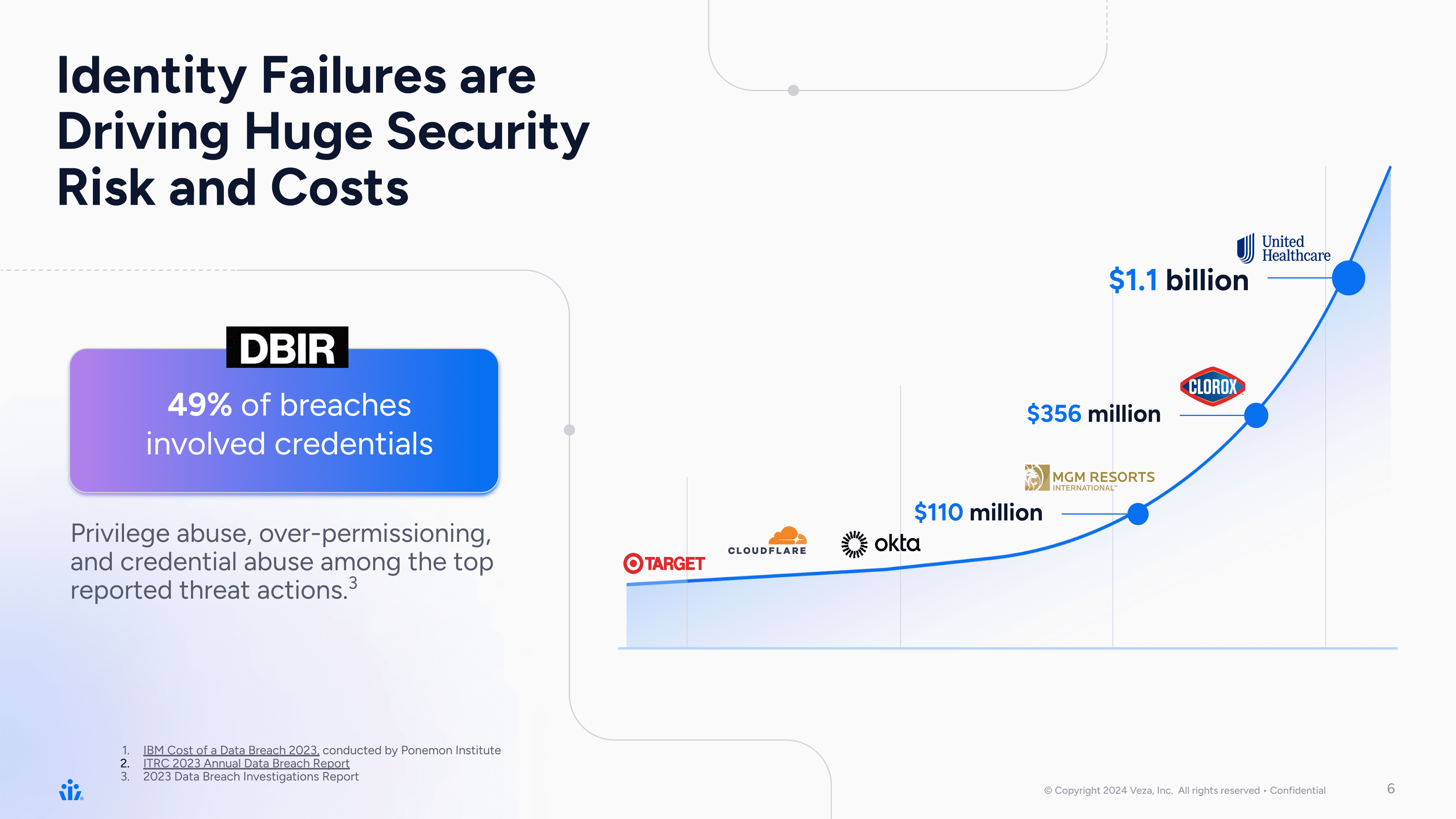
We founded Veza in March 2020, with an insight that in spite of all the identity and security tooling that has existed in the world, no one has been able to crack the code on – who can take what action on what data. From Colonial Pipeline in 2020 as the wake up call to fast forward four years to 2024, we as an industry have now experienced the first $1 billion dollar breach with Change Healthcare. All these breaches from – Target, Okta, MGM, Microsoft, etc. – have brought to the forefront the biggest challenge of how weak and porous our identity access infrastructure is – and, now is the time for the industry to wake up and take action.
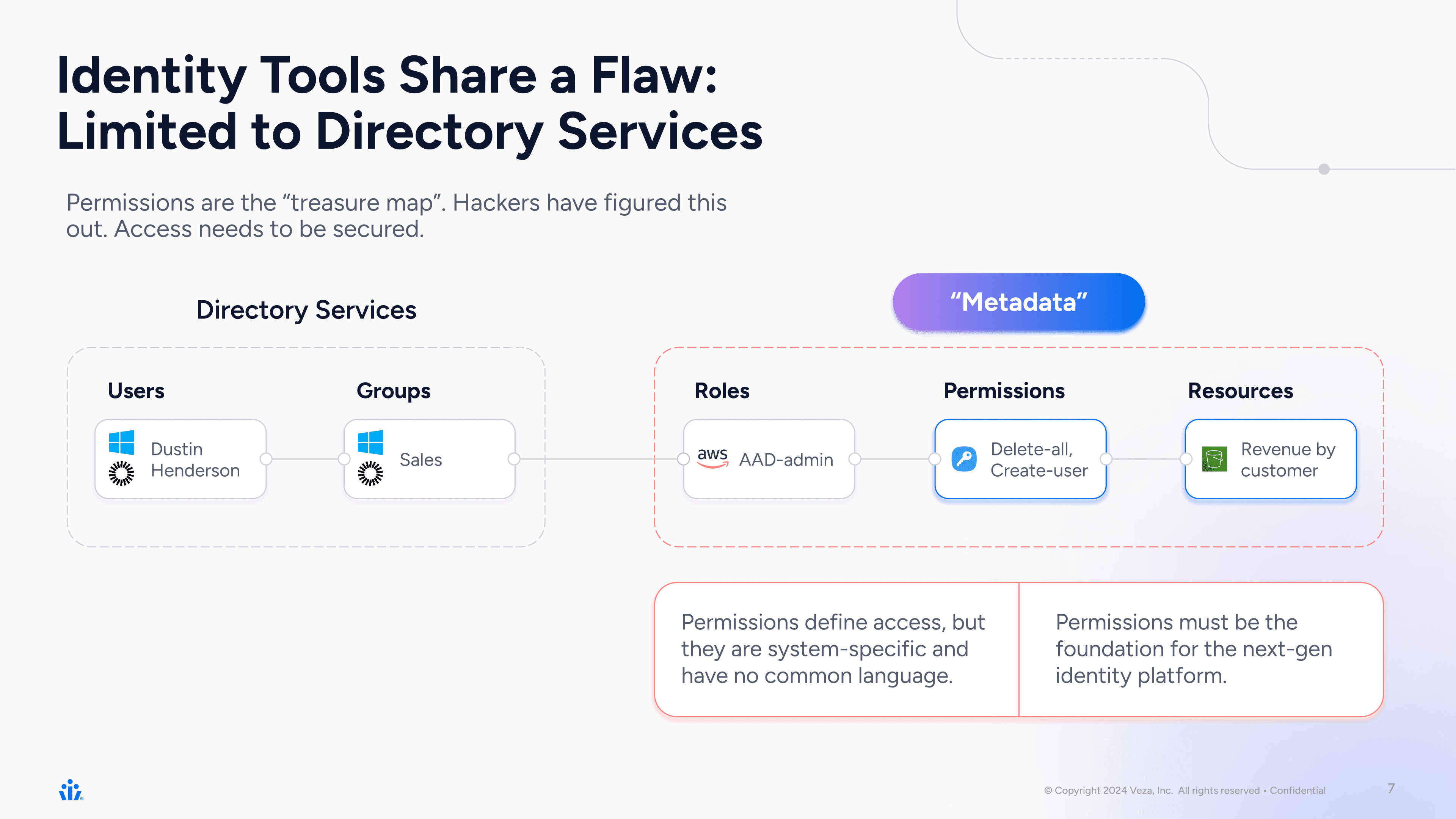
Our intuition – also from early 2020 – that all the major identity tools of today Microsoft Active Directory, Okta , Google Workspace, etc.) are just directory services with users and groups. Directory services with users and groups give no insight to access permissions, the true form of identity. Access permissions define who can take what action on what data, all these access permissions are system-specific, and have no common language. We must organize these permissions in a canonical data model that associates identities to their effective access – only then can we truly start to work towards the principle of least privilege.
Today, four years since our founding, we are even more excited with the opportunity that we see in front of us to truly help secure organizations worldwide. We deeply believe that we will define and lead the modern Identity Security category. With Identity Security, we aim to deliver core identity products for modern IGA (Identity Governance and Administration), Cloud PAM (Privileged Access Management), Identity Security Posture Management (ISPM), and Next-Gen Identity Provider with Veza Identity.
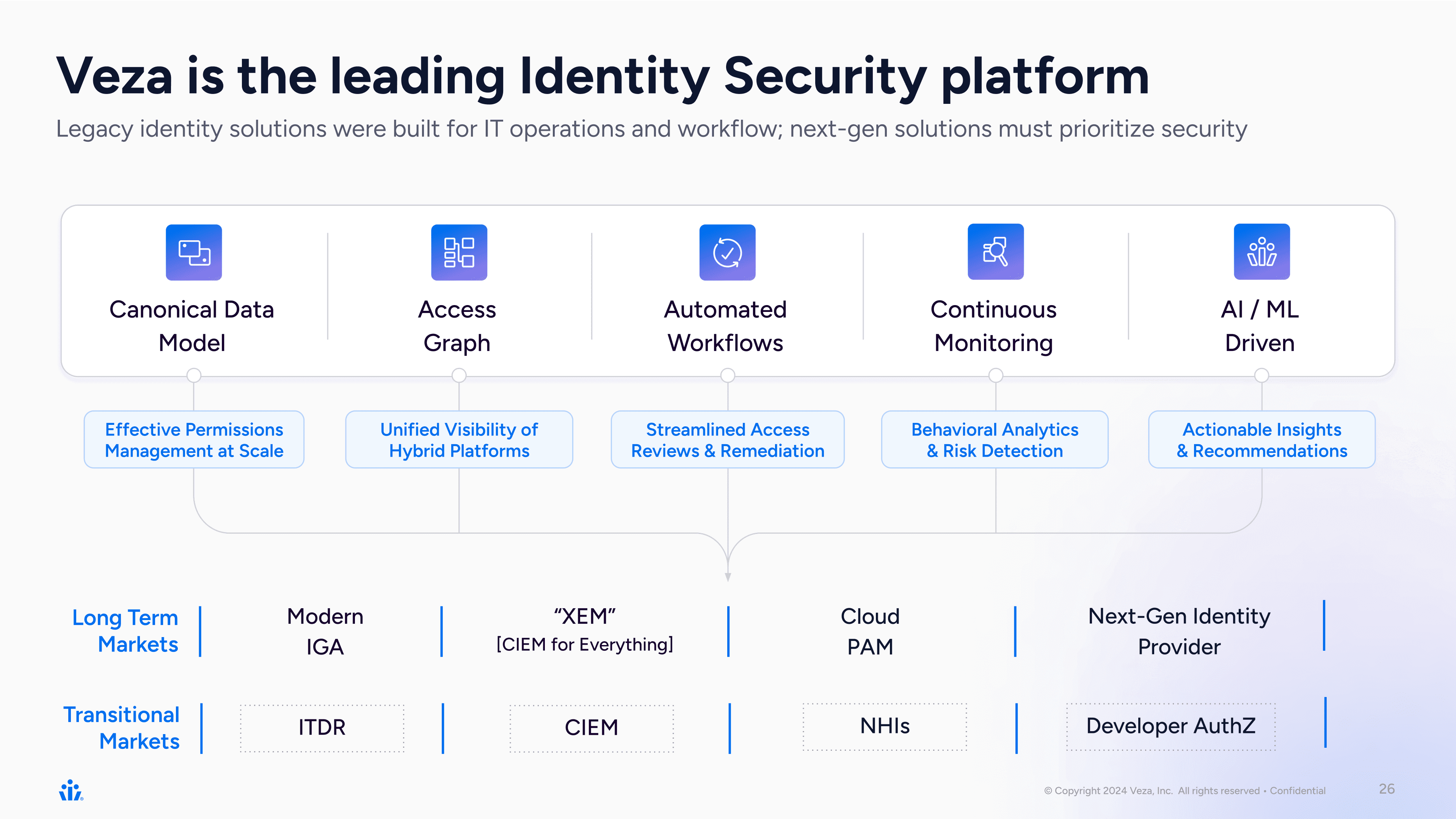
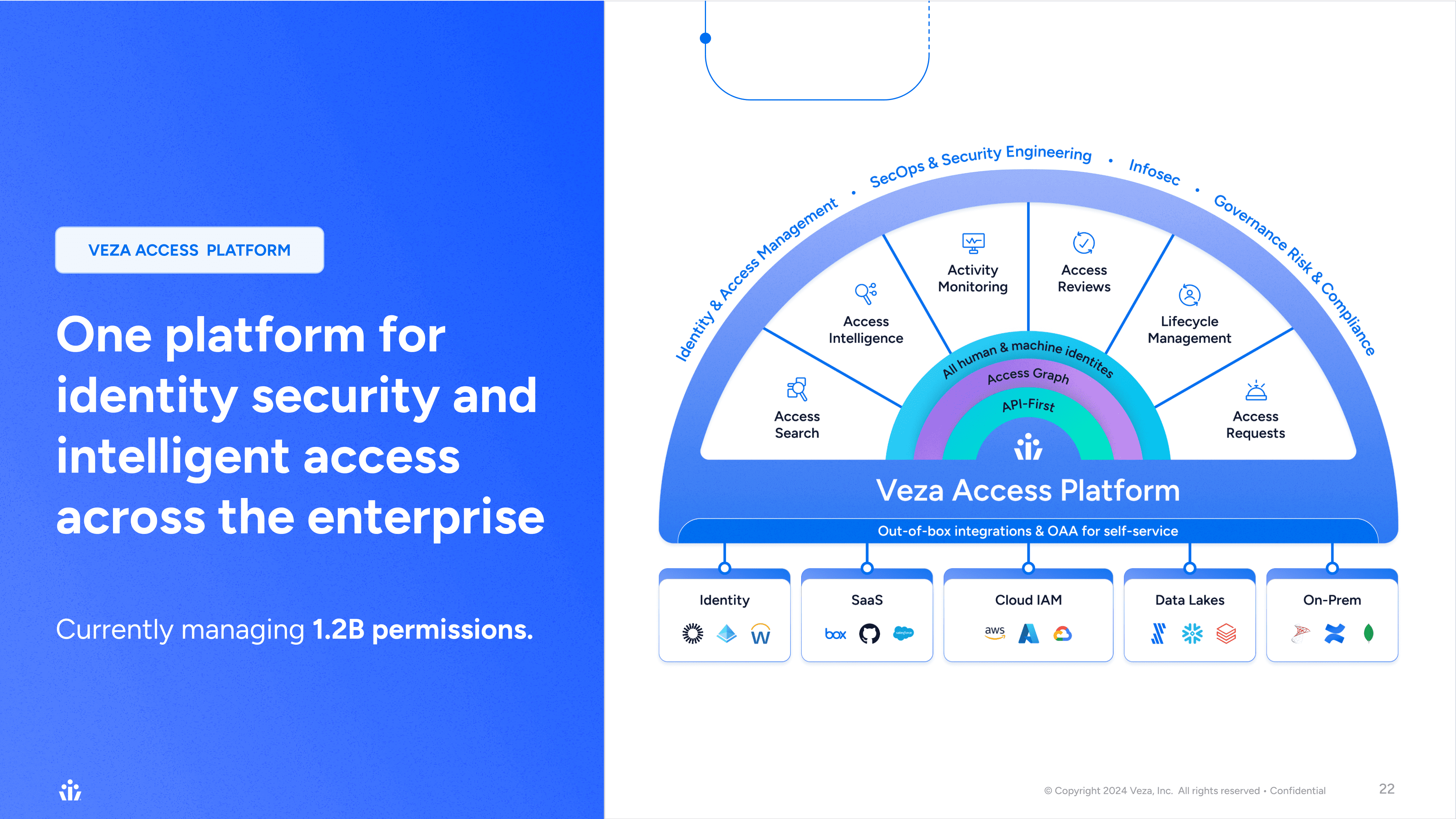
Veza, The Identity Security Platform
Use cases that we are focused on:
- Access Search: Identity Debt, Identity Hygiene, IAM Technical Debt
- Access Intelligence: Outlier Detection, Role Analytics, SoD Policies, Access Risk Rules, etc.
- Access Monitoring: Over-permissioned acces score
- Access Workflows: Access Reviews, Insider Threat Workflow, Incident Management Workflow, Segregation of Duty Workflows, etc.
- Lifecycle Management: Provisioning, De-provisioning, Joiner, Mover, Leaver
- Access Request: Role Recommendations, Role Assignment, Self Service Access, Access Policy Automation
Download the report and check out our webinar where #cybersecurity leaders, Mario Duarte (former VP of Security, Snowflake), Dr. Maohua Lu (Co-Founder & CTO, Veza) and Tarek Khaled (Field CTO, Veza), dive into data highlights and provide commentary from their years of practitioner’s experience.