Introduction
Balancing security and productivity while ensuring employees have the appropriate access to resources is a critical challenge for modern enterprises. The growing complexity of systems, roles, and permissions has placed an unsustainable burden on IT and identity teams, who often lack the tools and context needed to assign the right role with the least privilege required to meet business objectives. These challenges inspired us to create Veza Access Requests – a solution designed to automate and streamline the access request process. By integrating powerful automation with data-driven insights about permissions, the purest form of access, Veza empowers organizations to grant access faster, ensure least privilege, and maintain security without compromising agility.
The Broken System of Manual Access Provisioning
For years, IT teams have been overwhelmed by the inefficiencies of manual access provisioning. The process is fraught with challenges – many stemming from the sheer volume and complexity of roles, each customizable within its respective system. IT teams spend countless hours researching role capabilities, attempting to match requests to the appropriate permissions. This often results in two undesirable outcomes: roles that are over-permissioned, introducing unnecessary risk, or significant delays that frustrate end users.
The impact of these inefficiencies goes beyond IT teams. End users frequently experience delays in receiving the access they need, disrupting their productivity. Managers, meanwhile, struggle with limited visibility into their teams’ permissions, leaving them ill-equipped to proactively manage access. Together, these issues perpetuate a cycle of excessive permissions, rubber-stamped approvals, and growing security risks – highlighting the urgent need for a more effective solution.
Automated, Policy-Driven Access at Scale
Veza Access Requests transforms traditional access management by automating and streamlining the entire process through a policy-driven approach. Built on the Veza Access Platform, it provides real-time visibility into entitlements, enabling organizations to efficiently manage access at scale while maintaining strict control.
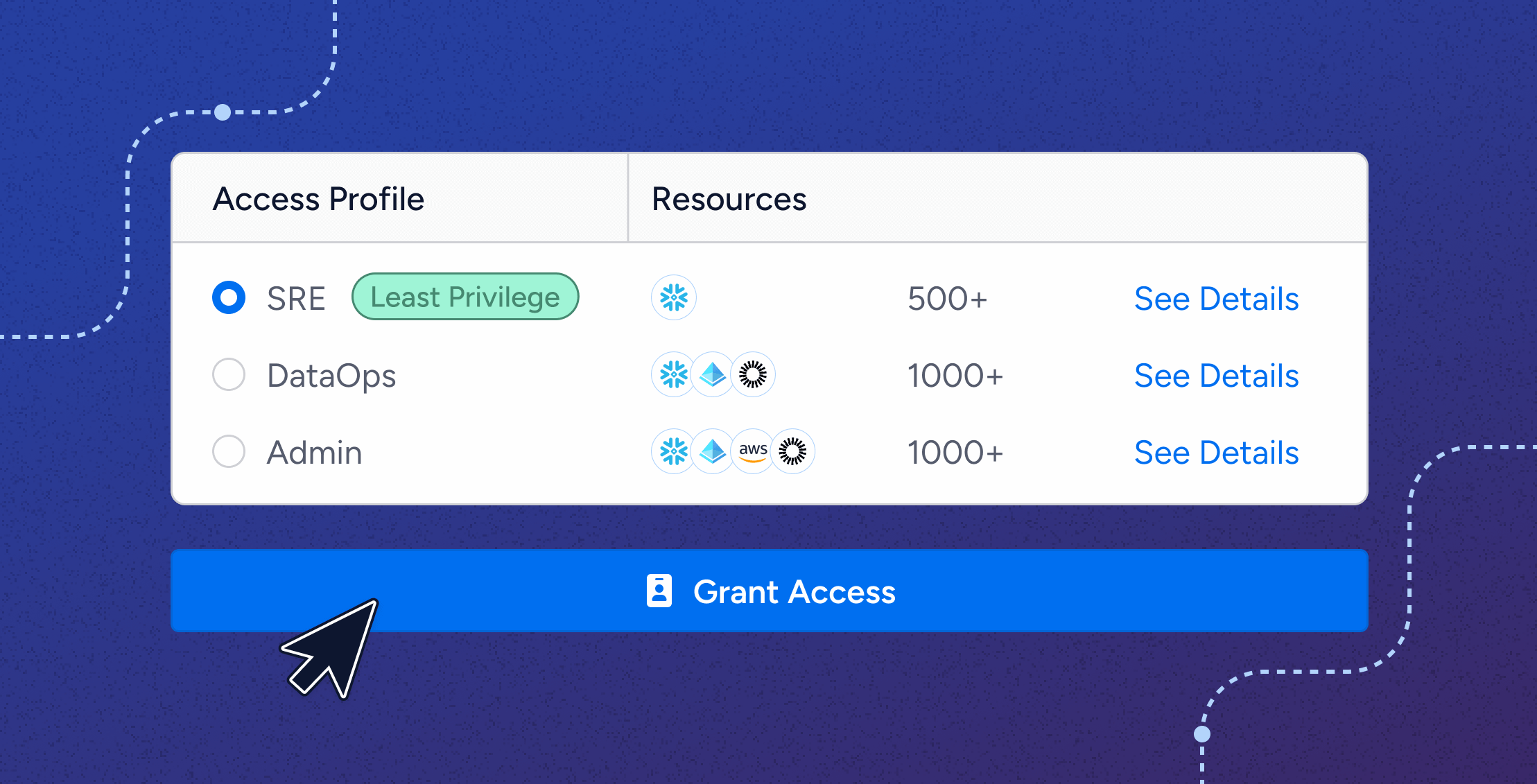
At its core, Veza Access Requests features a self-service catalog as part of the Access Hub – a new interface – that offers users a curated selection of roles, applications, and resources, ensuring they only request the access they truly need. The solution also incorporates just-in-time access, granting permissions only when necessary and automatically revoking them when they are no longer required, minimizing risks like privilege creep.
For the first time ever, the Access Hub allows end-users to now interface with Veza for their day-to-day needs including reviewing, requesting, and remediating access permissions. The Access Hub consolidates all of these features into a seamless interface, giving managers deep visibility and control over their teams’ access. With a comprehensive dashboard, managers can quickly review, approve, or remove access, ensuring that the right people have the right access at the right time.
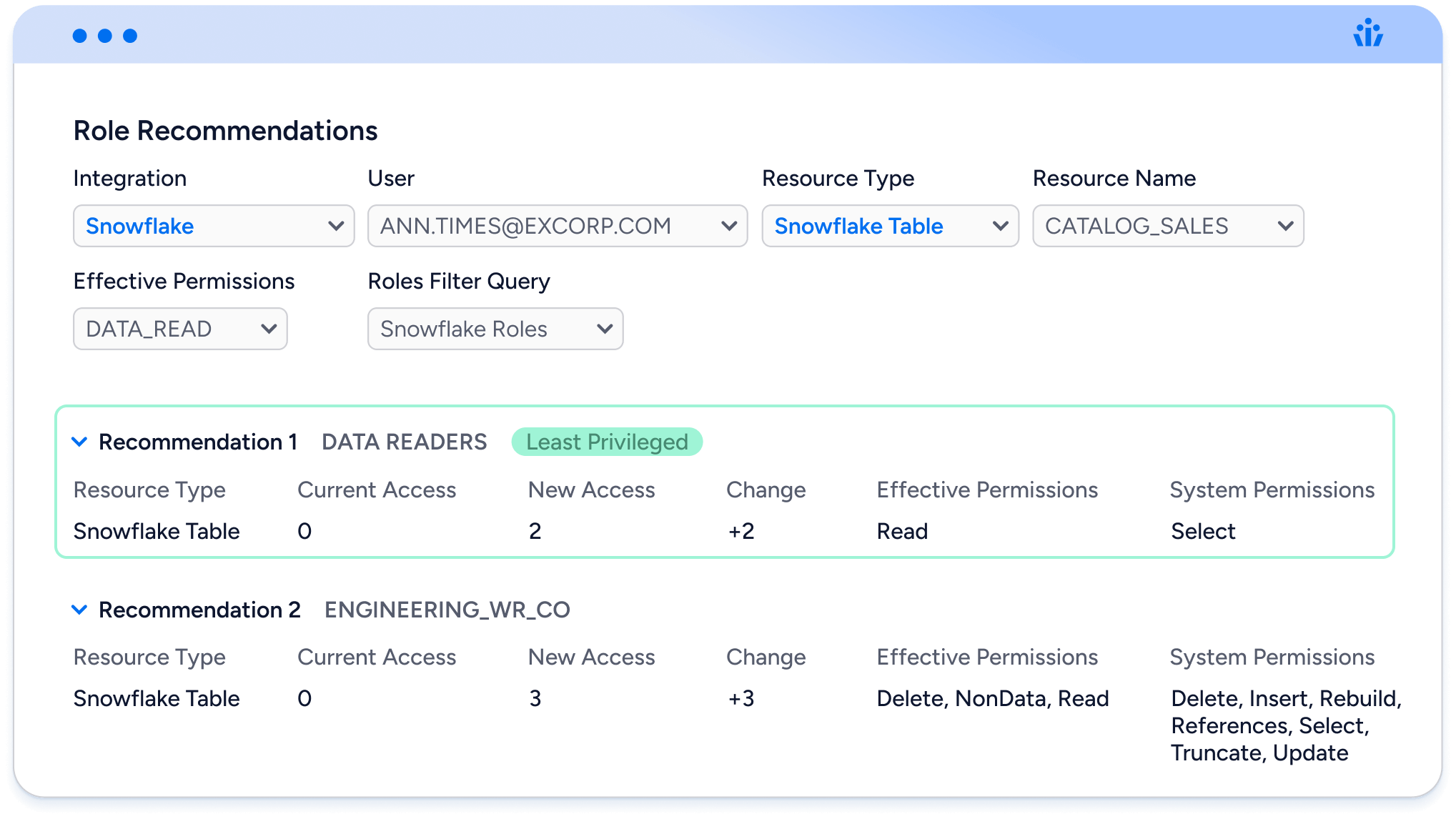
Role Recommendations: Precision Through AI
Access decisions are often hampered by a lack of clarity around which roles offer the appropriate permissions. This gap leaves IT teams either over-permissioning users to avoid delays or spending inordinate amounts of time researching roles. Veza’s Role Recommendations solve this problem by applying AI and machine learning to identify roles that best fit a user’s needs while adhering to the principle of least privilege.
The result is a curated catalog of application and role combinations that administrators can confidently approve. This catalog simplifies the self-service experience for users, ensuring they can request only what’s necessary for their work. By preventing excessive permissions at the request stage, Veza creates a streamlined process that saves time and bolsters security.
Just-in-Time Access: A Key to Least Privilege
In traditional access management, entitlements are often granted indefinitely, which leads to the accumulation of excessive permissions over time. This privilege creep not only increases the potential blast radius of compromised accounts but also exposes organizations to significant security vulnerabilities.
Veza Access Requests addresses this risk by ensuring that permissions are granted only when needed and automatically revoked when no longer required. This just-in-time approach minimizes the window of exposure, ensuring that users retain access only for the duration of their specific tasks. With automatic expiration, organizations can stay ahead of security threats while maintaining compliance – without burdening operations with manual access reviews.
Real-Time Governance for Managers
Managers often lack the visibility needed to govern their teams’ access effectively. The result is a reactive approach to access management, with delays in provisioning and limited oversight into existing entitlements. Veza’s Access Hub transforms this dynamic by providing managers with a centralized dashboard that delivers real-time insights into their team’s permissions.
Through the Access Hub, managers can view and manage access entitlements, initiate or approve access requests, and even remove outdated permissions. The intuitive interface allows for granular exploration of permissions, giving managers the tools they need to support their teams’ productivity while ensuring compliance with security policies. By empowering managers with this visibility, Veza bridges the gap between security and operational efficiency.

Faster, Smarter, and More Secure Access
Security shouldn’t come at the expense of business agility. With Veza Access Requests, organizations no longer have to choose between maintaining stringent security controls and enabling their teams to work efficiently. The platform allows users to request and receive the right access in minutes, not days, while just-in-time provisioning and automatic expiration minimize privilege creep over time. Finally, Veza’s Role Recommendations apply AI and machine learning to identify roles that best fit a user’s specific needs while adhering to the principle of least privilege.
By automating the most labor-intensive aspects of access management, Veza eases the workload on IT teams, reduces ticket volumes, and ensures compliance with internal policies. And with integrations for leading SaaS applications like Microsoft, Google, Okta, and Snowflake, as well as SCIM support, teams can implement Veza Access Requests quickly and seamlessly.
Ready to learn more? Discover how Veza Access Requests can transform your access management today.





