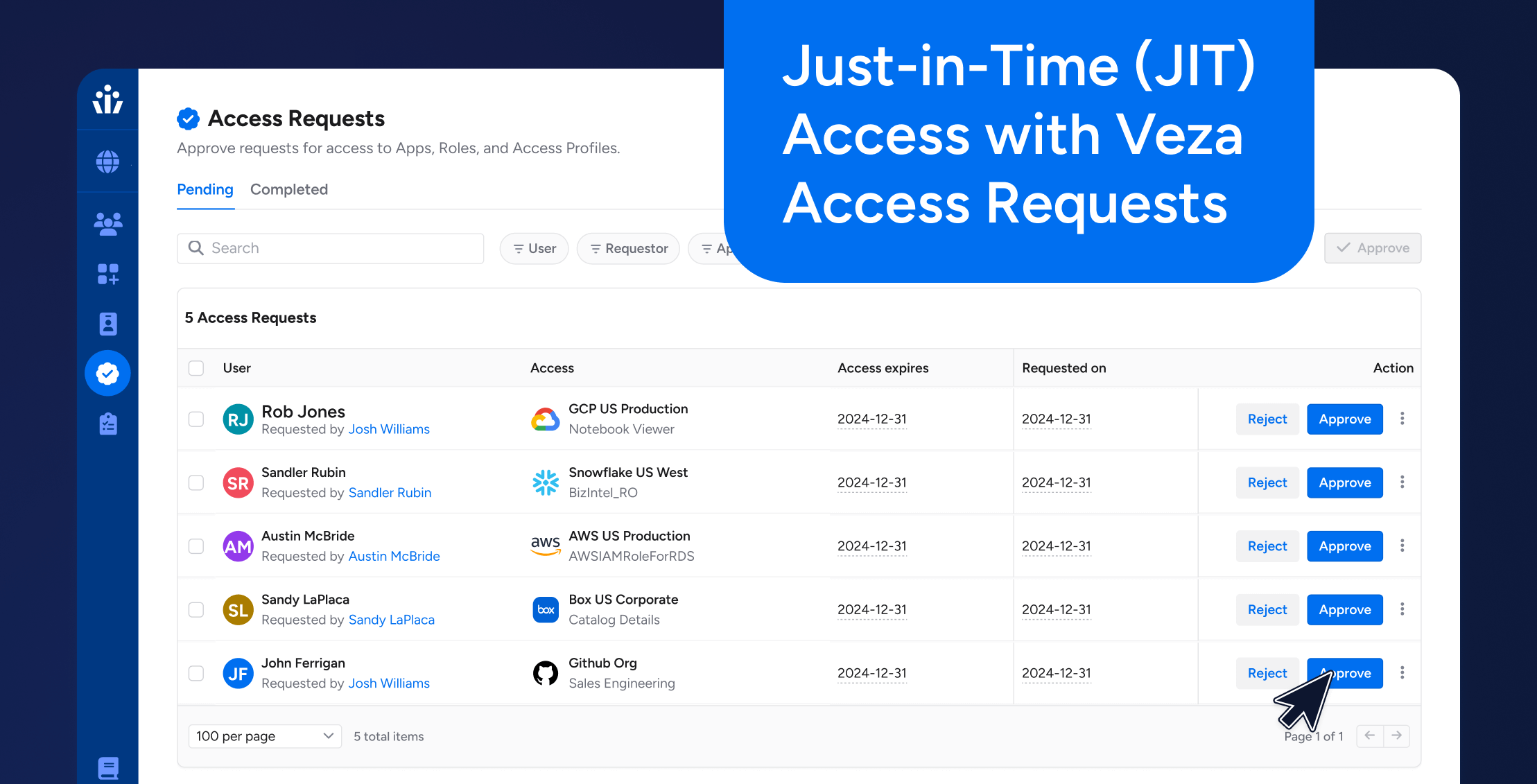
Key JIT Access Concepts in Veza Access Requests
Veza Access Requests is designed to help organizations manage, orchestrate, and fulfill just-in-time (JIT) access requests. In concert with our Veza Lifecycle Management product, Veza Access Requests is focused on the just-in-time access fulfillment scenario as opposed to policy-based provisioning / deprovisioning of birthright user access.
There are seven fundamental concepts in Veza Access Requests, including:
- The Catalogue contains the list of requestable access “items”. The Catalogue is generally accessible to all organizational users by default through Veza’s self-service Web-based Access Hub – almost like an app store, except that the “items” are published by Veza administrators and application owners. Future channels where the Catalogue will be accessible include the organization’s ITSM system and modern communication tools like Slack.
- Catalogue items represent specific grants of access that can be requested by users. Access Profiles are used to define catalogue items. Catalogue items composed of a single entitlement are called Entitlements, whilst items composed of multiple entitlements (across one or more applications) are called Bundles. Catalogue items also can have their own metadata, such as user-visible descriptions, icons, labels, and more. Visibility of Catalogue items in the Catalogue can differ between different groups of users – this is dictated by policy.
- Access Profiles dictate the specific application and entitlement combinations to be granted to a user upon successful approval of an access request. Of course, Access Profiles can do a lot more.
- Policy governs the rules for exposing Catalog items, sets time limits on user access grants, defines how much leeway requesters have to request longer durations of access or access extensions, defines required approval workflows and/or auto-approval/auto-reject criteria, and dictates how user accounts and access are provisioned (and ultimately deprovisioned).
- Approval workflows are an ordered list of approvers required to approve an access request. Approval workflows are defined in policy. Auto-approval/auto-rejection criteria can also be set. Additionally, one or more approvers can be specified at differing levels of approval, such as the beneficiary user’s manager must approve the request first followed by the application owner.
- Access requests are created by users, typically starting from the Catalogue. User access requests for Catalogue items can be either first-party (i.e. I am requesting access for myself) or third-party (i.e. I am requesting access on behalf of somebody else). Once access requests are created, they either get auto-approved/rejected or routed to policy-defined approvers (via notification) for review and decision-making. All access requests, decisions by approvers, and, if approved, access grants are permanently logged.
- For access that is presently granted, access revocations can be initiated manually by the approver or a Veza administrator. The system will also automatically revoke access after the policy-defined access duration is reached. All access revocations, irrespective of who initiated them, are permanently logged.
In order to support these key JIT access concepts, Veza Access Requests also includes comprehensive management framework in the Veza console designed to create and manage Access Profiles and Catalog items, author policies, view and manage user-initiated access requests, facilitate approval workflows, trigger manual access revocations, view and export audit logs, monitor dashboards, and more.
Requester and Approver Experience
Veza has designed both the requester and approver experience to be simple and intuitive.
The requester experience starts with a user visiting the Catalogue in the Access Hub. Within the Catalog in the Access Hub, the requester can search for Catalog items relevant to the JIT access that they seek – not unlike an app store. Catalogue items may have specific descriptions, icons, and labels attached to keep the catalogue organized as well as make searches for specific items easy. Requests can be made for oneself (i.e. first-person request) or for another user (i.e. third-person request), such as one’s direct report or colleague.
Requesting access to a published Catalogue item is simple. Requesters simply click on the Catalogue item and then select either Request Entitlement or Request Bundle, depending on the type of item. Next, requesters need to provide justification for their request and, if allowed, set a duration of access (within the range specified by policy). At this point, the access request will be routed for approval.
For access requests not automatically approved or rejected, they will be routed to one or more designated approvers. The specific approvers and order of approval are dictated by policy, so it can vary depending on the Catalogue item requested, but in general, approvers are notified that they have a pending access request requiring their action. Presently, approvers make their decisions in the Access Hub, but this will expand in the future to include options like decisions within the approver’s Slack workspace. Approvers can include any or all of the following: beneficiary’s managers, application owners, entitlement/bundle owners, system administrators, and named individuals. In order for an access request to be granted, approvers at all levels must unanimously approve the request. Any dissenting decision by an approver will reject the access request.
If an access request is approved, the request will transition into an access grant. For access grants, the Veza platform will automatically initiate an access provisioning to the target application(s). If necessary, the Veza platform will provision a new or secondary user account in the target application(s). Regardless of whether the beneficiary has an existing account in the target applications or a newly provisioned account, the next step is to assign the correct (set of) role(s), group(s), or other entitlement(s) to the user’s accounts across the target application(s).
All access requests, as well as every stage of the approval process and, ultimately, access grants, are permanently and immutably logged by Veza Access Reviews.
Access Revocation
Granted access requests can be revoked under two circumstances with Veza Access Reviews:
- Access is automatically revoked at the end of the specified access duration.
- Access is manually revoked early, either by the approver, requester, or administrator
At present, manual access revocation can be initiated from the Access Hub, Veza console, or via API.
Like access requests and grants, all access revocations are permanently and immutably logged.
Implementation Considerations
When implementing Veza Access Requests, there are several important considerations.
First, Veza Access Requests works hand-in-hand with Veza Lifecycle Management, though the products are intended for different access provisioning (and deprovisioning) use-cases. However, policy and Access Profiles are shared “building blocks” between the products. For instance, a common policy dictates how new user accounts should be created in target applications, irrespective if provisioning is triggered by Veza Access Requests or Veza Lifecycle Management. This ensures that user accounts in target applications are created consistently irrespective if access is being provisioned as part of a birthright provisioning process or via JIT access.
Access Profiles are also shared between both products, though Access Profiles do define if they’re to be used for birthright provisioning vs. JIT access provisioning. If utilized for the latter, then the Access Profile must be associated with an Access Request policy that defines the duration of JIT access, the approval workflow, and more.
As established, all access requests, approval decisions, access grants (if applicable), access revocations (if applicable), and access expirations are permanently and immutably logged on the Veza platform. These logs can be used as a record to prove when access was requested, approved/denied, granted, revoked or expired. The logs are very specific in terms of the actors involved (i.e. requester, beneficiary, approver(s), and revoker) as well as time and date when actions took place. These events are also summarized on the Lifecycle Management Overview dashboard. Importantly, individual events occurring on the target applications, such as creating the specific user account, adding/removing entitlements to accounts, etc., are also logged and are very useful for diagnostic and forensic purposes.
Mitigating Challenges When Implementing JIT Access
For many organizations, the cost, security, and compliance benefits of JIT access are compelling, but that doesn’t mean there aren’t implementation challenges. The biggest challenge is often with the users and business stakeholders themselves.
First, users and business stakeholders need to be trained since they’re now active participants in the JIT access management process. Most importantly, users will need to become accustomed to the fact that a) they will no longer maintain standing privilege in certain applications and b) access to these applications or access at certain elevated privilege levels will require requests for limited-time access. Obviously, users will need to know the basics, such as how to find and search the Catalogue and submit access requests (though Veza’s easy-to-use Access Hub makes this process quite simple and intuitive).
Although one of the clearest strengths of JIT access is minimizing the risk of standing privilege, the corresponding downside is increased waiting times for users between the period that they realize that they require access to a specific application and that access actually being granted. This can be mitigated in a couple of ways:
- Organizations should take a risk-based approach to approval policy. As much “mundane” JIT access should be auto-approved as possible. Even more sensitive JIT access should be subjected to the minimal number of approvals to just meet the organization’s security policy and compliance benchmarks. In other words, why require 5 levels of approval when only 2 levels of approval will suffice?
- In the case where multiple approvals are required in order to grant JIT access, organizations should thoughtfully consider whether approval notifications should be sent to all approvers at once – noisier, but decisions are theoretically made quicker – or sequentially – takes longer, but cuts down on the decisions being requested be higher level approvers. There are pros and cons to both of these approaches, and the best options vary depending on the organization.
- Organizations will also need to carefully consider their policies for escalations, exceptions, and administrative “break glass” scenarios. Again, this is yet another example of one size not fitting all.
Similarly, business stakeholders, as approvers, must be trained on their responsibilities – how to urgently review and respond to access requests. Compared to traditional access management (combined with periodic access reviews), business stakeholders like managers, application owners, and application administrators will be required to be much more active and responsive in the adjudication of access requests (though this potentially comes with the benefit of fewer and shorter access reviews each quarter).
Finally, both parties will also have to get used to access being temporary, meaning a constant stream of access requests and approval workflow tasks. For many organizations, this is going to be a radical departure for their users and business stakeholders used to traditional access management..
Overall, this may be a big cultural shift for some organizations so the roll-out of JIT access should proceed thoughtfully.
Conclusion
JIT access offers organizations significant advantages over traditional access models. By granting users access only when needed, JIT access:
- Minimizes standing privilege
- Reduces the attack surface on users
- Reduce the risk of lateral movement in case of a security breach
This approach also leads to cost savings through optimized software licensing and improved compliance with regulations, particularly regarding access governance since the auditability of JIT access provides a clear record of who requested, approved, and received access, crucial for compliance reporting.
Veza Access Requests, part of the Veza Access Platform, facilitates the deployment of JIT access by providing a comprehensive product to manage and orchestrate access requests. Through its catalogue of requestable items, defined by Access Profiles, and governed by customizable policies, Veza allows organizations to implement granular control over access requests. Approval workflows ensure proper authorization while automated provisioning and revocation streamline the process. The platform’s logging capabilities provide a detailed audit trail, enhancing transparency and accountability. By simplifying the requester and approver experience, Veza makes JIT access more accessible and manageable for all stakeholders.
Looking ahead, JIT access will play a vital role in more organization’s modern security strategies, especially in their move towards implementing the principle of least privilege. As organizations face increasingly sophisticated cyber threats and stringent compliance requirements, reducing standing privileges becomes paramount. JIT access helps minimize the potential damage from compromised accounts and malicious insiders while also ensuring that legitimate users can efficiently obtain the access they need. As access management continues to evolve, with trends towards more dynamic and context-aware permissioning, JIT access will remain a cornerstone of robust security postures, enabling organizations to adapt to changing needs and mitigate emerging risks effectively.
Next Steps
Ready to take your access management to the next level? Download the ebook “Intelligent Access: Modernizing Identity with Just in Time Access”, authored by former Snowflake VP of Security Mario Duarte and Veza’s Co-Founder & CEO Tarun Thakur. In it, you’ll discover strategies for achieving least privilege in the modern enterprise and learn how JIT access can transform your approach to security. Get the ebook now.
And if you’re ready to see how Veza can help streamline your JIT access processes, we’d love to show you how our platform works in real time. Schedule a demo today and take the first step towards securing your organization’s access management.





