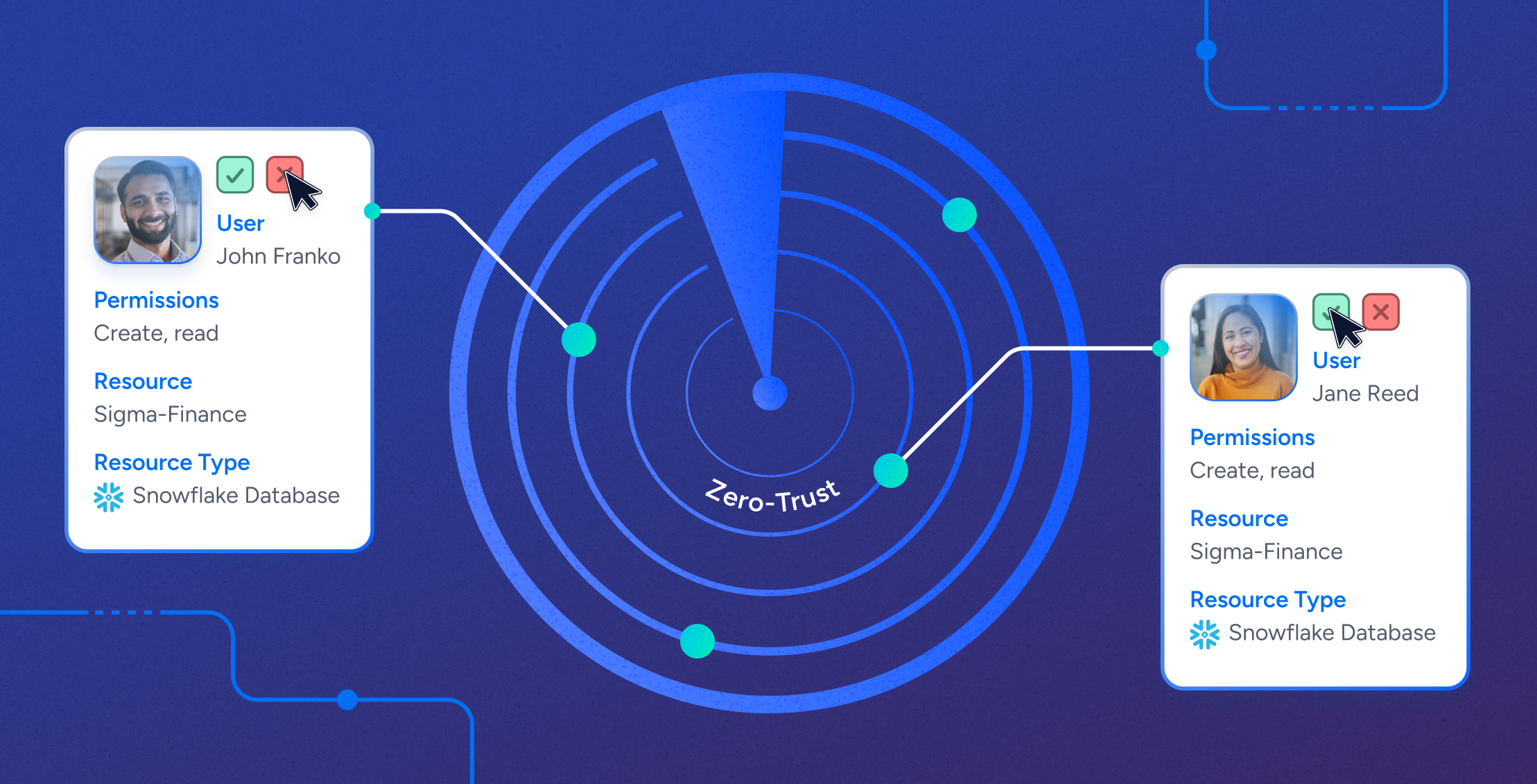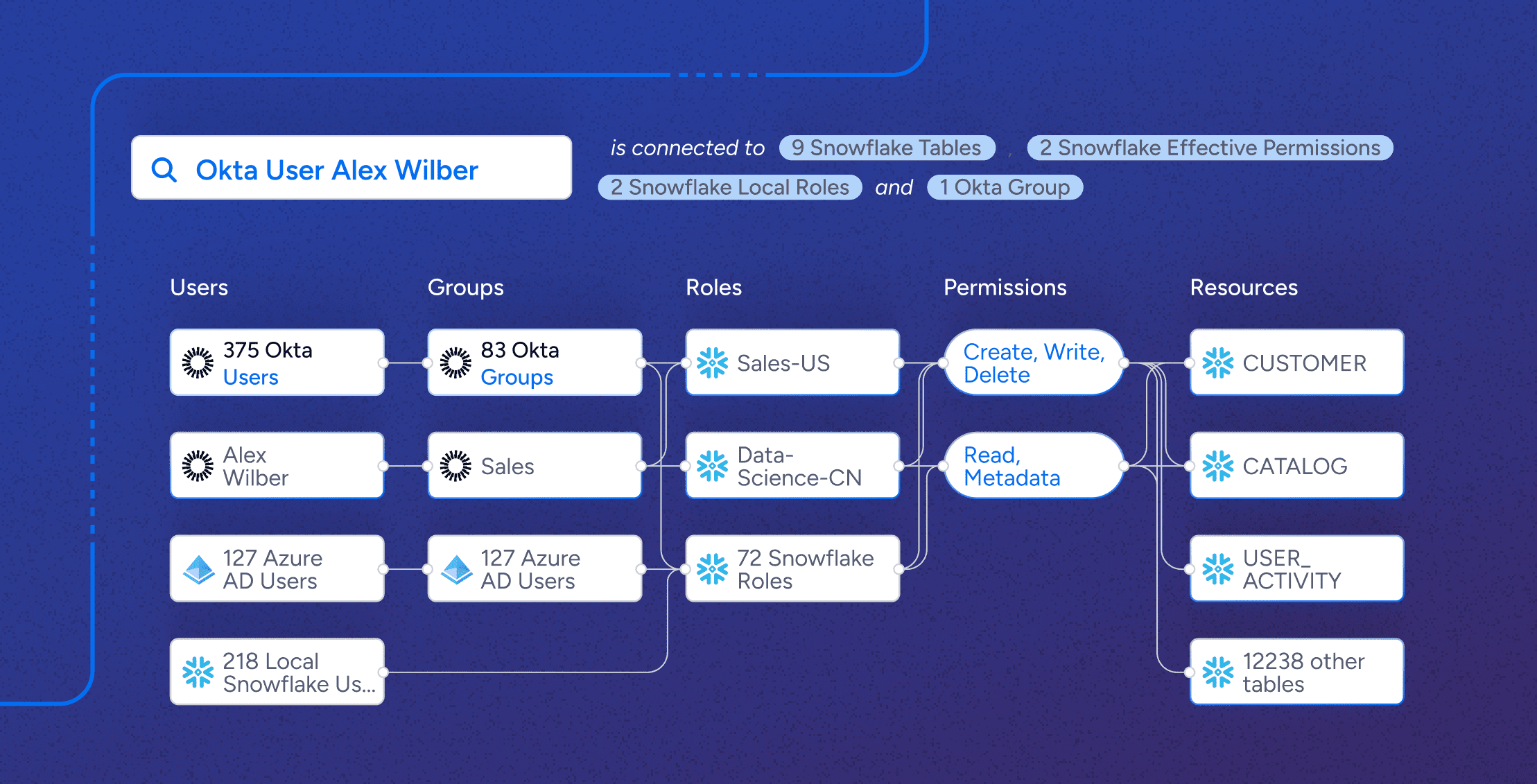
Most modern businesses face the same problem when managing identities and security: striking the right balance between easy and secure access to applications, data, and resources to perform one’s job function, and the safety and privacy of information. This challenge is widespread, and with 80% of cyberattacks using identity-based attack methods in 2023, it’s not only serious—it’s far from solved.
This is where authentication and authorization come into play. Together, they hold the key to letting the right people access the right resources with the appropriate permissions without sacrificing productivity.
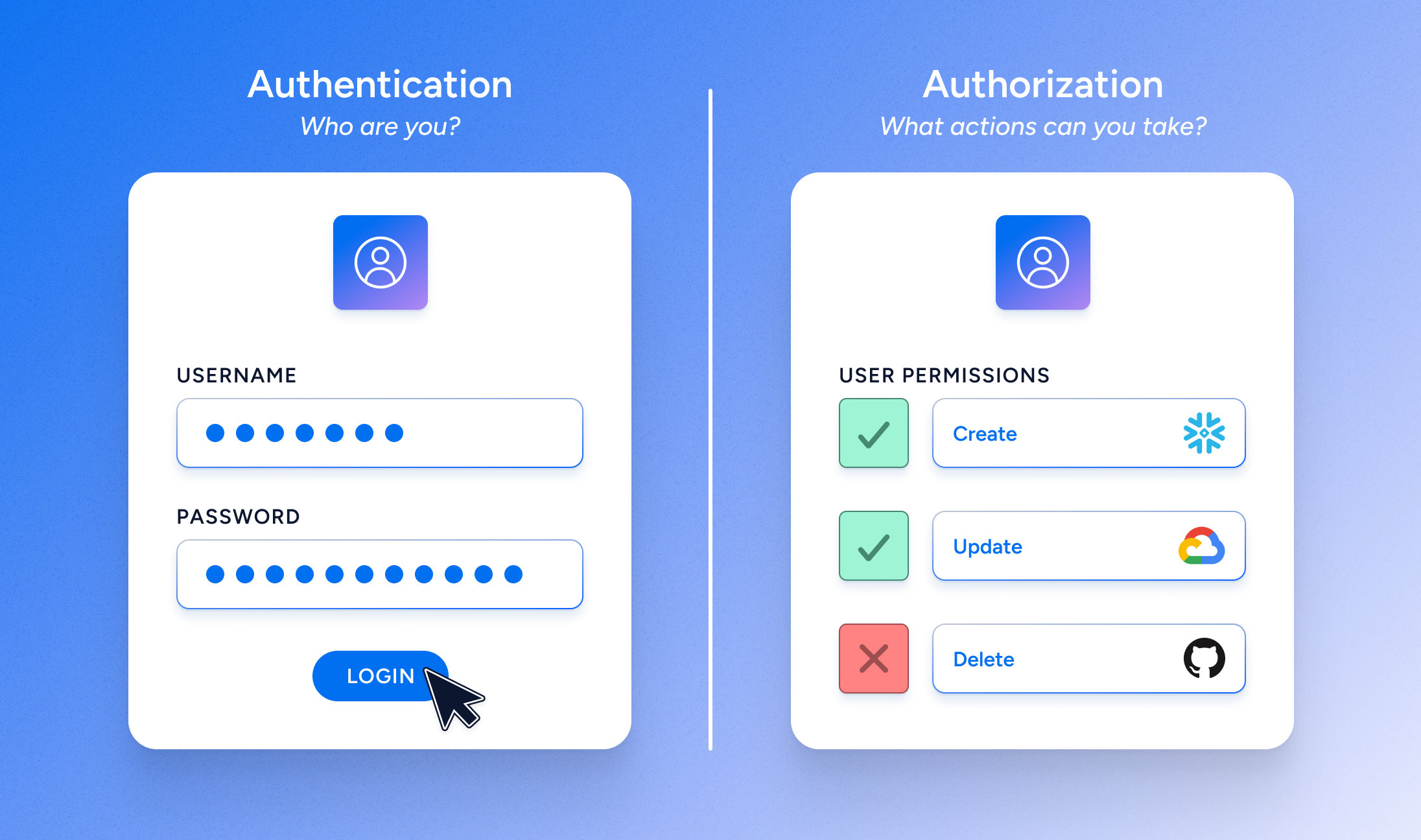
Authentication is about verifying who someone is, and authorization is about what they can do. Both are important for keeping company data safe and making sure only the right people with the right permissions can access sensitive information.
Because authentication and authorization sound similar, it’s easy to mix them up. This guide has everything you need to know about authentication vs authorization, from what they mean to how they differ, and why they are both critical to identity security.
What is Authentication?
Authentication is the process of verifying a user’s identity by confirming an individual is who they claim to be before granting them access to a requested resource. This verification process is especially important in today’s digital world, where virtual credentials and biometric data have replaced our physical presence. In most cases, it can be achieved through three primary means:
- Something a Person Knows: Like a password, PIN, or security question.
- Something a Person Has: Like a cryptographic identification device or token.
- Something a Person Is: Like biometric identifiers including fingerprints or facial recognition, which are unique to the individual and cannot be easily duplicated or lost.
In many ways, authentication is like a digital gatekeeper, making sure that only users with the right credentials are allowed through.
Types & methods of authentication
The evolution of authentication methods has significantly improved the security and user experience of accessing digital services. Here’s a closer look at the types and methods of authentication available today:
- Passwords: Still the most common form of authentication today. They’re easy to implement, but they also come with the risk of being stolen (either physically or online), guessed, or cracked.
- One-Time Pins (OTP): This method is more secure than passwords and works by generating a single-use code sent via email, text message, or physical token. OTPs are often effective because they’re changeable and time-sensitive, which makes them harder to intercept and reuse.
- Token Authentication: Rather than relying on something the user knows (like a password), token authentication grants access using something the user possesses, like a security token or a smartphone app. These tokens generate codes or digital signatures that verify the user’s identity.
- Single Sign-On (SSO): SSO simplifies authentication by allowing users to access multiple apps with a single set of credentials. This method reduces the number of passwords a user has to memorize, and improves the overall user experience.
- Biometric Authentication: Using unique physical characteristics such as fingerprints or facial recognition, biometric authentication is highly secure—and it’s becoming more common in everyday technology for quick and secure access to devices and applications.
- Multi-Factor Authentication (MFA): By combining two or more authentication methods (e.g., a password and a token), MFA significantly improves account security. Since it requires multiple pieces of evidence before granting access, it can be a powerful tool against unauthorized access.
- Passwordless Authentication: This emerging trend is trying to eliminate passwords altogether by instead relying on biometrics, software tokens or certifications, mobile devices, or security keys.
Authentication Challenges
Despite the advancements in authentication technologies, managing the process is still a significant lift for most organizations. Here’s a closer look at some of the key challenges:
- Diverse Identity Types: Today’s workforce includes both human and non-human entities (like IoT devices, service accounts, and bots), which requires a nuanced approach to authentication rather than a one-size-fits-all strategy.
- Password Vulnerabilities: Despite their susceptibility to weakness, guessability, and theft, passwords will likely stay a significant component of authentication methods for the foreseeable future.
- Evolving Authentication Techniques: The shift toward more secure and user-friendly authentication methods also creates challenges in infrastructure investment and training, often leading to a gap between the availability of advanced solutions and adoption rates.
- Compatibility with Legacy Systems: Organizations using a mix of modern and legacy systems often adopt a hybrid approach to authentication, blending newer methods with traditional passwords for compatibility and security—at the cost of added complexity.
What is authorization?
Once a user’s identity is confirmed via authentication, the next step is authorization.
Authorization determines what an authenticated user is allowed to do within a system. It governs access to resources and applications by specifying what actions a user can perform (like reading, creating, or modifying data). Authorization ensures that users have appropriate permissions, which contributes to an organization’s overall security and efficiency.
Types & methods of authorization
How organizations approach authorization can vary widely. Here’s a breakdown of the primary methods used today:
- Discretionary Access Control (DAC): Here, authorization is based on the user’s identity and permissions, and resource owners can grant other users access at their discretion.
- Mandatory Access Control (MAC): Unlike DAC, MAC assigns access rights based on information clearance and classifications determined by a central authority.
- Role-Based Access Control (RBAC): RBAC assigns permissions to roles rather than individual users. Users are assigned roles based on their job functions.
- Attribute-Based Access Control (ABAC): ABAC is a flexible strategy using policies to determine access rights. These policies can consider multiple attributes, including user attributes (like department or role), resource attributes (like data sensitivity), and environmental attributes (like time of day or location).
- Policy-based Access Control: In PBAC, access is determined by combining business roles with policies. PBAC is a flexible solution that lets you adjust entitlements based on various evaluated parameters and in response to any requirement changes.
Authorization Challenges
Despite authorization’s critical importance for securing access to resources and applications, implementing it effectively often comes with challenges. Ultimately, these hurdles come down to the dynamic nature of business, the complexity of permissions management, and the evolving cyber threat landscape.
- Fine-Grained Data Access: Many organizations lack the tools to manage permissions at the level of detail required to protect resources adequately—broad authorization policies can expose data to risks like data breaches and ransomware attacks.
- Maintaining Least Privilege: Following the principle of least privilege—ensuring that each user has access and permissions only to the resources and apps they need for their role—can be complex due to organizational changes (like promotions, departmental shifts, or project reassignments). This can lead to permission creep, where users accumulate access rights beyond what is necessary for their job.
- Lifecycle Management: Managing user permissions throughout the employment lifecycle, from onboarding to offboarding, means authorization systems must be dynamic, automatically updating permissions as users’ roles change.
- Governance and Compliance: Ensuring compliance with internal policies and external regulations is daunting—incorrectly configured permissions can quickly lead to compliance violations, unauthorized access to sensitive data, and potential legal repercussions.
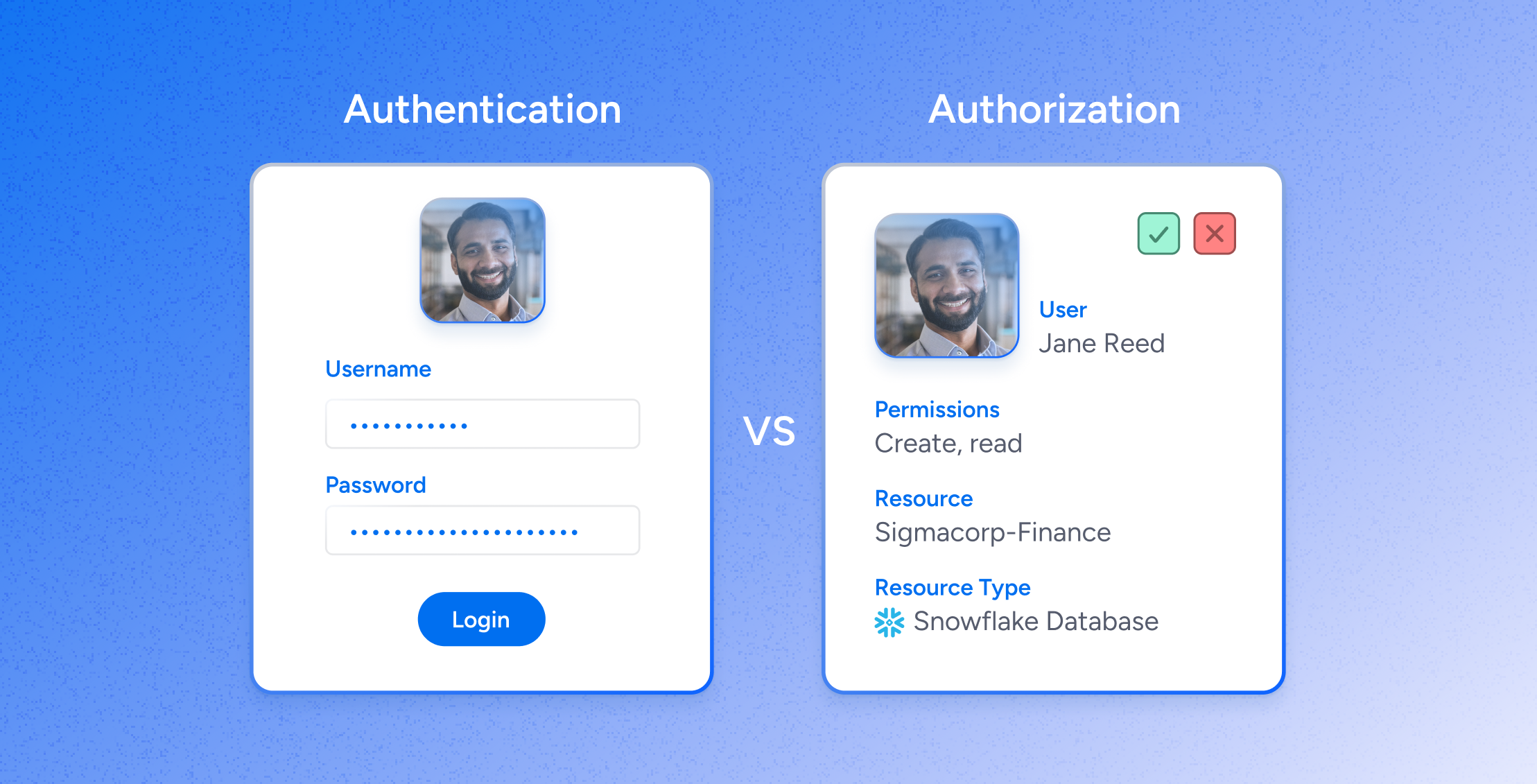
The terms “authentication” and “authorization” represent two distinct aspects of access control.
To recap, authentication is verifying a user’s identity. It involves confirming a user is who they claim to be before granting access to a system. This is typically done through credentials like passwords, OTPs, or biometric authentication like fingerprint or facial recognition. It’s the first step in the security process and ensures that access requests come from genuine users.
Once authentication is successfully completed, authorization determines what that authenticated user can do within the system at run-time. This involves assigning permissions and access rights to the user, dictating which resources or applications they can use and what actions they can perform (e.g., read, write, delete). Authorization specifies the scope of access granted to a user based on their role or identity.
Authentication vs Authorization: The Differences
- Purpose: Authentication verifies a user’s identity to make sure they are who they claim to be. Authorization determines the resources and actions available.
- When it Happens: Authentication happens first, followed by authorization.
- How it Works: Authentication relies on credentials and identity verification methods. Authorization uses defined permissions and policies to grant or deny access.
- How it Collects Information: Authentication collects and verifies identity information. Authorization requires knowledge of the user’s permissions and the resources or actions they’re attempting to access.
Similarities between Authentication & Authorization
Despite their distinct roles, authentication and authorization share several key similarities that contribute to their frequent conflation in information security.
For starters, both processes are fundamentally concerned with the concept of identity, and each serves as an important component in the broader framework of access control. In many systems, both authentication and authorization involve using digital credentials and tokens and both processes aim to improve the security and privacy of digital systems.
Ultimately, authorization cannot occur without prior authentication, underscoring just how intertwined these processes are for system security. Yet, without authorization, the system lacks the mechanism to control what a user can do, which makes it possible for them to access or alter information beyond their clearance.
More About Authentication vs Authorization
Let’s answer some frequently asked questions about authentication and authorization.
What’s the difference between identification vs authentication vs authorization
Identification happens when an entity claims an identity via username, process ID, smart card, or any other means that uniquely identifies an individual or subject. However, this claim does not prove the identity but merely asserts it.
In the context of authentication and authorization, identification technically comes before authentication, which comes before authorization. Identification alone only asserts an identity without proving it–which makes authentication necessary to verify the claim.
What’s the difference between authorization vs user provisioning
Authorization and user provisioning are often confused, but they address different aspects of access control. User provisioning is the process of creating, managing, and disabling user accounts and their access to resources within an IT infrastructure.
While user provisioning is an important part of access management, it doesn’t handle the nuanced permissions and access levels that authorization does.
Authorization is contextual, including factors such as the user’s role, the data’s sensitivity, and the time and location of access. While user-provisioning systems are great for managing account creation and assignment to certain groups and roles, they often lack the sophistication to handle this level of context.
Relying solely on user provisioning for authorization can create several issues. For instance, changes made directly in an application might bypass the provisioning structure, leading to inconsistencies in permissions. Plus, user-provisioning systems may lack the agility to manage ad-hoc access requests or roles changes, which could expose resources to unauthorized access.
What’s the difference between authentication vs authorization vs access control
While authentication and authorization are important parts of access management, they aren’t the same thing as access control. Access control is the processes and mechanisms that regulate access to resources—it’s the comprehensive framework that authentication and authorization fall underneath.
Is SSO used for authentication or authorization?
SSO (Single Sign-On) is a popular method of authentication that allows individuals to access multiple apps and services with a single set of credentials (like Gmail).
Is OAuth used for authentication or authorization?
Open Authorization (OAuth) is an authorization framework for third-party services to exchange web resources on behalf of a user.
Is SAML used for authentication or authorization?
Security Assertion Markup Language (SAML) is a standard for exchanging authentication data between parties, particularly identity providers and service providers.
Is RBAC used for authentication or authorization?
RBAC (Role-Based Access Control) is used for authorization and regulates access to resources based on the roles of individual users within an organization.
Is ABAC used for authentication or authorization?
ABAC (Attribute-Based Access Control) is used for authorization and uses policies that evaluate attributes (or characteristics) of users, the environment, or the resources to make authorization decisions.
Gain visibility & control of your authorization data
Veza built a solution for modern organizations to visualize, manage, and secure permissions across all systems and all identities. Veza’s Access Graph connects quickly to any enterprise system, on-premise, cloud, or SaaS application, monitoring both human and non-human identities all in one place.
It lets you see beyond roles and groups to understand the detailed permissions and entitlements of each user for each application and resource, translating esoteric permissions into simplified business terms so you can make more informed decisions.
With Veza, organizations can confidently answer the question: “Who can and should take what action on what data?”