As businesses increasingly harness the power of artificial intelligence (AI) to drive innovation and competitive advantage, many technology leaders are overlooking a critical foundation that can make or break their AI initiatives: identity security. AI’s true potential is unlocked when it’s trained on and analyzing well-curated, governed, and high-integrity data within an enterprise. Put simply, an AI model is only as accurate and useful as the data that is put into it. Security and trust teams play a vital role in enabling innovation by partnering with business leaders. They focus on elements such as data quality, data protection, and controlling permissions to data, ensuring the security and integrity of the AI-driven processes upon which businesses now depend.
The Promise and Perils of AI in the Data-Driven Enterprise
AI holds immense potential to transform businesses, from automating tedious tasks and deriving insights from vast amounts of data, to enabling more personalized customer experiences and empowering humans to up level their abilities. However, as organizations rush to adopt AI, they often neglect the security implications. AI systems rely heavily on large datasets, complex algorithms, and interconnected services, creating new attack surfaces and vulnerabilities. Without proper identity security controls, unauthorized access to sensitive data could lead to compromised AI models, inaccurate insights, and erosion of trust.
Identity Security: Enabling Secure, Data-Driven AI
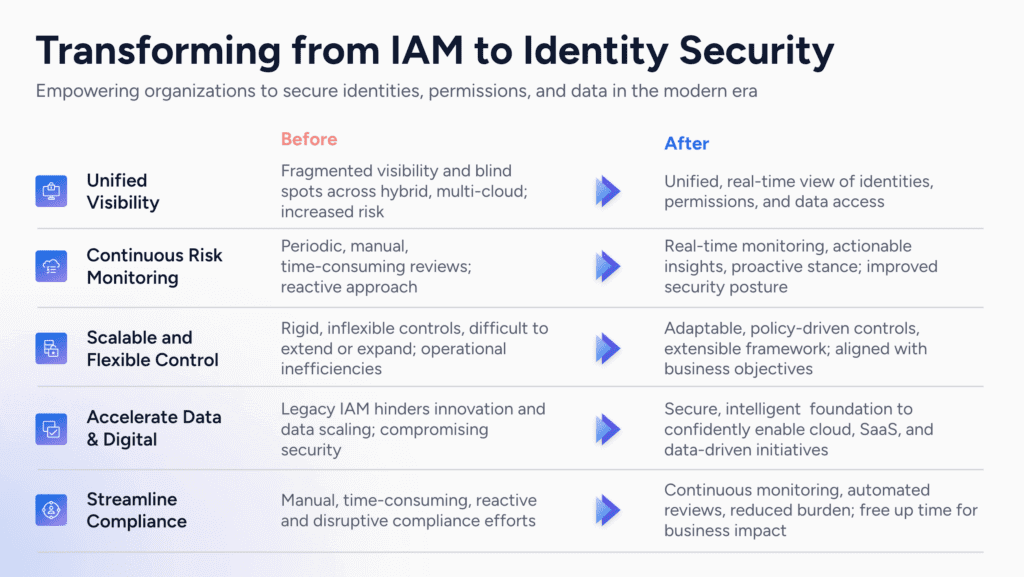
Legacy IAM approaches often hinder innovation and data scaling while compromising security. Traditional tools have blind spots because they rely on data models built for an era with on-premises architectures and fully-trusted networks, when it was sufficient to govern users via groups and role names. Furthermore, these IAM solutions were developed and deployed to address service levels, operational efficiency, and workflows. While these aspects remain important, they are no longer sufficient in the face of today’s cyber threats and the critical need to protect sensitive data across an expanding number of enterprise platforms.
In contrast, a focus on identity security at scale provides a secure, intelligent foundation that empowers organizations to confidently enable cloud, SaaS, and data-driven initiatives. By focusing on data protection and granular control over permissions to data, an effective identity security platform enables businesses to:
- Unlock data-driven insights with robust security controls
- Ensure high-quality, well-governed data for accurate and reliable AI models
- Enforce fine-grained access controls for sensitive data
- Manage entitlements and ensure data security across diverse data platforms
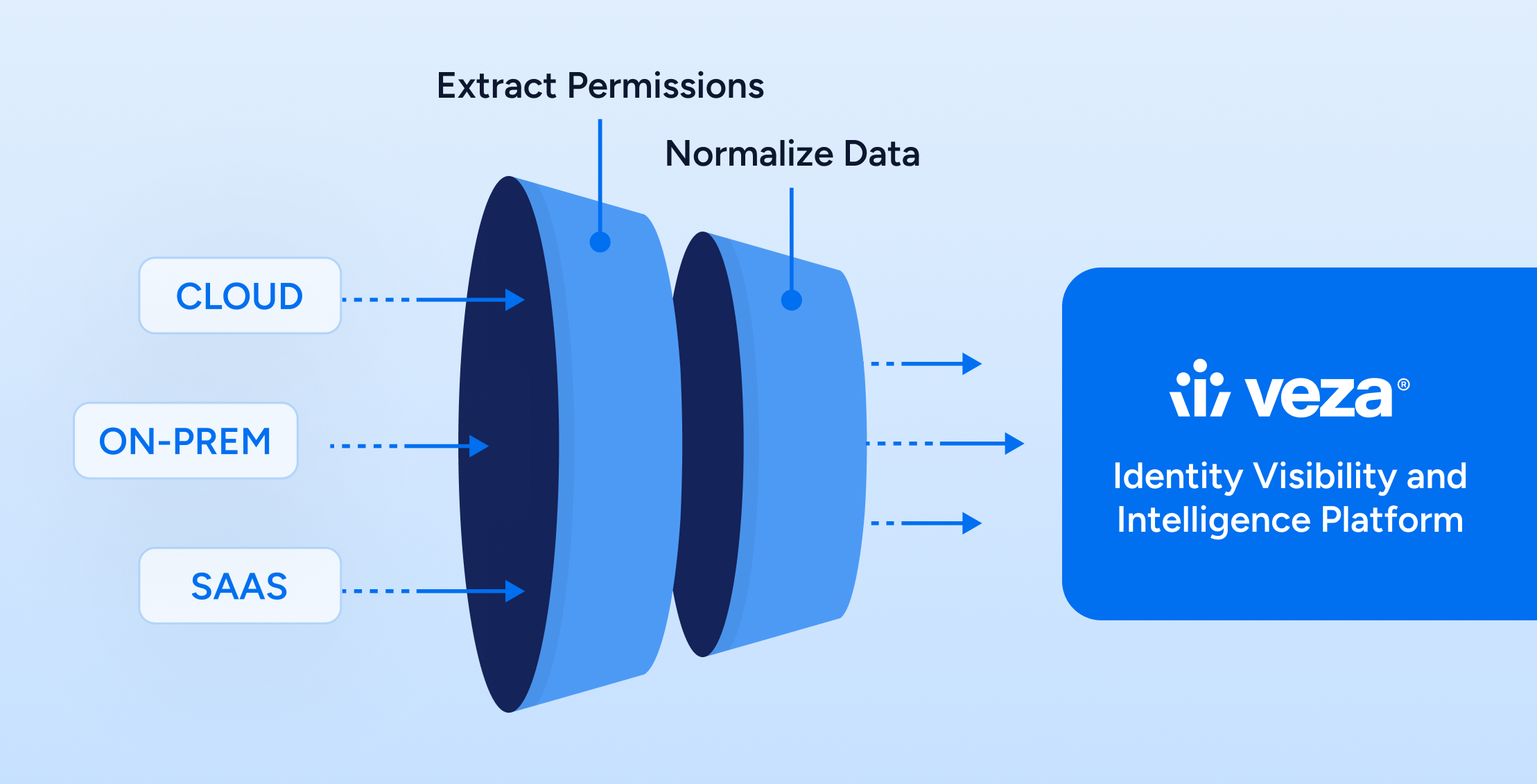
Identity security delivers substantial value to Identity & Access Management, Security Operations, Business Data Owners, Compliance, and Audit teams by providing a unified view of data platform access rights and enforcing granular controls across cloud data platforms such as Databricks, Snowflake, AWS RedShift, Google BigQuery, and on-premises platforms like Microsoft SQL Server. This foundation can provide confidence and control across today’s highly variable and complex technology landscape, spanning cloud infrastructure, on-premises systems, data platforms and SaaS environments.
An approach to identity security to unleash the power of AI focuses on three key pillars:
- Visibility: A unified view of all identities (human and non-human), their permissions, and the data they can access across multi-cloud and hybrid environments is pivotal. This comprehensive visibility is necessary to understand the complex web of interactions between AI systems, data sources, and users.
- Intelligence: Access graph technology transforms raw permissions data into actionable insights. It enables businesses to uncover excessive permissions, identify anomalous access patterns, and make informed decisions about access control policies. For AI initiatives, this intelligence helps ensure that only authorized users and systems can access sensitive data and algorithms.
- Control: Businesses can enforce granular, least-privilege access controls across their technology ecosystem. This means granting AI systems and users the minimum permissions necessary to perform their functions, reducing the blast radius in case of a breach. Automated access reviews and continuous monitoring ensures that permissions are regularly validated and any deviations are promptly addressed.
Enabling Responsible AI Innovation
By providing a strong identity security foundation, organizations are empowered to take on the challenges of the data and digital age with confidence and resilience. With full visibility and control over who can take what action on what data, businesses can innovate with AI more responsibly and with greater confidence. They can protect sensitive data used to train AI models, secure access to AI algorithms, monitor for anomalous access patterns, ensure compliance with data privacy regulations and ethical AI principles, and build trust with customers and stakeholders by demonstrating responsible AI practices.
The Path Forward
As businesses strive to unlock the full potential of AI in the data-driven enterprise, they must not overlook the critical role of identity security. Veza’s focus on data protection and controlling permissions to data provides the essential foundation for secure, responsible, and high-quality AI initiatives. By embedding identity security into the core of their data and AI strategies, organizations can harness the power of AI with greater confidence, resilience, and trust.
In the era of AI-driven business, identity security is no longer just a technical concern – it’s a strategic enabler to drive responsible innovation and competitive advantage. As a technology leader, I believe investing in a strong identity security foundation is one of the most important steps organizations can take to set their data-driven AI initiatives up for success.