A New Era in Identity Security
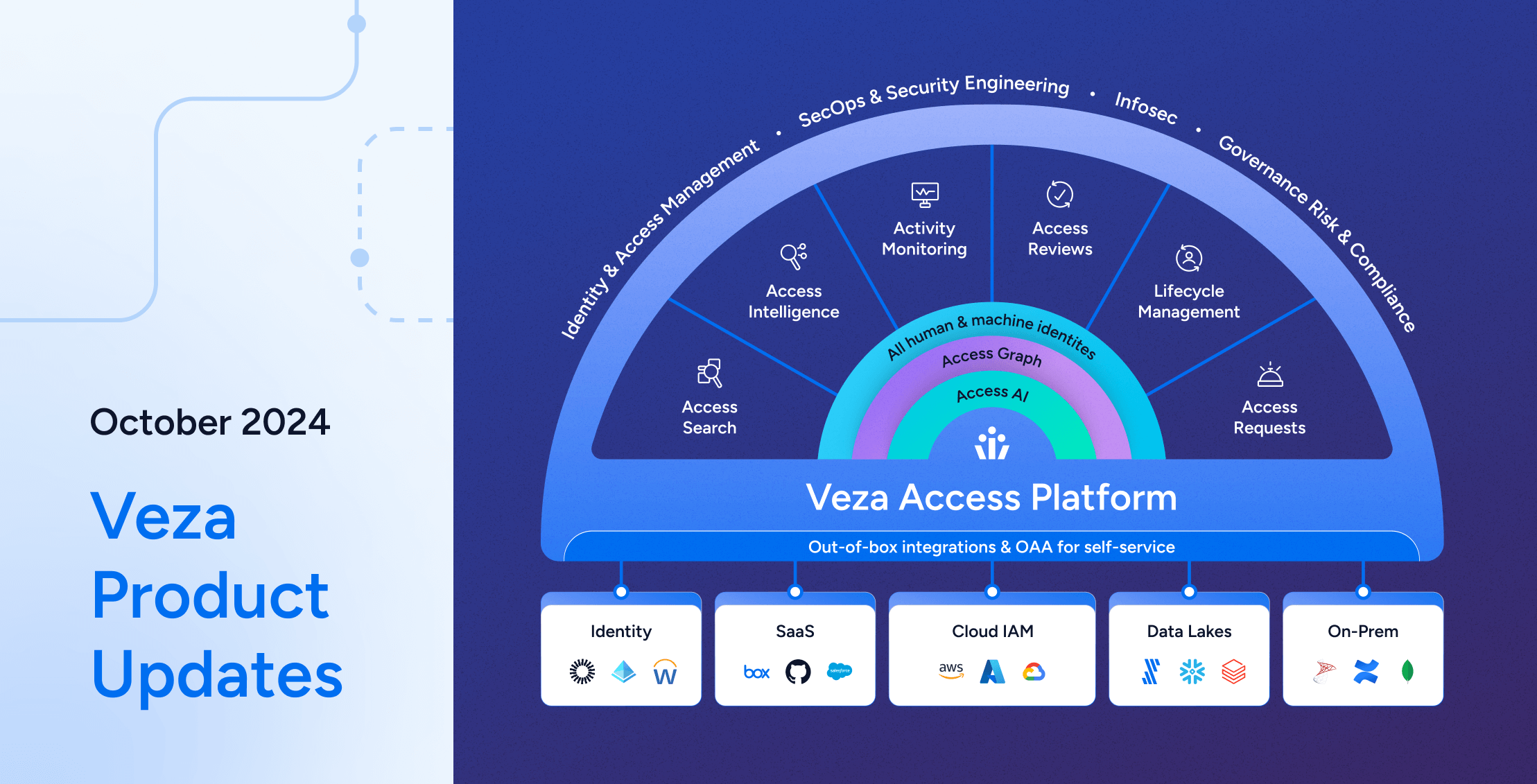
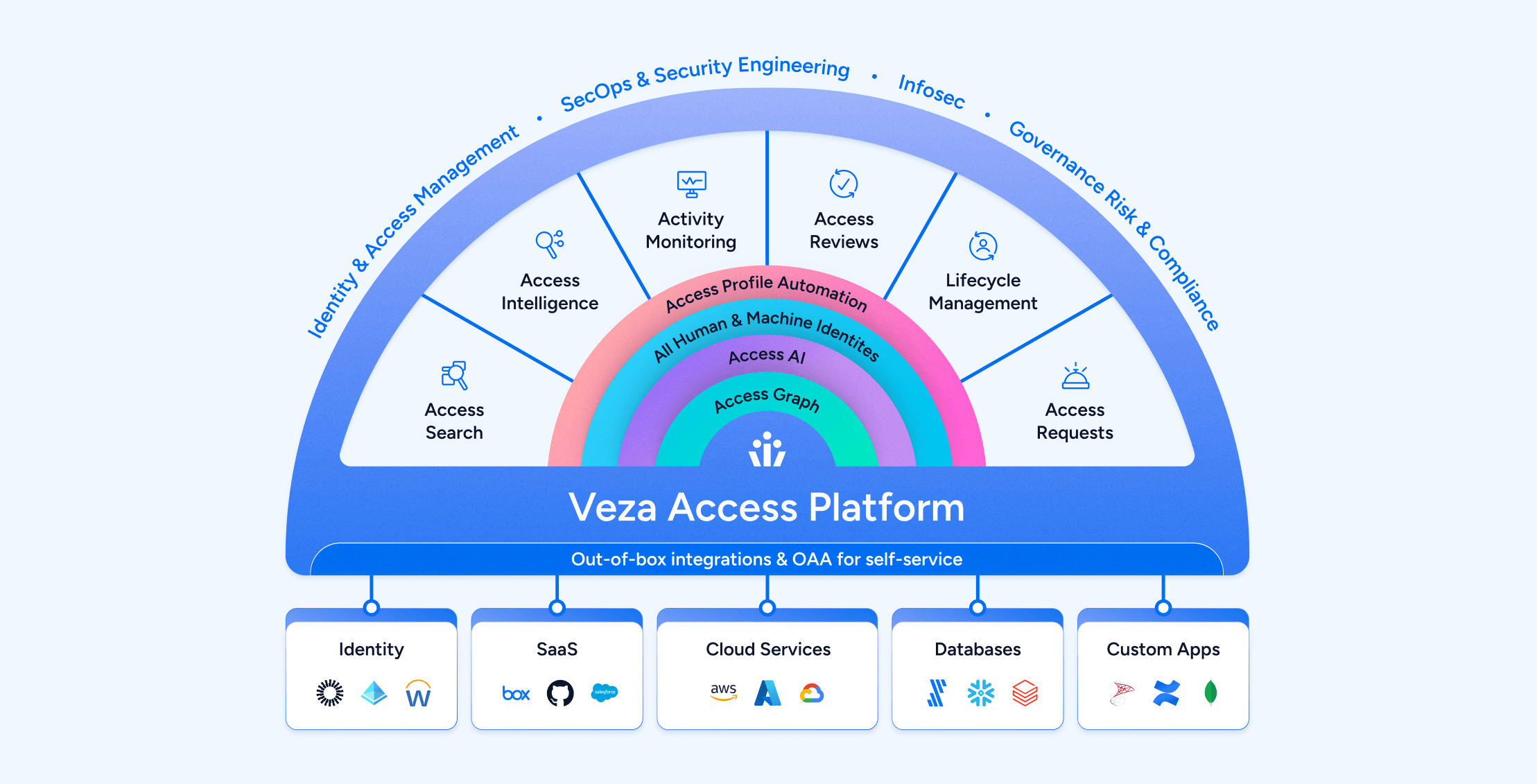
The identity security industry has undergone a seismic shift. At Veza, we developed the Veza Access Graph, the first database of its kind specifically designed to link the granular entitlements to system resources associated with every identity across the enterprise. This pioneering approach allows Veza customers to leverage the data from any angle and confidently answer the question, “who can, has, and should take what action on what data?” Other identity solutions now recognize that visualizing identity through a graph database—not a traditional relational database—is essential and they are building in kind. The world of identity is recognizing the importance of creating a granular view of permissions and entitlements, enabling teams to secure identities with unprecedented clarity.
We are honored to have played a role in spearheading this identity transformation, but we also understand that the work is far from over; the Veza Access Graph is just the beginning. The only defense against the growing identity threat landscape is the principle of least privilege. To achieve and sustain least privilege, we must go beyond visibility; we need Intelligent Access.
Intelligent Access: Pairing Visibility with Automation
Visibility is the first step to solving cybersecurity’s greatest challenge: understanding who can, has, and should take what action on what data. You can’t make effective access decisions without the context that visibility provides; conducting meaningful access reviews, implementing lifecycle management, or processing access requests can only be done effectively and in line with the principle of least privilege when context is provided.
Pairing that permissions data and context with automated processes is the concept behind Intelligent Access. Intelligent Access enables organizations to make good access decisions at the speed of business without sacrificing the granular understanding and managing of entitlements necessary to maintain least privilege.
Assuming that the reality of access aligns with existing legacy role group mappings is a fallacy, access exists at the permissions level. Without a platform that can discover and normalize permissions, IAM will not evolve, and all what we have will just be more of the same ineffective methods we’ve gotten used to.
This lack of understanding of access permissions has plagued one specific area for far too long: the process of requesting and granting access.
Introducing Veza Access Requests
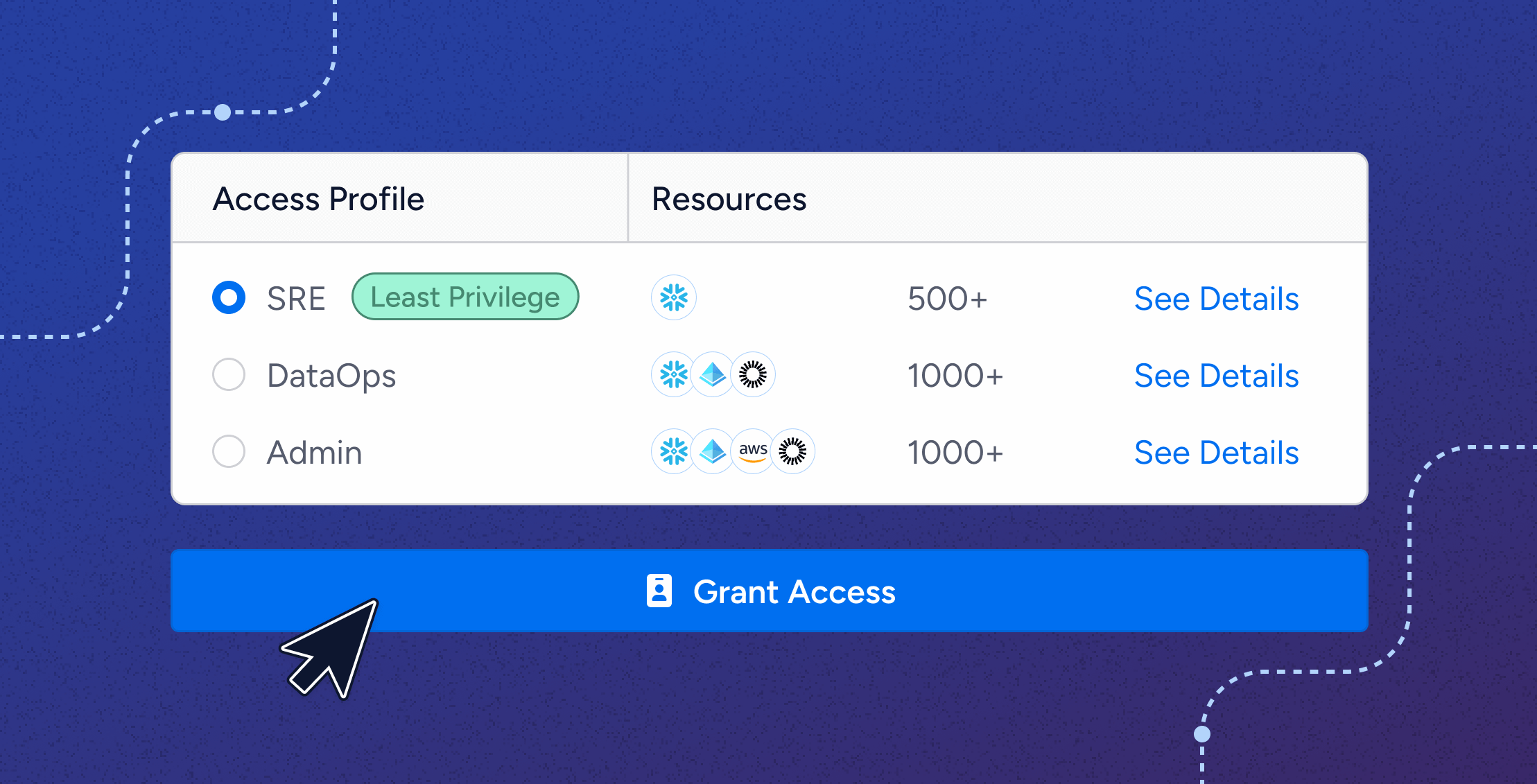
The way most organizations handle access requests today is fundamentally broken. As previously mentioned, traditional identity solutions cannot provide the visibility necessary to grant, monitor and revoke access in line with the principle of least privilege. To make matters more complicated, the scale and urgency of modern business operations don’t allow for much manual investigation and often force teams to take the path of least resistance-not least privilege. An endless stream of requests flows to overburdened IT teams, who are expected to make swift, informed decisions—often without the necessary context. How can IT teams determine the right role to grant without understanding what that role actually enables in terms of actions on data?
The result? Slow decisions, user frustration, and an alarming trend of granting “full admin” rights becoming the default response. IT teams replicate access from existing users or grant excessive permissions just to keep things moving. This leads to privilege creep—a dangerous accumulation of unused access that violates the principle of least privilege.
Our research consistently shows that the majority of granted access goes unused. That’s why we built Veza Access Requests.
The power of Veza Access Requests lies in context. Our platform understands permissions, breaking down silos across systems like:
- On-premise or even custom-built apps via our Open Authorization API
- Identity Providers like Okta and Azure AD
- Cloud Infrastructure providers, like AWS, Google Cloud, Azure, and Oracle
- Cloud Data Platforms like Snowflake,
- SasS applications like Salesforce, GitHub, Zendesk, and Dropbox, and
By using AI and machine learning, Veza automatically defines new roles, recommends access, and ensures that decisions align with the principle of least privilege.
IT teams retain oversight where needed, but Veza handles the heavy lifting. Users can confidently request the right access—and even receive immediate grants via self-service. Business moves faster, security improves, and organizations gain confidence that every access decision is correct.
Unlike traditional IAM, IGA, or PAM tools, Veza’s architecture is uniquely built to speak the language of permissions. To prevent privilege creep, Veza provides features like just-in-time access and automatic expiration, eliminating standing access that accumulates unused and unchecked.
The Destination: Achieving Least Privilege at Scale
Our mission lies in empowering organizations to achieve and maintain the principle of least privilege across the entire enterprise. This requires more than tools; it demands a holistic approach: visibility into permissions, intelligent decision-making, and a centralized control plane to visualize, monitor and remediate access.
At Veza, we see this as the ultimate destination: a world where identity management is seamless, secure, and aligned with the needs of the business. Veza’s Access Requests is the next big leap toward that world.
The future of identity security is here, and it starts with the right access, every time.