1. The Critical Need for Modern Access Visibility
The Challenge: Over-provisioning is a Security Blind Spot
Security teams today struggle with over-provisioned access, where users and service accounts have more permissions than they use or need. This isn’t just an operational nuisance; it’s a major security risk. Attackers exploit unused but enabled permissions to escalate privileges, move laterally across environments, and exfiltrate sensitive data.
Yet, traditional identity and access management (IAM) tools fail to provide insight into over-permissioned accounts. Here’s why:
- Periodic access reviews are static and outdated – Organizations generally conduct access reviews on a scheduled basis to meet audit requirements, but these reviews are highly manual, generally rubber-stamped and rely on snapshots that quickly become obsolete. They fail to detect near real-time risks posed by excessive or unused permissions.
- No easy way to quantify over-provisioning – Without a clear way to measure unused permissions, security teams struggle to prioritize remediation efforts and reduce risk effectively.
- Manual tracking is inefficient and leaves critical blind spots. Many security teams still rely on cumbersome Excel sheets to track access permissions, making it nearly impossible to maintain accuracy at scale. Sifting through logs and static reports by hand is overwhelming, leading to inconsistencies, overlooked excessive permissions, and security lapses.
Why This Matters
Access in the new world is both highly dynamic and the most common root cause of security incidents. To maintain a good security posture and avoid leaving open accidental doors for attackers, organizations need continuous, granular Activity Monitoring to proactively mitigate access threats as they occur. This requires a more real-time capability to identify & quantify over-provisioned and unused access as a matter of daily security operations and automation, and not merely quarterly reactions to compliance checklists. Enter Veza’s Activity Monitoring + OPAS, a modern approach that finally quantifies over-provisioned access and helps security teams take actionable, data-driven steps to reduce risk.
The Solution: OPAS—Over Provisioned Access Score
OPAS isn’t just another audit tool—it’s a security control that helps teams:
- Quantify over-provisioning across their entire identity landscape.
- Identify dormant accounts and permissions that increase the attack surface.
- Prioritize high-risk users and roles based on real-time access insights.
- Enforce the least privilege dynamically without disrupting legitimate workflows.
OPAS provides security teams with clear, actionable insights into who has access, how it’s being used, and where unnecessary permissions create risk. By filtering identities with high OPAS scores, teams can quickly audit over-provisioned users and remove unused access, strengthening least privilege without disrupting productivity.
With OPAS, security teams can proactively reduce risk, streamline compliance, and make access reviews more effective—ensuring that permissions align with actual usage, not outdated assumptions.
2. What is OPAS, and How Does It Work?
The Concept: Scoring Over-provisioned Access
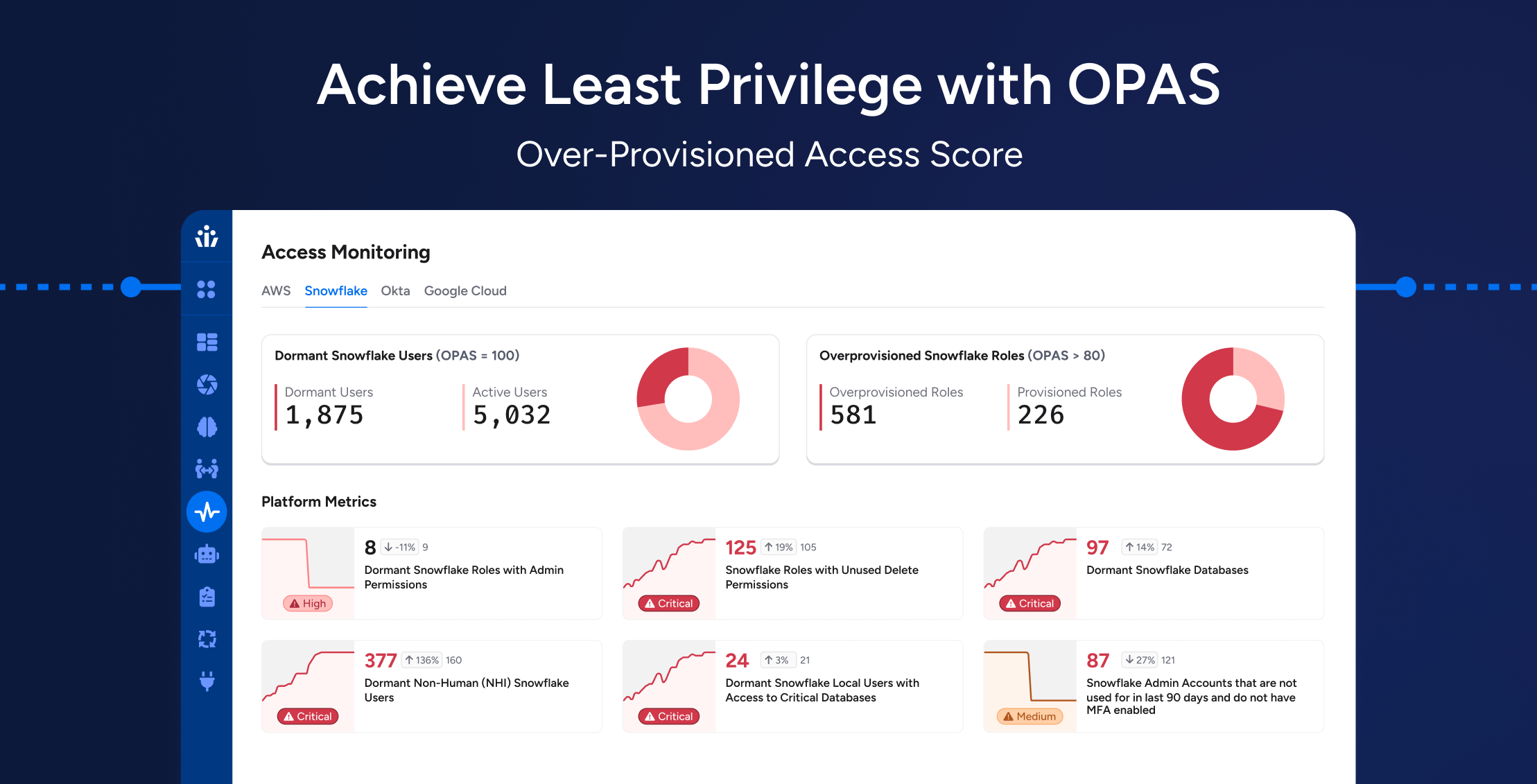
OPAS (Over Provisioned Access Score) represents the percentage of access to resources granted to an identity that has not been used recently.
Example:
- A user has read access to 10 Snowflake tables but only reads from 3 of them.
- This means 70% of their resources are unused and may no longer be required, which increases risk.
- The OPAS score reflects this over-provisioning—helping teams pinpoint which accounts need remediation first.
How OPAS Helps Security Teams Take Action
- Identifying Dormant Entities: Any entity with 100% OPAS is completely dormant, making it a prime candidate for access removal.
- Prioritizing Over-Provisioned Accounts: A role with 95% OPAS should be reviewed before one with 75% OPAS—enabling risk-based access decisions.
- Drilling Down to the Permission Level: Security teams can view OPAS for specific permissions—e.g., identifying unused “Delete” permissions, which pose a high risk if compromised.
3. OPAS in Action: Real-Time Activity Monitoring & Risk Reduction
How OPAS is Calculated
Veza’s Access Graph models who has access to which resources, including roles, groups, and granular permissions. It integrates this access data with real-time activity data pulled from audit logs across platforms like AWS, Snowflake, and other cloud environments. The system overlays the access data from the Access Graph with the activity data to generate OPAS scores for each identity and resource type pair.
For example, consider a user, U1, who has access to 10 S3 buckets. Out of these, 3 have been actively used in the past 30 days. The OPAS score for this user with S3 buckets is 70%, reflecting that 7 out of 10 buckets are unused hence, the user is over-provisioned on 70% of the S3 buckets
Key Metrics Behind OPAS Calculation:
- Tracking Resource Activity – Veza monitors when a user or service last accessed a resource or performed any action.
- Identifying Dormant Access – If an entity (user, role, or service account) hasn’t accessed a resource within a defined period (e.g., 30, 60, or 90 days), it is flagged as dormant, indicating no usage or risk.
- Granular Permission-Level Analysis – OPAS allows security teams to filter unused permissions at a granular level, such as Delete, Write, or Admin rights, to help identify and remove excessive permissions.
Example: Snowflake User Santosh
- Santosh has Read + Delete access on Database customers and orders.
- Santosh used Read & Delete on customers (7 days ago) but only Read on orders (14 days ago).
- Santosh’s OPAS Score (30-day period):
- Santosh’s OPAS for all permissions: 0% (The user has used some permission on all the resources).
- Santosh’s OPAS for Delete permissions: 50% (Out of the all the delete permissions on resources that Santosh has, he has used only 50% ).
Deep Integration with Veza’s Activity Monitoring
By combining OPAS with Veza’s real-time access monitoring, security teams gain an actionable view of privilege usage:
- Near Real-time insights into which privileged roles and users are actually using their access.
- Automated reports for audits & compliance, ensuring teams can take action before an access review.
- Enriched Access Reviews – OPAS scores highlight unused permissions, guiding reviewers to revoke excessive access instead of simply rubber-stamping approvals.
Without OPAS: security teams must manually sift through logs, often missing over-provisioned users and roles.
With OPAS: they can instantly filter high-risk entities, audit them efficiently, and remove excessive permissions—reducing risk in minutes, not months.
{insert video here}
4. The OPAS Advantage: Real Security & Business Impact
Reducing the Attack Surface
Every unused permission represents a potential attack vector. Dormant accounts, standing privileges, and excessive access make it easier for attackers to exploit credentials, escalate privileges, and move laterally across environments.
OPAS provides quantifiable insights into over-provisioning, helping organizations:
- Eliminate standing privileges for inactive users and service accounts.
- Reduce excessive access across cloud, SaaS, and on-prem platforms.
- Shrink the attack surface without disrupting legitimate workflows.
When unused permissions are removed proactively, attackers have fewer opportunities to exploit misconfigurations and privilege creep.
Enforcing Least Privilege with Precision
Traditional least-privilege strategies often lack the precision needed to be effective. Security teams struggle to answer key questions:
- Who is over-provisioned?
- When did their access exceed what’s necessary?
- How are they over-privileged? What specific resources or permissions pose a risk?
- What needs to be adjusted to enforce the least privilege without disrupting productivity?
Without clear, near real-time insights, teams either revoke access too aggressively, breaking workflows, or leave excessive permissions unchecked, increasing security risk. OPAS changes this by providing real-time visibility and actionable insights, ensuring that the least privilege is achieved with precision, not guesswork.
With OPAS, teams can:
- Drive the least privilege with actionable insights – pinpointing unused permissions for removal.
- Target privilege reductions at the permission level – eliminating unnecessary “Delete” or “Admin” rights while keeping essential access intact.
- Monitor privilege usage continuously – ensuring only active, necessary permissions remain over time.
Instead of making arbitrary access decisions, OPAS helps teams optimize permissions with precision, keeping users productive while improving security.
Streamlining Compliance & Audit Readiness
Security audits and compliance reviews are often time-consuming and inefficient, requiring manual access certifications that lead to rubber-stamping permissions instead of meaningful security actions.
With OPAS, compliance teams can:
- Automatically generate reports that highlight over-provisioned users and roles.
- Streamline access reviews by displaying OPAS scores alongside entitlements.
- Ensure access decisions are backed by real data—so permissions are revoked based on usage, not assumptions.
This approach makes security teams more effective while keeping compliance efforts focused on real risks—instead of just meeting regulatory checkboxes.
5. Real-World Use Cases: OPAS + Veza’s Activity Monitoring
Security & Compliance Teams: Proactive Privileged Access Management
Traditionally, security teams have relied on manual audits to track privileged access, often missing hidden over-provisioning. OPAS changes this by enabling:
- Automated identification of high-risk, over-privileged accounts.
- Streamlined access reviews with real-time insights into privilege usage.
- Reduction of dormant and excessive permissions before they become attack vectors.
DevOps & Cloud Teams: Preventing Privilege Creep in Multi-Cloud Environments
- In cloud environments, developers and DevOps teams are often granted broad access to streamline operations, but these permissions rarely get cleaned up once they’re no longer needed. OPAS helps by:
- Identifying inactive permissions without disrupting workflows.
- Preventing privilege creep in fast-moving DevOps pipelines.
IT & Infrastructure Teams: Reducing Administrative Overhead
Managing privileged access across multiple platforms is time-intensive, and manual audits are unsustainable at scale. OPAS provides IT teams with:
- Automated privilege reduction recommendations based on real usage data.
- Simplified approval workflows with pre-filtered OPAS insights.
- Continuous monitoring of access trends, ensuring security policies are enforced dynamically.
6. Final Thoughts
Access security has long been a guessing game—but OPAS changes that. By quantifying privilege risks and enabling proactive access reductions, organizations can finally take control of their attack surface. This approach empowers enterprises to implement the principle of least privilege, significantly reducing risk without disrupting business operations.
OPAS isn’t just a tool—it’s a new way of thinking about access security. Are you ready to rethink yours?
New to access security? Explore how Veza addresses modern identity security challenges to understand why visibility into permissions and usage is the foundation of Zero Trust and least privilege.
Want to learn how Veza delivers real-time access insights? Discover Veza’s Access Monitoring capabilities and see how combining access data with activity data can transform your access reviews.
Ready to take the next step? Schedule a personalized demo to see how Veza and OPAS help organizations enforce least privilege with precision and confidence.
Coming in Part 2:
🔹 How Veza’s Activity Monitoring detects and eliminates dormant access.
🔹 Why inactive accounts are a major security liability.






