
Hi there,
Welcome to the Veza Voice, our monthly customer email where we share product updates, tips and tricks, events and news.
This month: we introduce powerful new risk dashboards, new risk tiles, new trends, expanded capabilities for GCP IAM, new Veza integrations, and more!
-Mike B.
Product Update: Introducing Risks
Identity makes up a huge portion of your organization’s attack surface. To secure access to SaaS apps and data you need to be able to identify, track, and remediate access risks. Examples of risk factors include:
- Identity Access Risks
- Privileged Access Risks
- Cloud IAM Access Risks
- SaaS Posture Risks
But without visibility into the effective permissions of users across all your cloud providers, apps, and data systems, these risks can be difficult to quantify. You know that having too many users with admin privileges makes you vulnerable to data breaches, ransomware, and other disasters, but how many users actually have those privileges? Without being able to quantify the problem, you don’t know how urgent it is. And without being able to track it over time, you can’t demonstrate to your stakeholders that your security and governance efforts are actually paying off.
We’re introducing the concept of “Risks” into the Veza platform to help you continually monitor your key risk factors, set rules and policies to drive action, and shrink your attack surface over time.
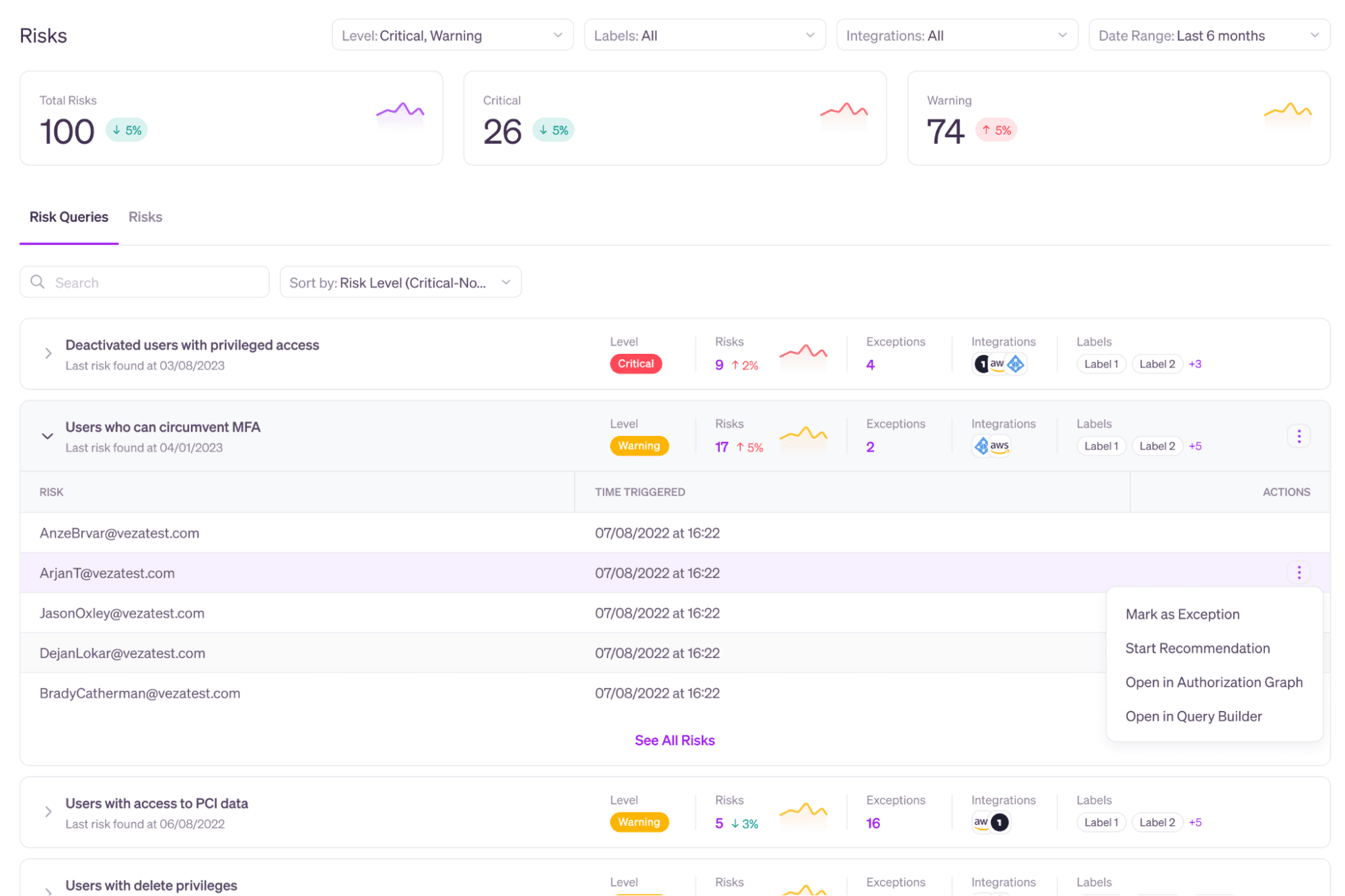
How it works
Veza reads, parses, organizes and stores authorization metadata across enterprise systems: identity providers, SaaS apps, data systems, cloud services, etc. Veza offers a suite of products—search, workflows, insights, monitoring—that allows organizations to query this data that is relevant to business needs, such as privileged violations, and identity access risks. Any query in Veza can be marked as a risk. To help you triage, you can categorize the most important risks for your organization as “Critical”, and other risks as “Warning”.
Veza counts each result returned by queries marked “Critical” or “Warning” as a risk. For example, if your query “Deactivated users with privileged access” returns 9 identities, your total risks increase by 9. You can see your total risks, and a breakdown of Critical vs Warning risks at the top of the Risk page.
You can also mark exceptions for each risk query. For example you might create a query for “Users with write access to production repositories” in GitHub and categorize the risk level as Critical. However, you’re likely to have at least one identity—like a service account for your CI/CD platform—that is actually intended to have this access. By marking that identity as an exception, you can prevent it from being counted as a risk.
Key Benefits
Track the health of identities at a glance
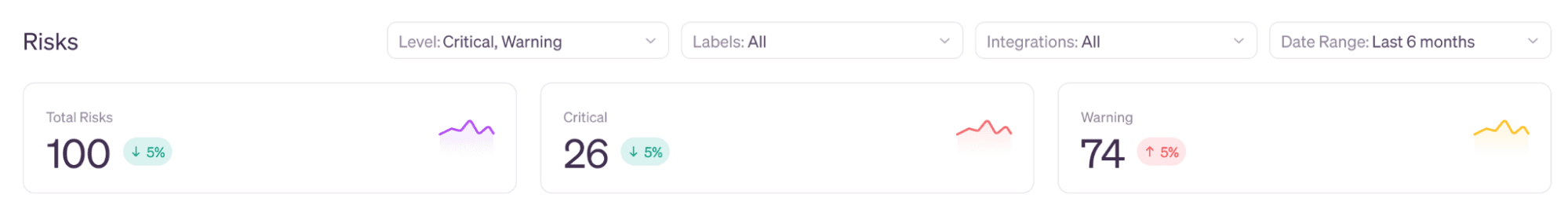
The top row of the Risks page are key analytics for access risks across your organization. The Veza dashboard is designed to quickly present your risk profile across key categories (identity access, privileged access, SaaS misconfigurations, cloud IAM, and more): how many risks are currently outstanding, how many are critical, and what direction are your overall metrics moving in?
Introducing Trends
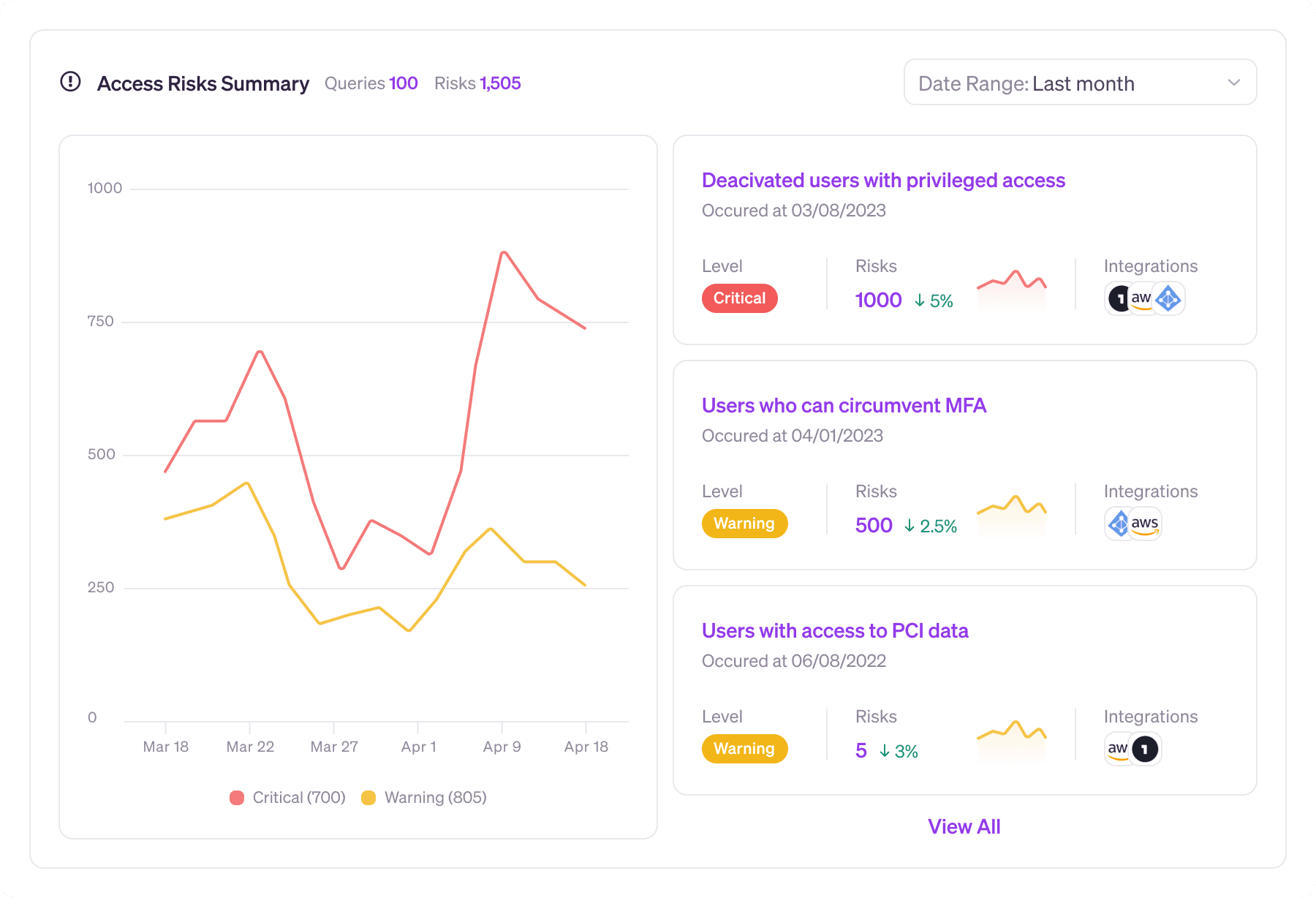
You can track progress on your total risks, or any individual query, by graphing the results over a given date range. Showing a continued downward trend for a group of agreed on risks helps you demonstrate return on your investment in identity-first security. Keeping an eye on your risk trends also helps you evaluate the effectiveness of your governance activities. For example, did your overall risk profile decrease after your most recent round of access reviews?
Veza Integrations
As we continue to expand the reach of Veza’s Authorization Graph, our team is always easing new integrations. Newest integrations include:
- AWS Cognito
- AWS Lambda
- Github Organizations
- Github Enterprise
Reach out to your customer service manager to get started.
Veza releases new features every week. Bookmark our release notes page to see the latest and greatest.
Tips and tricks: Find and eliminate misconfigurations in Google Groups
If you’re using Google Cloud in your organization, then you’re using Google Workspace as an identity layer. Even if you use an external IdP, like Okta or Azure AD, to provision your users access to Google Cloud, you still need to be mindful of additional identity hygiene risks that can arise within Google Workspace.
For this installment of Tips & Tricks, we’ll show you how to monitor for toxic combinations in Google Groups that can allow external threat actors to gain access to your projects. There are a few things you need to know about Google Groups
- Google groups have multiple classes of membership: Owners, Managers, and Members
- Google groups can be configured to allow Owners, Managers, or any Members to manage membership of the group
- Google groups can be configured to allow users from outside the organization to join. Groups even can be configured to allow anyone on the web to join, with or without asking.
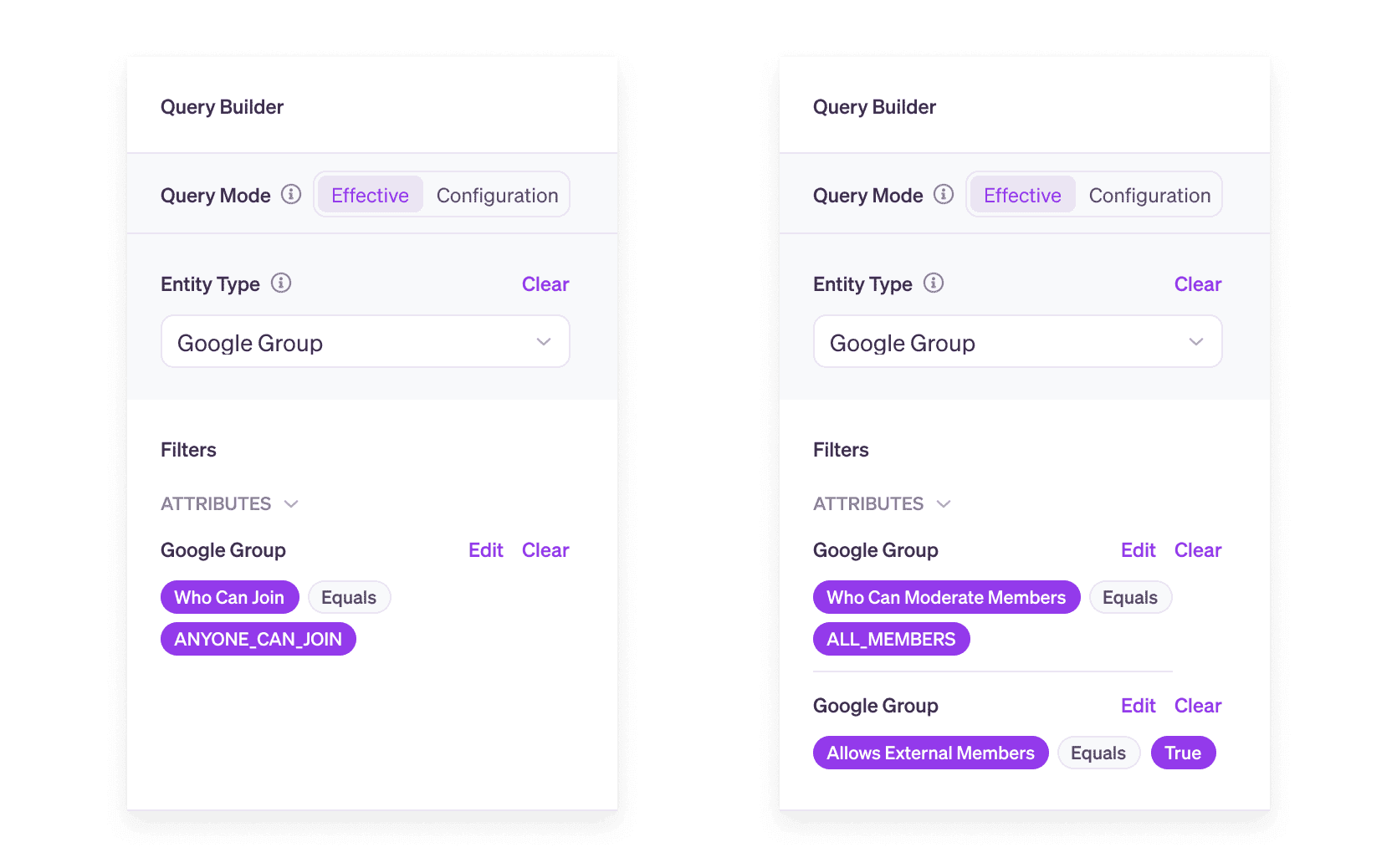
You can see how misconfigured Groups can potentially expose sensitive data in your Google Cloud projects to anyone on the web. Fortunately, you can monitor for risky group configurations in Veza using the following Google Group attributes:
- Allow External Members
- Who Can Moderate Members
- Who Can Join
For example, you can set up alerts in Veza for any Google Groups configured so that anyone on the internet can join, or any groups that allow external members, and also allow any member to moderate members.
Visit the docs to learn more about creating rules and alerts to monitor risks and misconfigurations.
Events
Meet the Veza team at these upcoming events:
- RSA, April 24-27 in San Francisco. We will be hosting a dinner on April 25th at 8pm at the Monarch – Sign up here! Interested in a meeting with Veza Execs onsite? Sign up here for follow up or contact your AE!
- Identiverse, May 30-June 2 in Las Vegas
- AWS re:Inforce, June 13-14 in Anaheim
- Snowflake Summit, June 26-29 in Las Vegas
Email events@veza.com for more details.
News
- Read Veza’s Co-Founder & CEO Tarun Thakur in Dark Reading: Everybody wants least privilege. So why isn’t anyone achieving it?
- We welcomed Jason Garoutte to the Veza team as our CMO.
- Veza was named one of 15 new cybersecurity products to know in Q1 of 2023 by CRN.com.






