Welcome to the June 2024 Veza Product Update! We’re excited to share the latest enhancements and new features from the latest weekly releases. Our team has been diligently working to improve your experience on the platform, especially around understanding and monitoring risks associated with non-human identities. This includes expanded support for machine access credentials such as tokens and API keys.
This update includes enhancements in risk management, query builder functionality, and access review usability. As always, we have enhanced and added integrations to expand your ability to secure and manage a range of possible environments, including Oracle Database on AWS RDS.
Read the highlights and major changes to empower your identity security and access management practices with Veza:
Access Intelligence
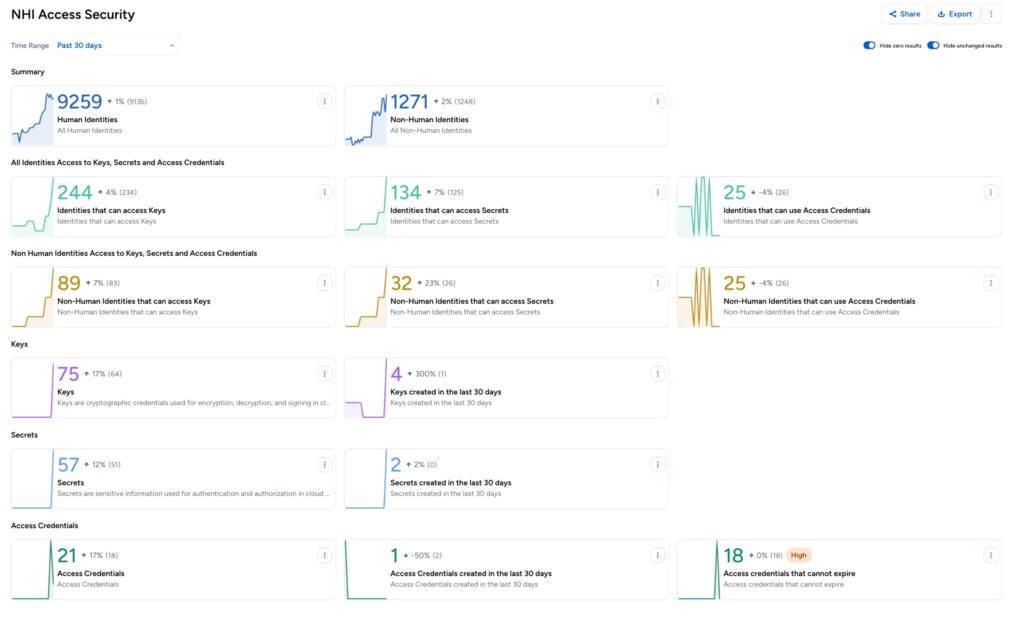
- Non-Human Identity Dashboards: Added two new dashboards for monitoring and understanding the access of non-human identities in various environments, and how they interact with critical resources using keys, secrets, and access credentials.
- NHI Access Security: Highlights non-human identities accessing secrets and using access credentials, helping identify trends and potential security gaps.
- NHI Insights: Visibility into identity sprawl and capabilities, such as AWS EC2 instances that can list and read bucket objects, or Microsoft Azure AD Service Principals connected to VMs.NHI Access Security Dashboard
- Risk Details: You can now quickly view the detailed explanations and get remediation instructions by opening a details sidebar on the Queries with Risks page.
- Non-Human Identities: Added support for automatically labeling human and non-human identities with Enrichment Rules, configured in the Integrations section. Administrators can use these rules to label entities as “NHI” or “Human” automatically.
- Dashboard Export: Dashboards now include an Export button to save the current view as a PDF.
Access Visibility
- Entity Type Groupings for Non-Human Identities: You can now use “Access Creds,” “Keys,” or “Secrets” as the source or destination to search across all included entity types
- Credential Expiration Distinction: Veza now adds the Can Expire attribute to GitHub Personal Access Tokens and AWS Access Keys to distinguish access credentials supporting expiry dates from those that do not.
- Query Builder: When using an entity type grouping (such as “Identity” or “Access Creds”) as the query source or destination, you can now use the Filter by Type menu to select specific entity types in the grouping.
- Query Builder: When using the Show Destinations option to get results as source-destination pairs, you can now filter and visualize all destination entity attributes using additional columns.
- Query Builder Enabling Show Destinations now includes Last Activity At and Last Activity With Resource At columns, when the source and destination entity types support Activity Monitoring.
- Query Details: Opening a query to view details or clicking on a dashboard tile now opens a redesigned details page featuring a spreadsheet-like view of the results.
- Query Export: Query exports now include any tags applied to destination entities.
Access Reviews
- PDF Exports: PDF exports for individual reviews now include additional pages with review metadata, reviewer details, data source details, and row completion statistics. The title page now features the review publication date, completion date, and the user who completed the review.
- Approve and Sign-off: It is now possible to control whether the Approve and Sign-off action is shown in the reviewer interface. When enabled, reviewers can approve and sign off on applicable rows with one click, using an in-row action or bulk action on selected rows.
- Column Customization: Default columns in the reviewer interface can now be defined for individual configurations, enabling customized reviewer experiences for all reviews using the specified configuration.
Lifecycle Management
- GitHub: Added preliminary support for GitHub as a provisioning target.
- Policies: Attribute transformations can now use nested
IF/THEN/ELSEstatements. - Custom Attributes: Policies can now define custom attributes for provisioning targets such as Okta and Microsoft Azure AD users.
- Manual Workflows: Added support for manually running workflows for identities with no matches.
- Provisioning Sources: Added support for selecting more than one human resources information system (HRIS) integration as a possible source when syncing identities.
Integrations
New Integrations
- SwiftConnect: New integration for discovering profiles, badges, and access on the SwiftConnect platform (Early Access).
- Oracle Database (AWS RDS): New integration for discovering resources and access controls for Oracle Database on AWS RDS.
Enhancements
- AWS Access Keys: Added support for discovering AWS Access Keys and their attributes, such as Name, Active, Created At, Last Used At, Last Used Service, and Last Used Region.
- Microsoft Azure: Added support for extracting custom On Premises Extension Attributes for Azure AD Users. To specify extension attributes in an integration configuration, use the full name, e.g., ExtensionAttribute12.
- CSV Import: Added several requested enhancements for importing users, groups, and roles from CSV:
- Importing a custom application from CSV now supports the full range of custom user attributes, including Password Last Changed At and Last Login At.
- Roles and Groups can now be assigned by creating additional rows for a user.
- Improved encoding support to support CSV files generated with a wider range of applications.
- GitHub: Veza now discovers GitHub Personal Access Tokens and their effective repository permissions, used for programmatic access to GitHub resources.
- Google Cloud: Veza now shows Service Account Keys for a parent Service Account, and their effective permissions on resources assigned to that Service Account.
- HashiCorp Vault: Added support for gathering nested secrets for secret engines such as KV2. Nested secrets are shown as sub-resources of the parent secret in Graph search.
- Okta: Veza now gathers additional attributes for Okta Users: Password Changed, User Type ID, User Type, Recovery Question Exists, Credentials Provider Type, and Credentials Provider Name.
- SharePoint: When applying System Permissions filters in Graph search or Query Builder,
Read/Write/Ownerpermissions on SharePoint Folders now have aninheritedordirectprefix. The prefix indicates whether permission is inherited from the Folder’s parent, or assigned directly to the Folder. - Snowflake: Veza now extracts and parses Snowflake Database Roles.
- Workday: Added the ability to get custom reports and add fields as custom properties for Workday Workers.
Open Authorization API
- Access Credentials for Custom Applications: The custom application template now supports an array of
AccessCredsfor modeling API keys and other credentials assigned to users to grant roles and permissions on resources.
Platform API
- Added a v1 API operation
GET "/api/v1/users/self", returning details about the calling user without requiring an ID. - Improved logging on the Events page when an Insight Point is unavailable.
Product Design and Usability
- Access Intelligence
- The Access Analytics overview is now the default Access Intelligence landing page, shown when logging in to Veza.
- Dashboards now include shortcut icons to filter queries by integration. Tiles now show include the risk level, if the featured query has one.
- Dashboard trend charts can now show the total Y-axis in addition to changes over time.
- Access Visibility
- Users can now cancel long-running exports directly from the Query Builder.
- Access Reviews
- The row actions dropdown now includes the option to Add a Note for a single row.
- In the reviewer interface, the icon to open the full row details in a sidebar now appears only on hover.
- Improved consistency of titles and button labels throughout the product.
- Lifecycle Management
- New interfaces for Policy and Access Profile management, Identity centric-view, and Event view.
- Integrations:
- Improved UI for easily filtering the list of integrations by provider name, type, or status.
- Data source errors are now indicated by a warning status on the integration overview. You can now filter the Integrations page to show events for recently created integrations.