Access Reviews
Automate user access certifications – creating comprehensive campaigns in record time. Certify with confidence by prioritizing risky access first and giving reviewers the context they need to approve or reject.
Why use Veza
Key Benefits
- Rapid Deployment: Get started in minutes with hundreds of agentless integrations. Compile campaigns instantly.
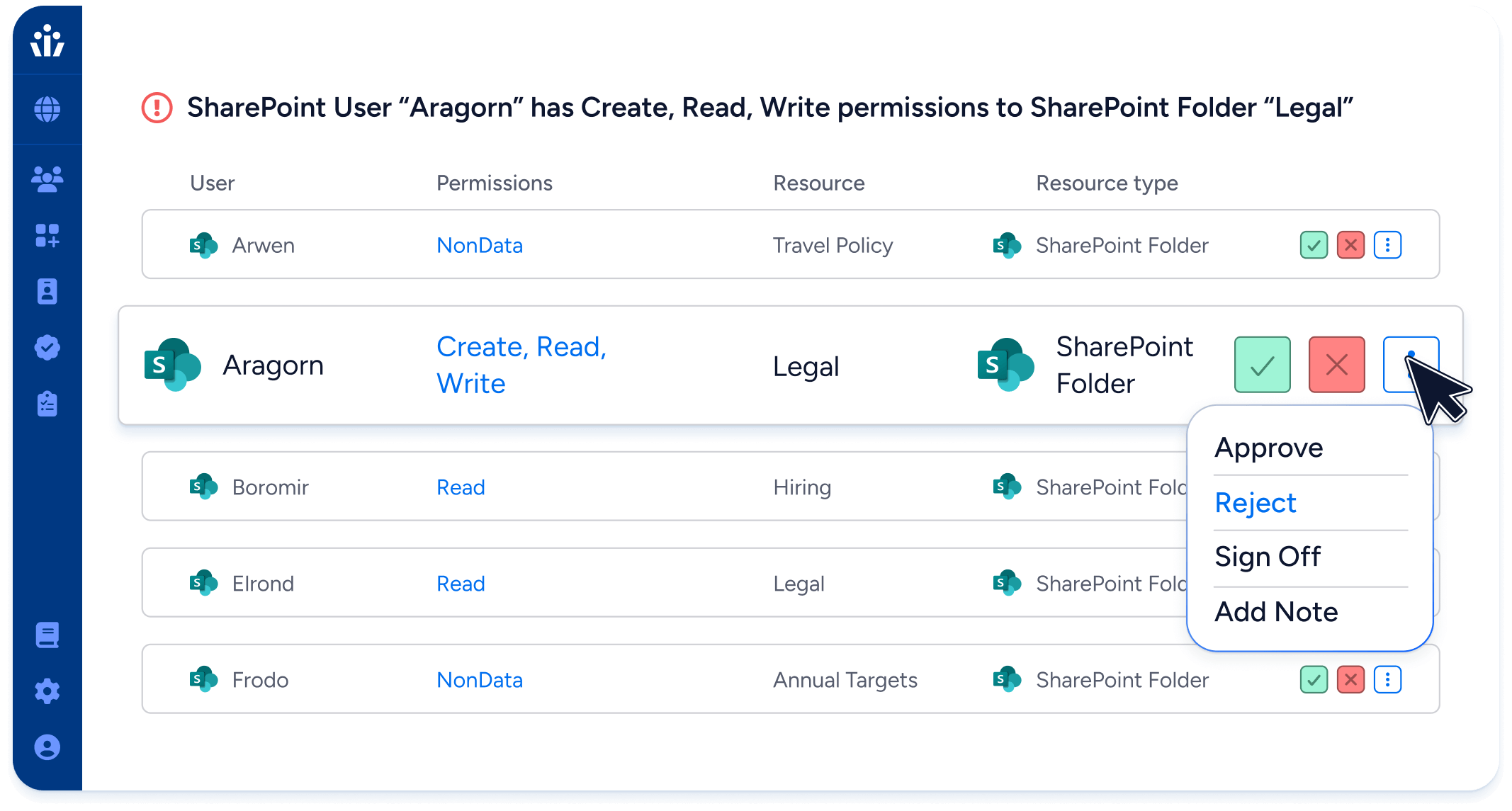
- Trusted Certifications: Stop guessing about abstract role names. Veza’s effective permissions translates system permissions into simple terms: Create, Read, Update, Delete.
- Efficiency: Focus on reviewing access with the greatest risk by prioritizing privileged accounts, toxic combinations and separation of duties violations.
- Comprehensive Reviews: Accurately reveal all accounts with access, including local, machine, and service accounts, even if they exist outside your identity platforms.
Key Features
- Access Reviews: Create campaigns to review the permissions of any human or machine user, or for any resource, such as an S3 bucket or Snowflake table.
- Review Delegation: Automatically assign reviewers to the user’s manager or the owner of the resource.
- Smart Actions: Bulk certify access based on customizable conditions such as last-modified, time limits, recent usage, and separation-of-duties (SOD).
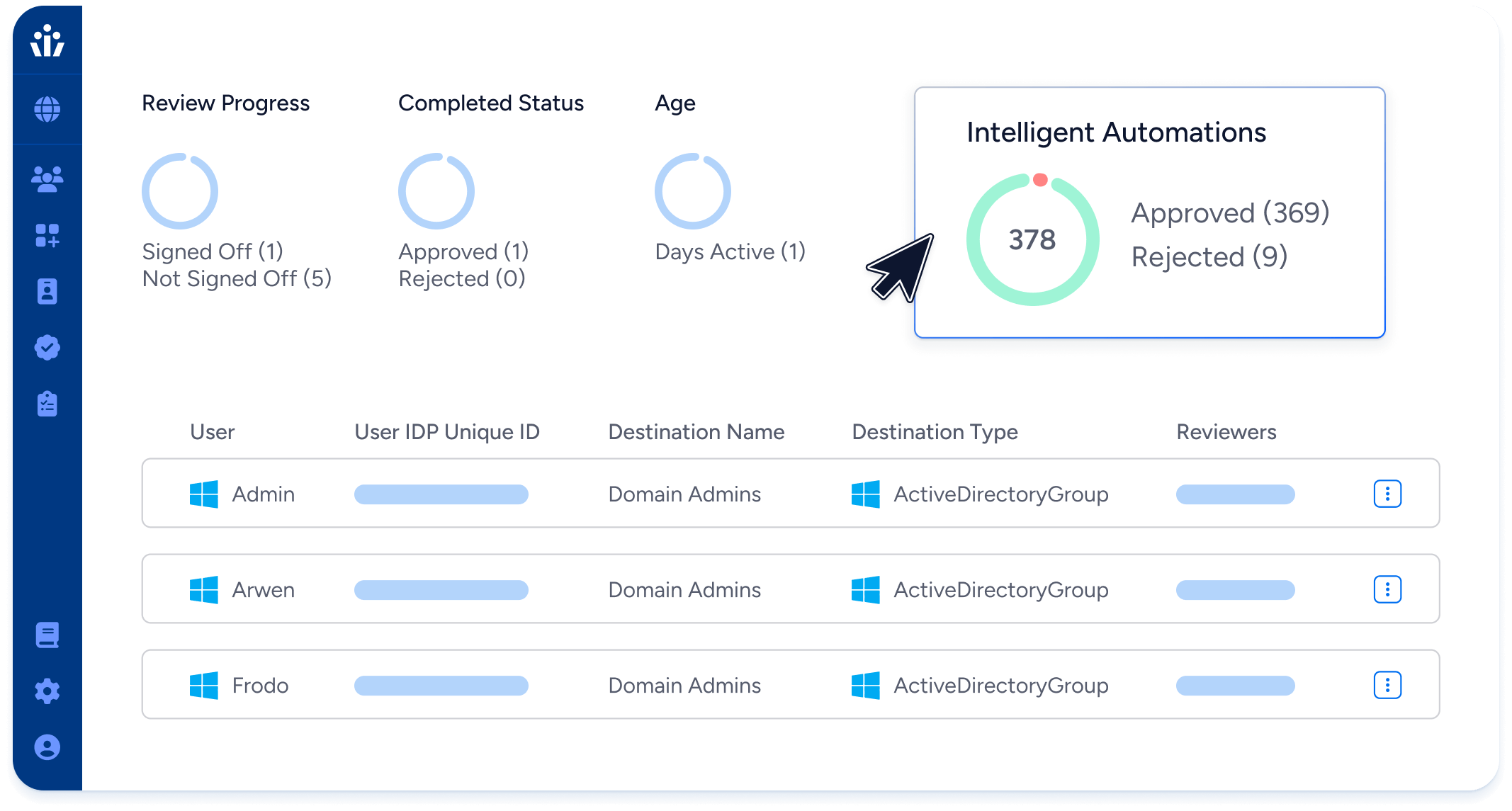
- Review Intelligence: Automate review suggestions based on past decisions.
- Enterprise Scale: Conduct hundreds of access reviews for all of your systems at once for large compliance programs.
- API Access: Programmatically create access reviews, view, or update certifications, and integrate with existing review tools.
Introducing Advanced Access Reviews
ADVANCED FEATURES
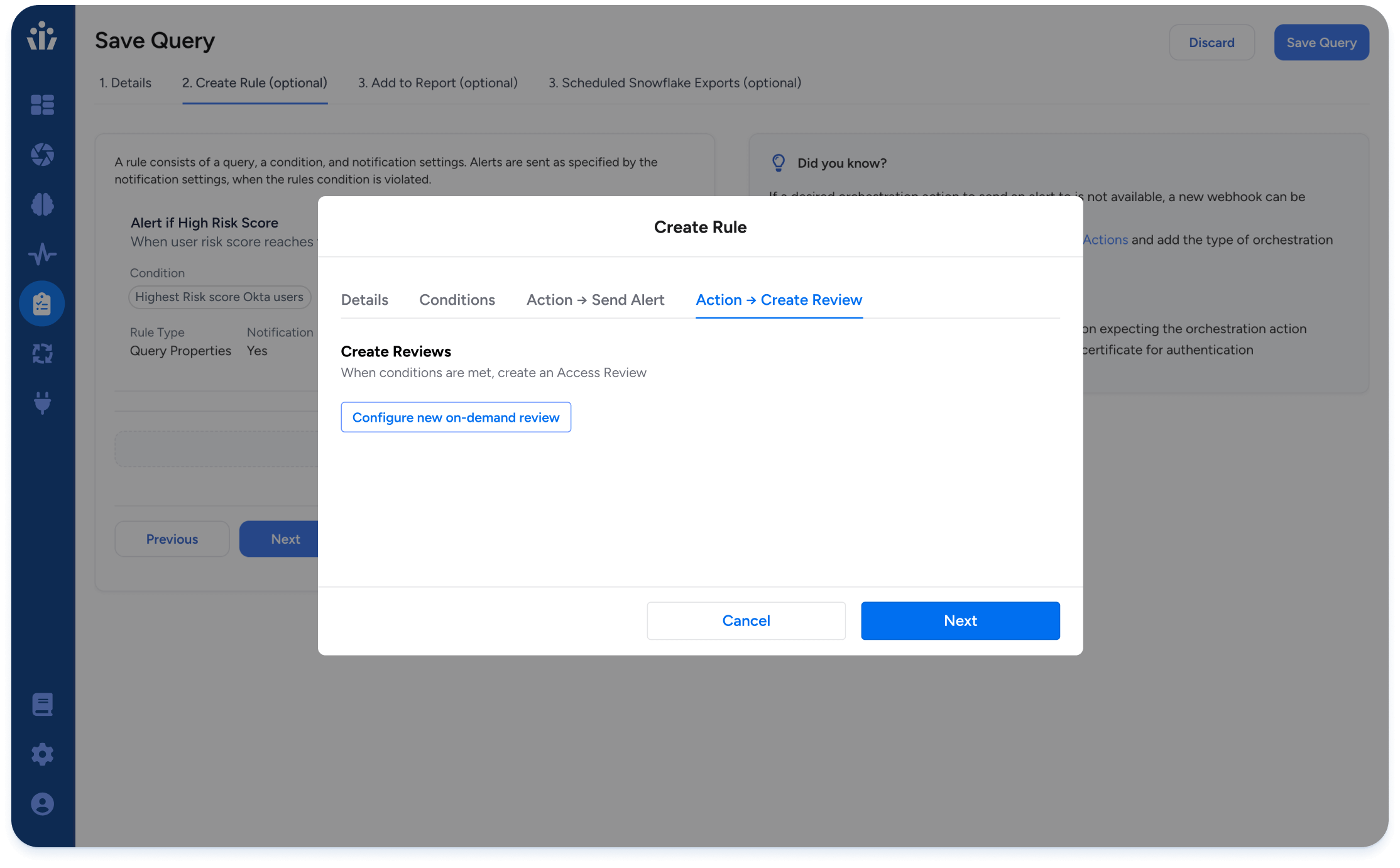
- Advanced Review Intelligence automation: Automate reviewer actions, such as approve, reject, or sign-off, for entities matching pre-defined and custom policies
- Access Intelligence integration: Focus reviewers on the riskiest users, entitlements, and resources by incorporating risk scores and risk levels into your reviews
- Role Analytics: Give reviewers a clear understanding of access granted per role, including resource counts, access levels, and risk
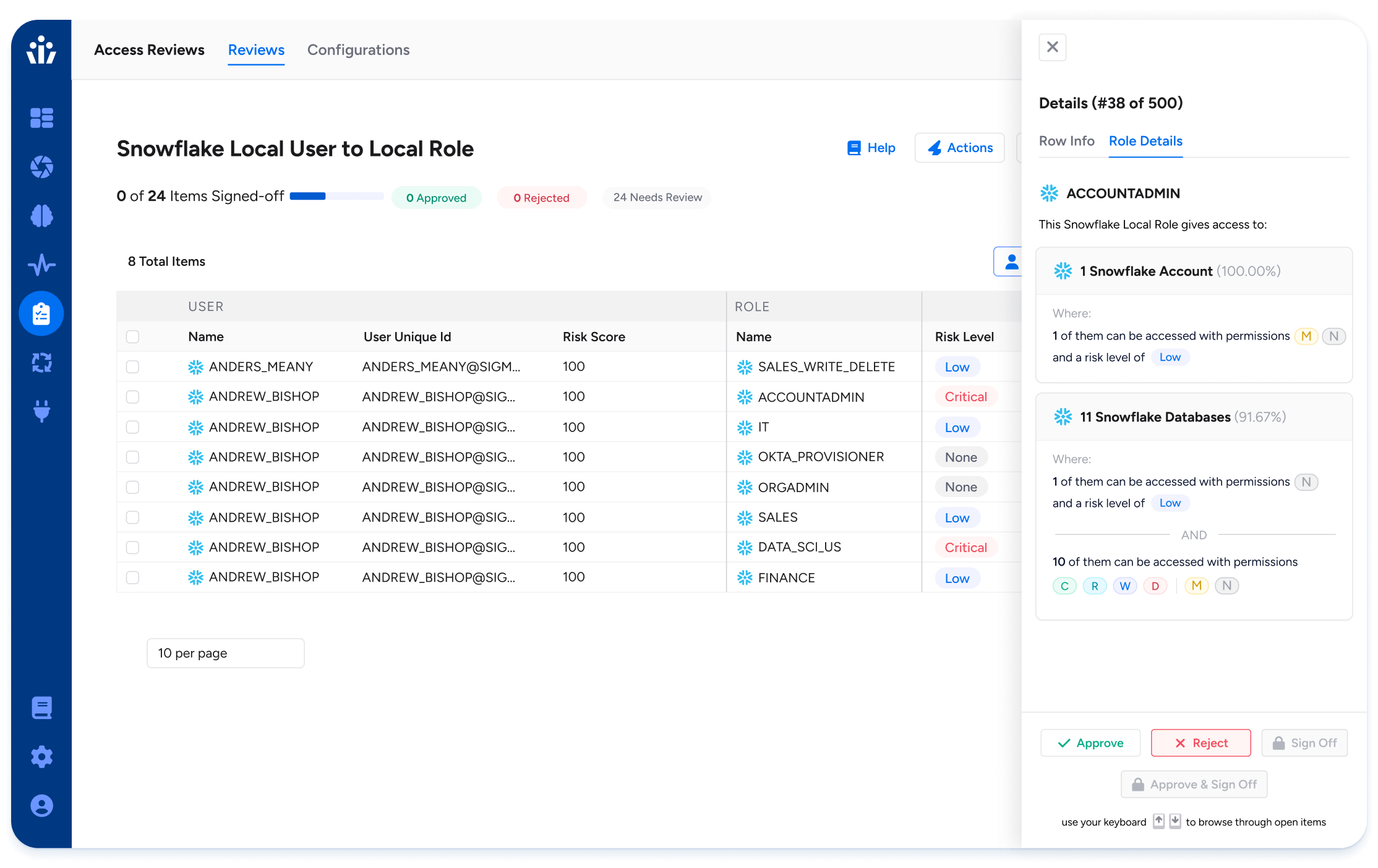
- Activity Insight: Identify whether a user’s entitlement is actively being used, not just if they’ve logged into the application, enabling confident removal of unused entitlements.
- On-demand reviews: Event-driven microcertifications triggered as critical security, user mobility, or privilege escalation events occur.
- Multi-level sign-off: Support for multiple reviewers who both must sign-off on an access review prior to completion and certification.

